101: Introducing Microsoft Defender for Endpoint, one of my favourite role functions is to talk with customers about Microsoft security, of course I like to speak about security in general as well but Microsoft do a really great job covering 80% of what organisations need from a cyber security perspective so I almost always start with that.
This week I was fortunate to speak with Microsoft customers about what Microsoft Defender for Endpoint is and what it does at a 101 level.

On behalf of my employer Crayon, I presented around “Advanced Endpoint Security” – please read the follow with a slightly kiwi accent to experience what the audience felt 🙂
The Security Challenge

The problem with traditional Endpoint security is that it is complex to manage.
- Identities are the modern network perimeter and actively targeted by cyber criminals – devices are the connection point for an identity
- It is complex to deal with all the number of devices and device types across a corporate network
- There is huge difficulty in managing the telemetry / signal data being generated by 100s to 1000s of devices
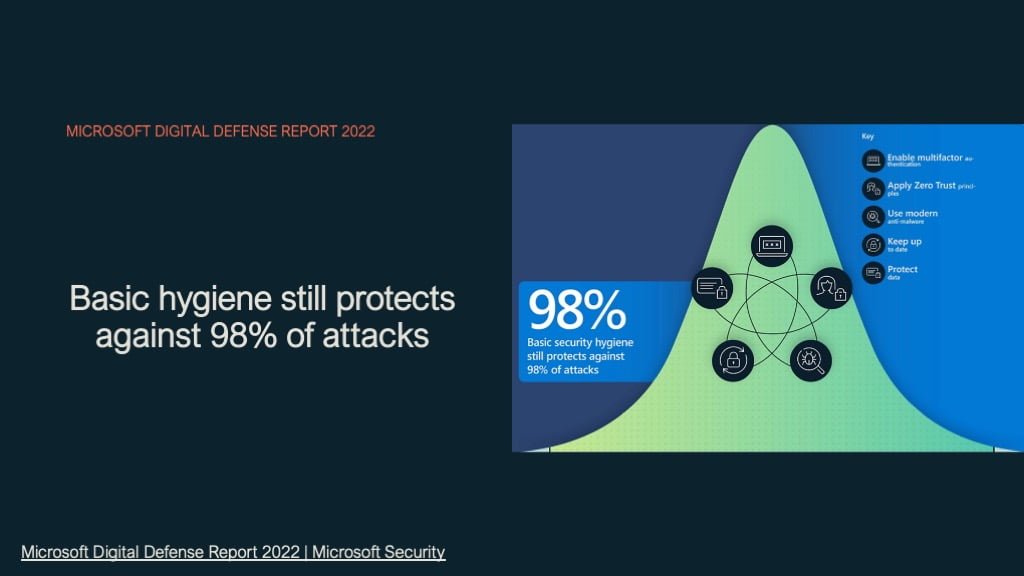
Yet one of the most effective ways to protect your business or your partners business is basic security hygiene and Microsoft for Endpoint provides very good protection across a significant attack vector.
- Enable MFA
- Utilise a Cyber security Framework like Zero Trust
- Use modern anti-malware
- Keep upto date
- Protect data
The one thing I would like everyone to take away from my presentation today is that being secure is about simply improving all the time on where you are currently from a security baseline point of view.
Microsoft assist immensely in lifting security posture for organisations as Microsoft provides protection across the Zero Trust network architecture with capabilities that can assist in any areas and integrating deeply providing automation and remediation at levels impossible with the traditional individual products from a multiple vendor cyber security approach.
Defender for endpoint editions

Defender for Endpoint is not the same as Windows Defender for NGAV, Defender for Endpoint can be thought of as endpoint security plus for: Windows, Mac, iOS, Android, Linux and servers (on-premise and cloud, AWS EC2 and GC)
Defender for Endpoint P1, provides a good baseline security posture and integrating into Defender for 365 for full environment visibility
Defender for Business, for less than 300 seat organisations provides you with MDE P1 as well as EDR and Threat and Vulnerability management and automated response,
Defender for Endpoint P2, is everything an organization needs for Endpoint security across Windows, Mac, iOS, Android, Linux ands servers and includes EDR, threat and Vulnerability Management as well as Microsoft Threat expert assistance.
