Consulting Integrity
Read More: Consulting IntegrityConsulting with Integrity is critically important in my industry of Cyber Security, there are many consultants preaching to be what they are not, “knowledgeable” people. The Cyber security industry is fully of vendors and sellers trying to position security tooling as a solution to a cyber risk problem. I want to share a recent story…
A picture is not always worth a thousand words
Read More: A picture is not always worth a thousand wordsA picture is not always worth a thousand words, cyber security vendors please take note Question: When is a picture NOT worth a thousand words? Answer: When it has no context Just like my photo, it has no context and therefore would by of little interest to anyone who wasn’t on the same trail with me…
From Backup to resilient cyber security
Read More: From Backup to resilient cyber securityIn the Beginning From Backup to resilient cyber security: Best practises for Information Technology such as “Least privilege access”, “Admin account segregation”, “Operating system patching”, “Multi-factor authentication”, even “Patching and updating applications” have been around for many years, undertaken as ritual by many Information Technology departments within businesses across Australia as best practise maintainence, without…
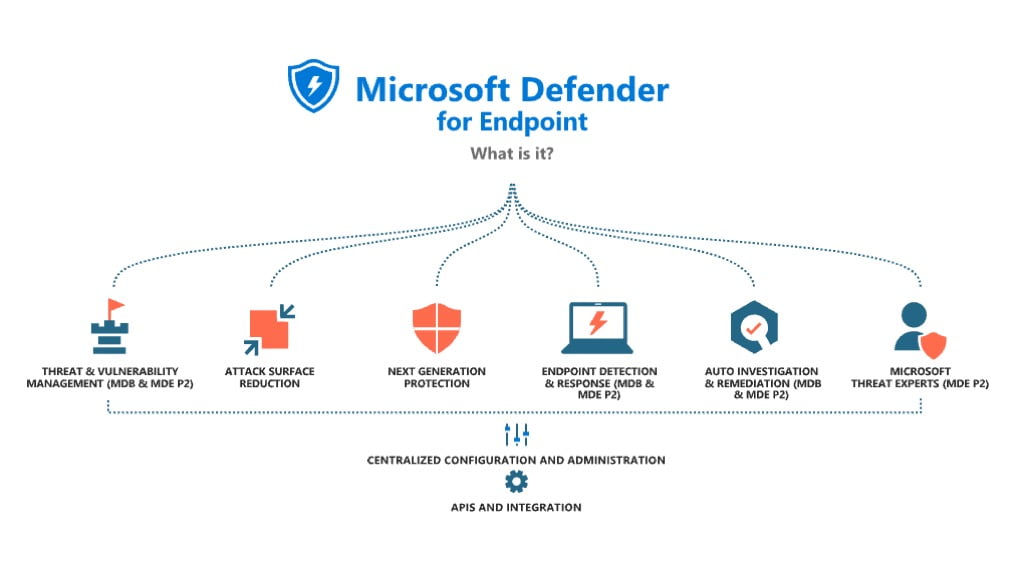
Four actions for protection with Microsoft Defender for Endpoint
Read More: Four actions for protection with Microsoft Defender for EndpointFour actions for protection with Defender for Endpoint: Originally written by myself for Crayon and sharing here to help other organisations move past Endpoint Detection and response into preventative technologies to improve your security posture. Introduction Often I am asked the question, “Why should I use Defender for Endpoint, I use product ‘X’ and Product…
CVE-2023-23397: Microsoft outlook vuln
Read More: CVE-2023-23397: Microsoft outlook vulnCVE-2023-23397: Microsoft Outlook Vuln: elevation of privilege vulnerability leads to NTLM credential theft: Very quick and short post today, I have already been contacted today around mitigations for this vulnerability and wanted to get some quick steps out early incase your business is unsure how to check whether you are at risk. My post assumes…
101: Basic Security Posture for WordPress
Read More: 101: Basic Security Posture for WordPress101: Basic Security Posture for WordPress, WordPress is one of the most popular internet technologies in use today, as a tool for amateur and professionals wanting to blog, to sell, to consult or to do almost anything else, nothing comes close to the WordPress ecosystem for flexibility and extensibility – want to build a store…
101: Introducing Microsoft Defender for Endpoint
Read More: 101: Introducing Microsoft Defender for Endpoint101: Introducing Microsoft Defender for Endpoint, one of my favourite role functions is to talk with customers about Microsoft security, of course I like to speak about security in general as well but Microsoft do a really great job covering 80% of what organisations need from a cyber security perspective so I almost always start…
Microsoft Sentinel – reducing spend and log complexity first
Read More: Microsoft Sentinel – reducing spend and log complexity firstMicrosoft Sentinel – reducing spend and log complexity first, Microsoft sentinel is one of the easiest SIEM platforms to switch on and be usable without configuration. But the devil is in the details of what should be configured to ensure that the signal data being ingested is most useful, minimally duplicated and at the lowest…
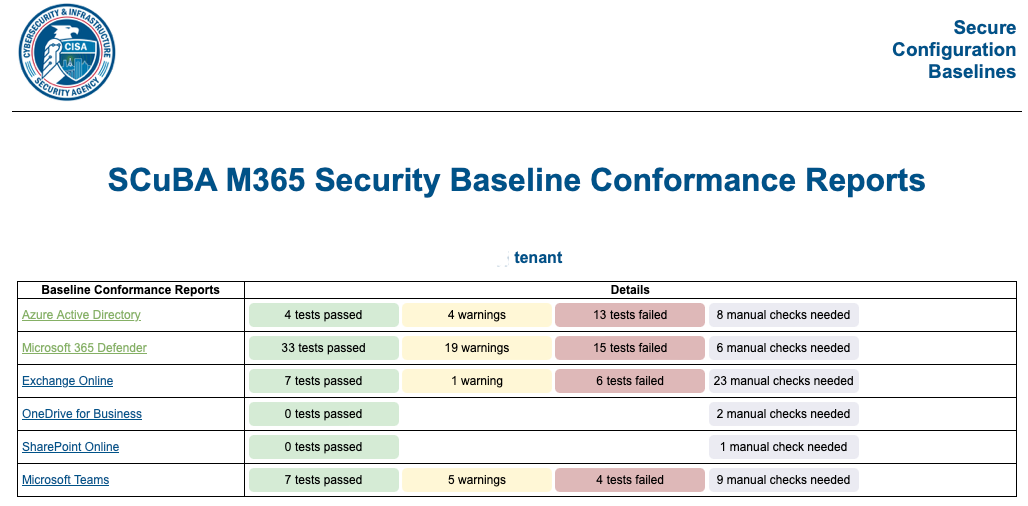
Secure Cloud Business Applications – assess your security
Read More: Secure Cloud Business Applications – assess your securitySecure Cloud Business Applications, assess your security – Best of all it is at no cost and provides guidance on best practise security guidelines for business. When reducing the likelihood of a successful cyber attack we need to break down the approach into various elements, a security assessment such as the CISA SCUBA tool is…
Protecting Australian Business from Cyber Crime
Read More: Protecting Australian Business from Cyber CrimeProtecting Australian Business from Cyber Crime, easy title to write and a topic beyond complex to implement for many small to mid sized businesses in 2022, Australia. The secret is that it is not complex to get started on a cyber security journey, it is easy to do the basics and reduce the risk of…