Four actions for protection with Defender for Endpoint:
Originally written by myself for Crayon and sharing here to help other organisations move past Endpoint Detection and response into preventative technologies to improve your security posture.
Introduction
Often I am asked the question, “Why should I use Defender for Endpoint, I use product ‘X’ and Product ‘X’ is the best endpoint detection and response platform in the market”.
My answer to this very valid question is the following, as in my mind this statement needs to be further broken down:
- Product ‘X’ performs detection of breaches and it assists in the response to breach across my endpoints and devices.
Marketing claims of breach minimisation (even elimination) by security vendors is commonplace, I know! I have succumbed to marketecture many times to the detriment of my bank balance – albeit at a much smaller scale personally.
Intentionally, most endpoint detection and response marketing avoids the most critical aspect of cyber security, that is protection and prevention in the first instance, as this is much more impactful to your cyber security program than endpoint detection and response can ever be.
- This is where I place the unsung hero, the real protector of the device (Windows, MacOS, iOS, Android and Linux), the scruffy school yard kid who stops the bullies before they get a chance to cause a problem – but does this “so quietly” that no one even noticed because the breach didn’t happen at all, this “Protector of businesses” being Microsoft Defender for Endpoint.
To my mind there is only one option that should be considered, that is to protect and prevent a cyber attack in the first instance, if that process / solution can also detect and respond to an attack then my organisation already has the best Endpoint security coverage available, not just the ability to detect a problem that might be occurring but to protect my devices before a potential problem can take hold and ransom my business operations.
The One, Two Knock Out punch
Introducing Microsoft Defender for Endpoint (Plan 1, Plan 2 and Defender for Business), an endpoint protection platform from Microsoft as the “One” in a One, Two Knock out punch.
There is a second ‘punch’ being Microsoft Endpoint Manager (formally known as Intune and now known as Intune again!) which is the best way to deploy Defender for Endpoint, but for the sake of brevity I can not cover MEM in this article.
Protecting and prevention of cyber attack is where MDE shines bright, being great at detection is one thing, but being able to prevent the attack in the first place is better than any detection capability by any vendor.
Defender for Endpoint specialises in what is most important to your business, that is providing you with a prevention first approach and then detection and response in those cases where Prevention falls short of complete protection from an attack.
Prevention and protection is possible with Defender for Endpoint because of the tight integration into the Microsoft platform (OS and Applications) – the best protection comes from knowing the platform intimately which is why Microsoft Defender for Endpoint performs so well.
An example would be the recent Folina Zero Day vulnerability where an Attack surface Reduction rule to block Office applications from creating child processes would have prevented Follina from being able to execute, without the application even being aware of what is happening – reducing attack surface is about minimising the options available to malware creators and locking the device down as much as is possible.
When Follina was discovered in May 2022 most endpoint detection and response platforms were completely unaware of this attack, this vulnerability had never been seen before and endpoint detection and response platforms did not have knowledge of its methods or its attack path, afterall Follina appeared to be a valid action performed via Microsofts own MSDT tool to almost any Endpoint detection software in use.
Follina and the next Follina are why attack surface reduction rules are so important, zero day attacks are damaging because they rely on being the first malicious explorer to target a new vulnerability.
Attack surface reduction provides mitigation through removing the opportunity for a new piece of malware, the next Follina to perform its malicious task.
NOTE: Attack Surface reduction technologies do not prevent breaches in isolation, they
are another layer in your security stack to reduce the likelihood of an attack being successful.
Microsoft Defender for Endpoint | M365 Maps
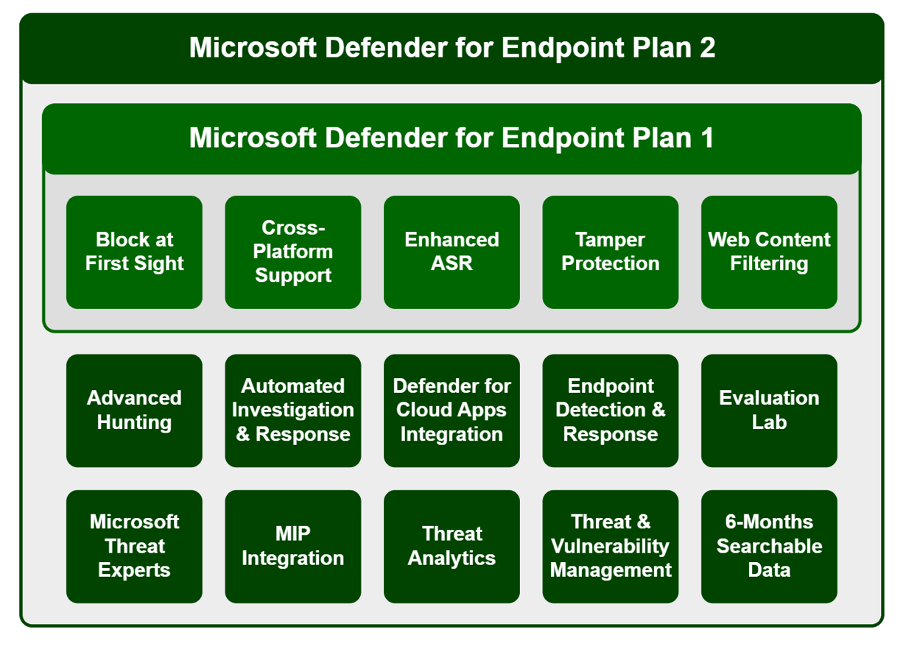
Protection is always better than cure, MDEP2 provides several specific capabilities to enhance an organisations security pre-breach, including:
- Enhanced ASR
- Threat and vulnerability management
- Block at First site
- Web content filtering
- Integrated into Defender 365, security.microsoft.com and Microsoft Secure score for near real time assessment.