What is defender for Endpoint?
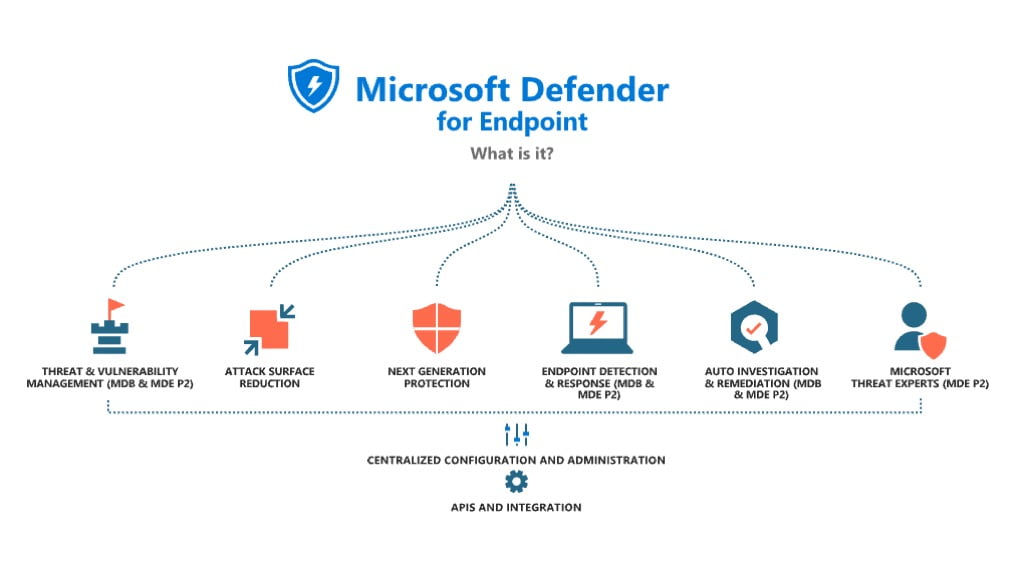
Microsoft Defender for Endpoint is a complete Endpoint security solution for all sizes of business from 10s of users to 10s of thousands and beyond across these areas:
- Threat and vulnerability management
- Attack surface reduction
- Next generation Anti virus
- Endpoint Detection and response
- Auto investigation and remediation
- Microsoft Threat experts
And with cyber security the MOST important aspect of all is to ensure that the organisation can automate and repeat processes as much as possible as prescribed by the Zero trust framework because this ensures that your assets are always secure, Microsoft Defender for Endpoint does this through integrations via M365 defender and utilises the Graph API for automation and consistency.
Threat and vulnerability management
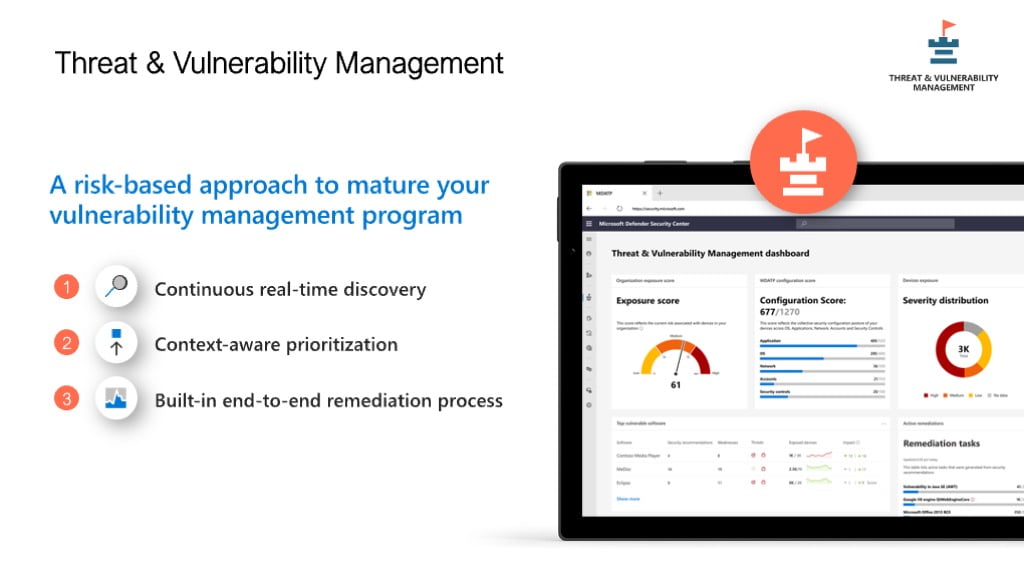
Good security posture requires knowing what vulnerabilities exist within your organisation, then the next steps from here are to know whether these vulnerabilities can be exploited, how easily it can be exploited (where is the device) and how many devices are vulnerable to this exploit.
