Microsoft Sentinel – reducing spend and log complexity first, Microsoft sentinel is one of the easiest SIEM platforms to switch on and be usable without configuration. But the devil is in the details of what should be configured to ensure that the signal data being ingested is most useful, minimally duplicated and at the lowest cost, starting from free for certain data types including M365 signal data using the connector and from other Microsoft platforms there may be an inclusion, such as Microsoft Defender for Endpoint Server P2 which has a 500MB daily ingress allowance.
Introduction
Recently I became involved with an MSP who had a significant overspend with Sentinel due to their decision to process all Firewall logging data, so I have prepared the following as a quick 5 minute read on what to look out for and what you can do to minimise your Microsoft sentinel spend, or at least have no surprises.
In this example of importing Firewall data, what is it that you need to collect? think about this in your own context, you will have other resources capturing the same data so before forwarding all log data, consider what is actually needed and what is miscellaneous and unnecessary.
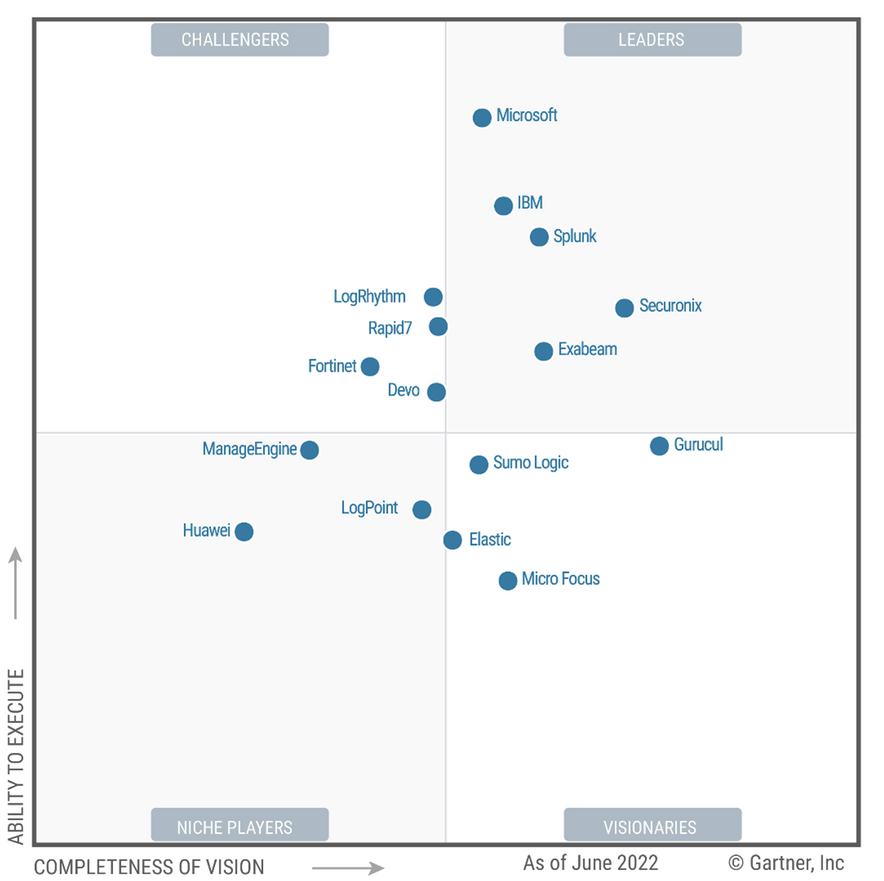
Microsoft Sentinel has rapidly improved and is now a leader in the Gartner magic quadrant for Security Information and Event Management, further information is linked here. Sentinel makes it relatively easy for organisations to ventrally store and manage their signal data.
There is a problem with Microsoft Sentinel
With great power there are always negatives to be considered and with Microsoft Sentinel this is no difference, left to its own devices, ingress of all of an organisations signal data is going to lead to a couple of bigger issues in the future.
- Where to start looking, too much data leads to event overload, duplication of signals, telemetry all over the place and difficulty in making heads nor tails of what needs to be visualised.
- Storage overload and cost blow-outs, this is a significant challenge for any cloud platform. Knowing the implications of switching on features and functions without having historical data to reference is a budget blowout/catastrophe waiting to happen.
The solution
As with much of the Microsoft Azure/M365 suite there are many ways to limit costs and I will cover a few of these today with the hope that it will assist in planning and setting up Sentinel for your organisation.
- Set up spending limits, set spend limits for every feature you use even outside of Microsoft Sentinel.
- Monitor Microsoft Sentinel use every day, at least every week and configure alerting
- Decide what data needs to be ingested, avoid duplication, Eric Mannon (an expert) explains here, Eric is a must follow for anyone involved with Microsoft Security.
- Log data is the most expensive and least filtered
- Utilise the Microsoft connectors whenever possible, from M365 Defender ideally for an M365 platform.
- Use the free ingest amounts provided by Microsoft as much as possible, 90 days for M365 data and more than adequate for a small to mid sized business without ISO 27001 log retention requirements.
- Utilise Azure storage or warm storage for signal data until it is needed for analysis, most often the SIEM is not going to be the first sign of an Indicator of Compromise, have the log data stored elsewhere incase it is needed for further review especially in the case where the log data requirement is for regulatory purposes rather than Threat Hunting.
- Decide whether pre-payment for consumption is more appropriate for your organisation as the savings can be large.
Some further resources:
The below links will assist in optimising your sentinel costs.
- Because Eric is so good I have to repeat: http://www.ericmannon.com/2022-12-06-Crafting-your-Microsoft-Sentinel-Ingest-Strategy/
- Charbel https://charbelnemnom.com/optimize-your-costs-in-microsoft-sentinel/
- Practical365 https://practical365.com/increase-microsoft-sentinel-cost-efficiency-with-log-analytics-capabilities/
Summary – Microsoft Sentinel
Microsoft sentinel is a very powerful platform for organisations to leverage as a threat hunting tool, the number of workbooks being created and shared by the community and cyber security vendors is ever growing and Sentinel has shown that it is as good as any of the traditional SIEM providers though if an On-premise (Software on your Hardware) SIEM is required then Microsoft Sentinel is not the right choice for your organisation, as Sentinel is Cloud Native and Cloud first.
Make sure that you check regularly your Sentinel spending and set low spending limits if you are evaluating the platform and larger spending limits if you are prepared to pay more for.
Updates
This Sentinel blog post will be updated with additional information on ways to save on Microsoft Sentinel spend. Therefore it will continue to be added to as new articles come to light.
30th December 2022, Morten Knudsen has a great blog post here on saving costs through excluding Syslog events from banned IPs, in Mortens example he cites a 43% cost saving.
Contact me
As always if I can assist further then please let me know here.




Leave a Reply