Assuming you have already implemented MDEP2 (if you haven’t feel free to contact us) and enabled integration with the Microsoft Security centre, do these things for the greatest protection as rapidly as possible.
- Become familiar with the reports available within Defender 365 where related to devices: https://security.microsoft.com/securityreports
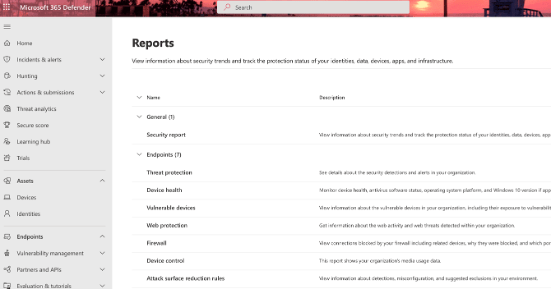
- Check the Device and Sensor health status regularly, Advanced persistent threat actors often disable protection/detection capabilities as a first step to compromising a network so make sure you always know whether all devices are being protected: https://security.microsoft.com/devicehealth
- Implement an Attack surface reduction policy in “audit mode”, Crayon can help with the scripts to make this easier or use what ever method you currently rely on to set up and configure a rule.
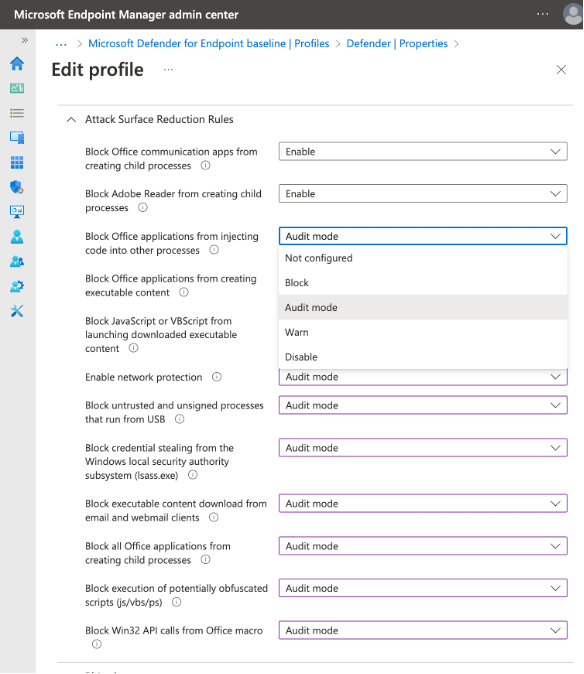
Once the policy is set apply to all users and devices and monitor for 30 days at least to determine which Attack surface reduction rules would be triggered on which devices for what users and investigate / create exceptions where necessary for those power users who need Office Macros – at least ensure they can only run from specified trusted locations.
To help you implement ASR rules, use the reports Microsoft have provided: https://security.microsoft.com/asrto determine which ASR mitigations would be triggered on workstations by what policies.
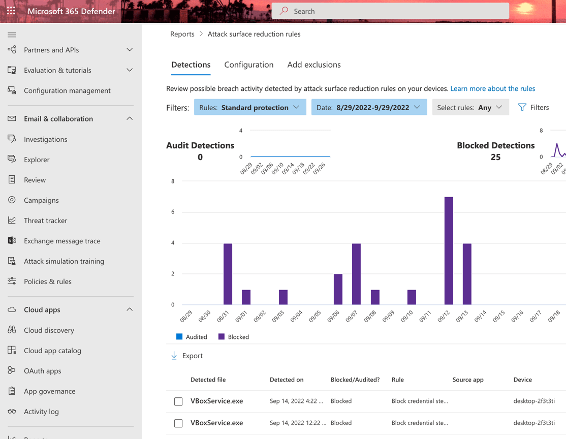
- Use Azure Active Directory groups to create groups for exclusion from ASR rules and apply for users who must have access to these capabilities and then apply the ASR policy in either Warn or Block mode.
- Warn is the most “friendly” configuration in that a user triggering an ASR will be asked to confirm that they want to continue the current operation.
Summary
Relying on traditional Endpoint Protection to detect a breach is rather like watching a burglar run from your house with your new OLED screen, the goal should be to stop the criminal disconnecting the TV from the wall, or even better preventing entry in the first instance.
Attack Surface reduction rules are simply one way in which you can improve device security with very little impact to normal users, while reducing the threat from “Zero Day” attacks substantially by minimising possible exposed vulnerabilities.
Ensure simple but effective mitigations for protecting devices like Attack surface reduction rules, are in place to minimise the likelihood of a cyber attack leading to a breach or compromise.
It may take some learning to fully leverage but it is worth spending the time to understand MDEP2 fully as it goes beyond Endpoint protection.
Please reach out if I can assist you with any of the above here.
Microsoft Confirms Exploitation of ‘Follina’ Zero-Day Vulnerability | SecurityWeek.Com
Guidance for CVE-2022-30190 Microsoft Support Diagnostic Tool Vulnerability – Microsoft Security Response Center






Leave a Reply