Threat and vulnerability management is like having an internal penetration testing process set up and running all the time, your organization improves its security posture by knowing what discovered exploits could affect you, giving you the means to patch vulnerable systems and plan for removal of software etc that should not be running.
TVM looks for:
-Operating systems mis-configurations vulnerable versions
-App misconfigurations, versions etc
-Account misconfigurations
-Network issues
Defender TVM helps you know what is happening and what needs to be patched / mitigated in what order therefore increasing your overall security
Attack surface reduction
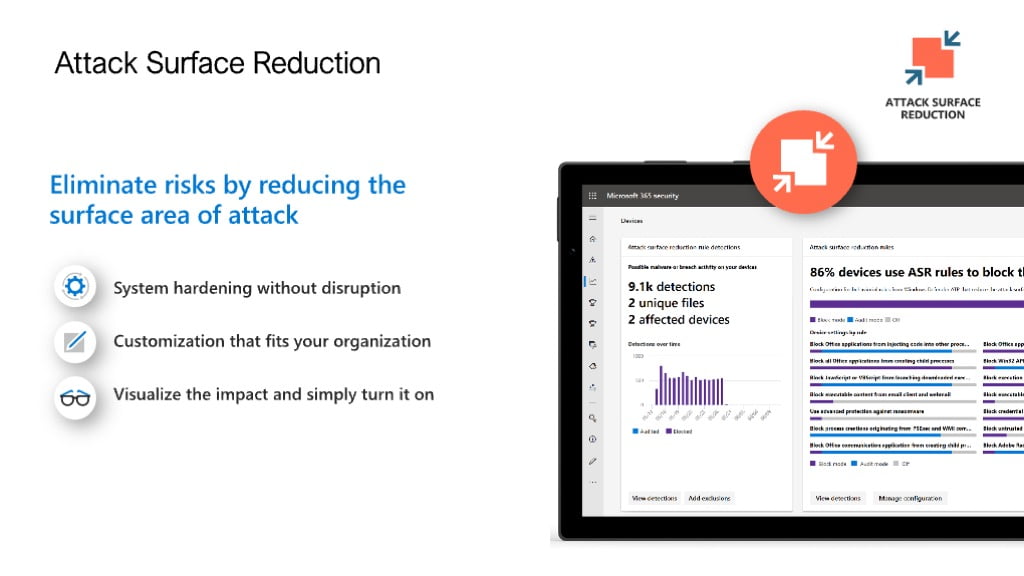
Zero day exploits I am sure you are all familiar with? When a new attack vector is exposed such as what happened with Folina in 2022, Anti virus and EDR tools in the majority did not detect Follina.
This makes sense as the Zero day had never been seen before, Machine learning training models used by endpoint protection tools need to have ‘seen’ an exploit before before they can block.
This is where Microsoft Defender for Endpoint has a big advantage over third party Endpoint solutions because ASR removes the attack vector for the exploit.
For example if 95% of your employees do not ever run Office macros then disable these from running.
Another example, Only allow trusted applications to execute because if malware.exe is downloaded to a workstation then it can not execute then it can not start its nefarious purpose of exfiltration data, scraping the local credential store etc.
Important Note: Attack surface reduction rules have the largest impact on limiting the affect of a possible attack but they also have potential to cause problems with user access so Microsoft provide audit and warn capability to allow testing of the rules and full reporting in M365 Defender on what rules would be triggered with configured ASR rules.
Recommendation: Set up ASR rules in audit mode, check the triggering of ASR rules in M365 Defender before implementing in block mode.
next generation anti Virus
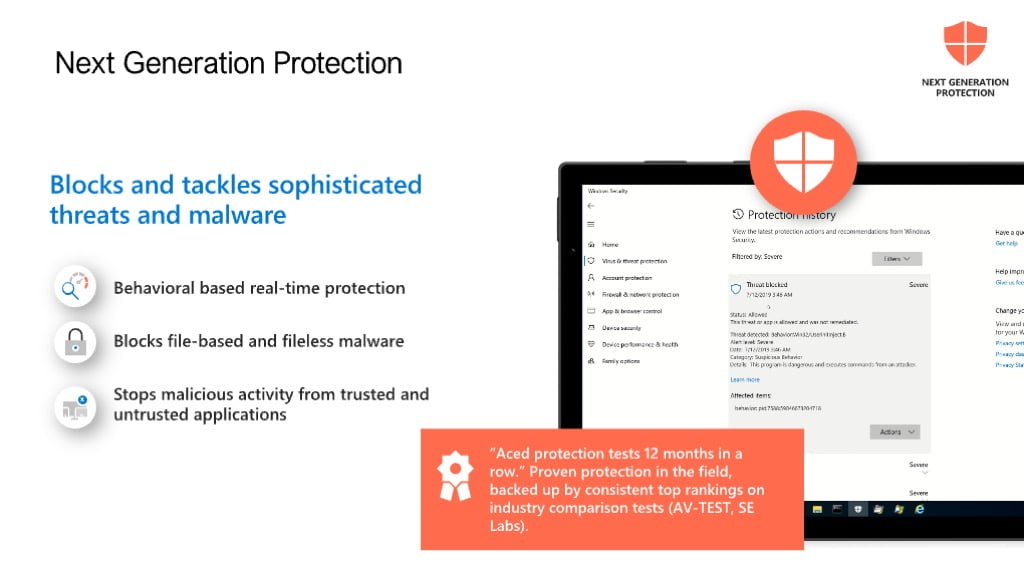
Next generation Antivirus goes past traditional signature based Anti Virus, now organisations are facing fileless malware, software that may perform “unusual activities” that are suspect but that would not be picked up by a signature based Antivirus solution.
Note: When configuring your Signature update frequencies make these frequent, the minimum is hourly and there is a lot of value in ensuring that all your devices are as upto date as possible.
Recommendation: Configure the minimal number of folder/file exclusions possible, ideally use file level exclusions as attackers will try to use folders excluded from malware scanning.
Also enable Tamper protection to minimize the potential for a malicious attacker to stop your NGAV/EDR service.
Remember that Defender for Endpoint is already installed on Windows 10 and 11 devices and will start operating if the third party NGAV is removed, this makes deploying MDE very easy – just create a policy and remove your other EDR/AV.
Endpoint detection and response
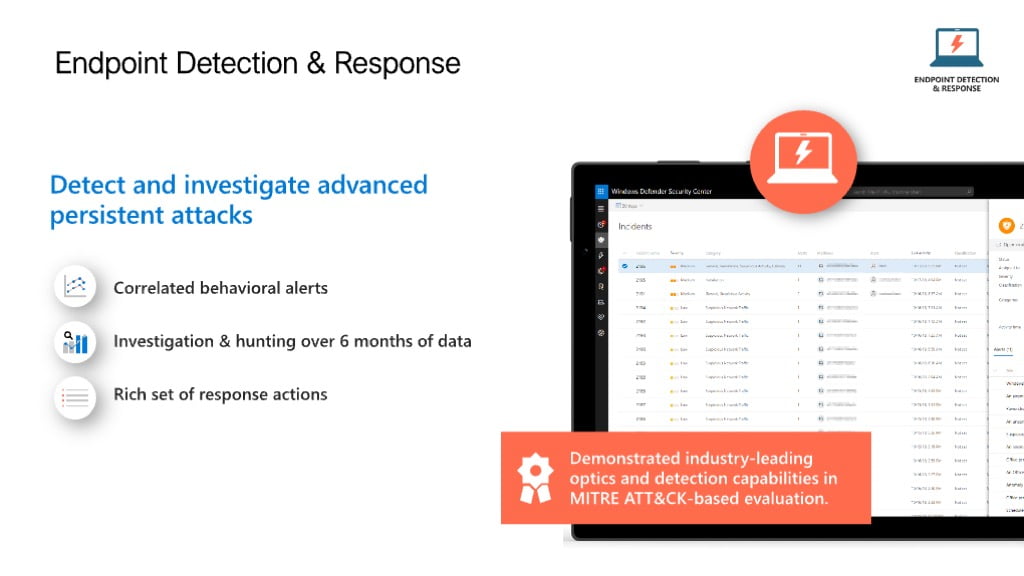
My personal favorite part of Defender for Endpoint is Endpoint Detection and response or EDR. This is where we look at the behaviour of users actions on a device or multiple devices rather than individual signals to determine that there may be indicators of compromise running on the corporate network.
Maybe it is a powershell instance started and several commands run that connect to other devices or that use alternative credentials not used on this workstation previously, these may be indicators of Compromise or they may be legitimate, and it is EDRs job is to determine what is legitimate and what is not.
EDR helps with the determining whether actions are legit or are a part of an attack or otherwise, EDR is not magic but it vastly improves value from the signal data being logged on the workstations across your network by expanding the visibility from one endpoint to multiple endpoints.
If you have a license for MDE P2 or MDB but are using another EDR then make sure to still enable your Microsoft EDR policy in Block mode as this gives you two layers of protection from Advanced threats. Defender for Endpoint is already installed so it does not require any other changes.
Auto investigation and Remediation
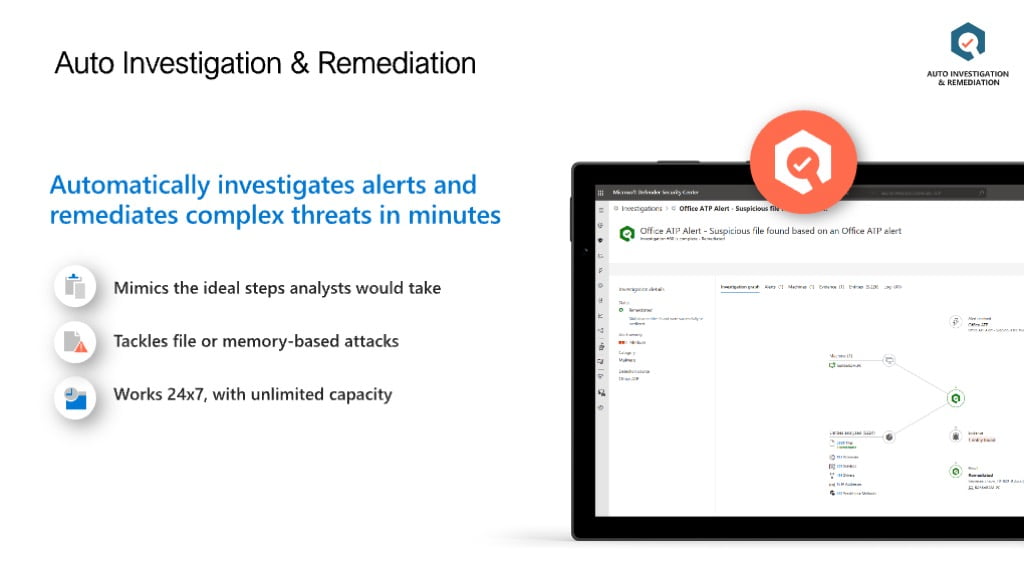
In the industry we are all aware of the concept of False positives (telemetry detections that are false) and False Negatives (no detection of a real incident), in each of these cases we are either tuning our detection software to minimize the erroneous alarms while still trying to catch all the real events, there is a very risky balance here between a failed detection due to tuning the alerts down or too many alerts for our SOC team.
Microsoft Defender for Endpoint Auto investigation and remediation or AIR is designed to augment your security teams capabilities. AIR looks for indicators and remediates these based on your configured settings from “do nothing” (not recommended) through to “Full – remediate threats automatically” (on by default).
AIR helps to reduce the time spent by your security team to investigate all security alerts by automatically handling known malicious events and activities and taking the appropriate actions to stop them, the true power of Microsoft XDR comes in here if you are using Microsoft Defender for 365, Microsoft Defender for Cloud Apps, Microsoft Defender for Office 365 then remediation can work across multiple attack vectors for example: Email, office docs, Cloud security to act on indicators of compromise across multiple ingress points.
An example of this would be, an email received by 10 employees with a malware payload, the link is clicked on by a single employee, using AIR and the XDR capability above might mean that MDE P2 blocks and deletes the malware and quarantines the machine, Defender for O365 removes the malware containing email from all 10 employees and Microsoft Defender for cloud apps blocks the C2 server that the malware was connecting to, this demonstrates what can be done with real integration between platforms.
This feature is available in MDE P2 and a subset is available in Microsoft Defender for Business.
Endpoint attack notifications
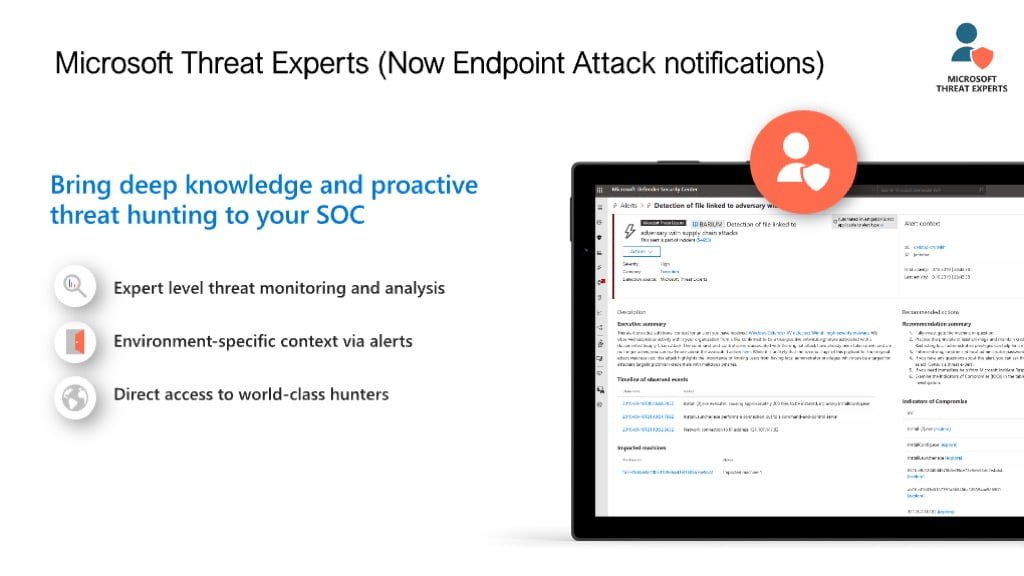
Microsoft Threat experts is included with MDE P2 though check with your account manager on eligibility. Microsoft threat experts is like your own threat hunting service when your team can ask for help with various detections or alerts that may have occurred and obtain additional details back from Microsoft related to the incident or discovery.
These questions might be related to an alert generated that you don’t have an explanation for, such as:
We detected a phishing email that delivered a malicious Word document to a user. The malicious Word document caused a series of suspicious events, which triggered multiple Endpoint Attack Notifications alerts for Follina malware. Do you have any information on this malware? If yes, can you send me a link?
I recently saw a Twitter post about a threat that is targeting my industry. Can you help me understand what protection Defender for Endpoint provides against this threat actor?
Defender for Endpoint in a Zero trust world

In a zero trust world where does Microsoft Defender for Endpoint assist your business in having a more secure posture?
First off there is no Zero Trust product or vendor, Zero trust is a framework based on principles:
- Good governance
- provide guardrails and automation
- security controls
- Technology
There are many Microsoft architecture documents that cover Zero trust and best practise so this is just a basic example, the box above illustrates where in a Zero trust Architecture MDE can assist your business to improve your security posture through the ZT principles of Always verify, Least privilege and Assume breach.
Specifically MDE provides rich signal data to show indicators of compromise from the devices connecting to your environment – MDE does this through providing the Visibility and Analytics as well as the automation to restrict the extent of an attack.
defender for endpoint > Microsoft XDR
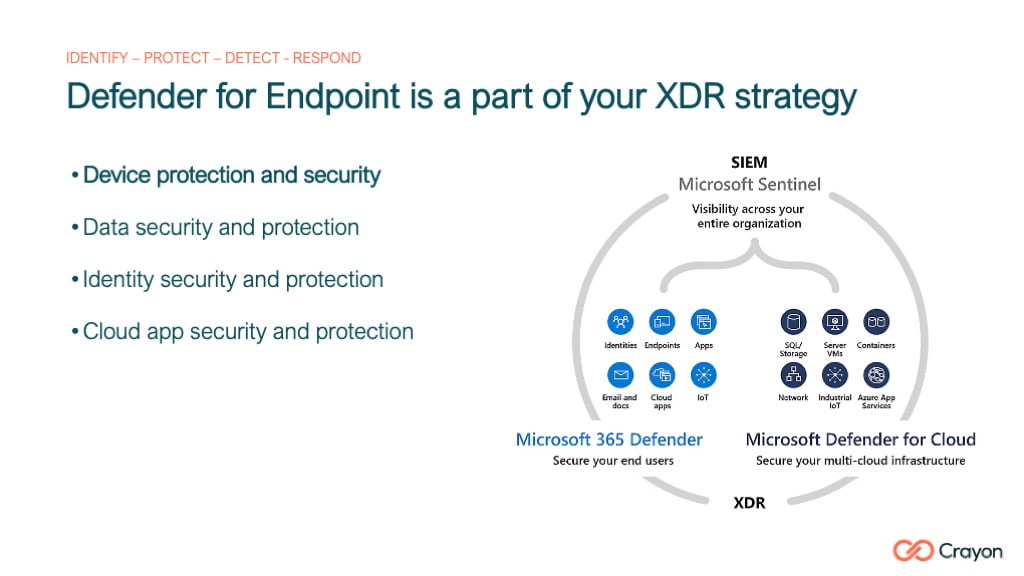
MDE forms a part of your Xtended detection and response capability (XDR) and from a Zero Trust perspective Microsoft MDE enables your org to prevent a breach from occurring in the first instance:
- Identify vulnerable software and exploited software running on devices across the enterprise
- Next gen Anti virus, blocks the known knowns
- Attack surface reduction rules, blocks the unknowns – the attacks never seen before
- Endpoint Detection and response, uses Machine learning to identify activity that is suspect based on Microsofts 43 trillion signals processed daily
- Tamper protection, stop the attack from disabling protection
- Respond automatically to known attacks and reduce the load on your security team through automation
- Detect and alert when an indicator of Compromise is discovered on your network (MDE P2) using Microsoft threat experts
Typical deployment

Crayon works with customers across Asia Pacific to implement Microsoft Defender for Endpoint using Crayon Accelerators to speed up the deployment of MDE but to also ensure that companies can maintain a strong security posture by providing automation and guardrails to ensure that your MDE configurations do not regress.
The above is a sample deployment example but the main thing to remember with Microsoft Defender for Endpoint is that it is already installed on your windows 10 and windows 11 devices, implementing it is as simple as setting a policy in Security centre and removing your third party EDR solution.
Summary
My hope is that by sharing these presentations I can help to highlight and explain the reasons for both solutions and frameworks and help to educate individuals and organisations on the best ways to protect your assets.
As always please reach out to me here if I can assist in anyway.






Leave a Reply