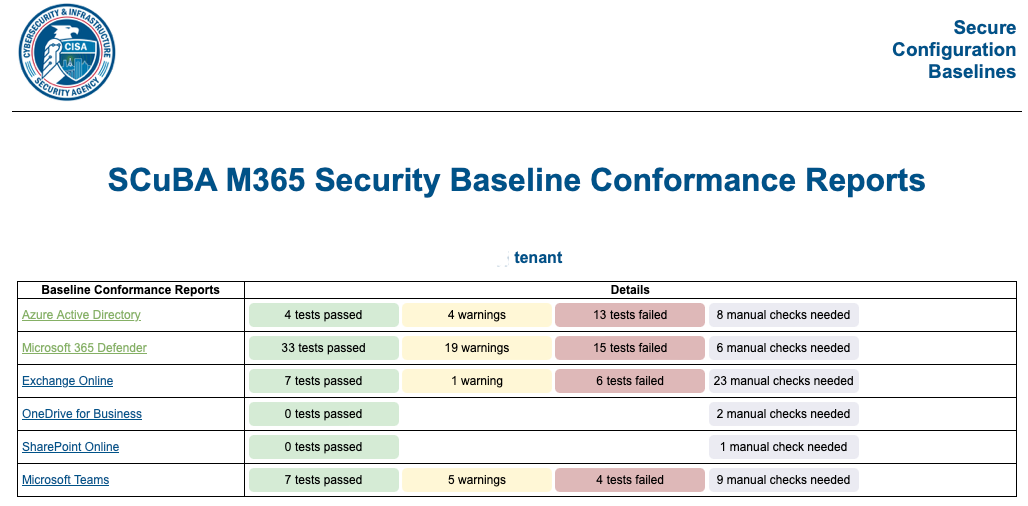
Secure Cloud Business Applications – assess your security
Read More: Secure Cloud Business Applications – assess your securitySecure Cloud Business Applications, assess your security – Best of all it is at no cost and provides guidance on best practise security guidelines for business. When reducing the likelihood of a successful cyber attack we need to break down the approach into various elements, a security assessment such as the CISA SCUBA tool is…
Michael Brooke presents the ASD essential 8 on Safari
Read More: Michael Brooke presents the ASD essential 8 on SafariMichael Brooke presents the ASD essential 8 on Safari; recently I had the opportunity to work with TechforGood, an organisation making a difference with Social organisations across Australia. I have two passions other than fishing and family (so four passions in total), these are: Cyber security, the field of cyber security is an industry where…
“Okta parses passwords in clear text”, What does that mean to me?
Read More: “Okta parses passwords in clear text”, What does that mean to me?“Okta parses passwords in clear text”, What does that mean to me? This is really NOT an Okta problem but an industry problem – my industry, cloud SSO authentication should always and only be against known “good” Authenticators such as Microsoft, Google, Apple and others for all cloud based SSO. Passwords should never be out…
Carrots, sticks and Donkeys do improve cyber security, part 1
Read More: Carrots, sticks and Donkeys do improve cyber security, part 1Carrots, sticks and donkeys do improve cyber security, part 1. More specifically how to Use the ACSC recommendations to achieve cyber resilience augmented with what organisations are already doing well today. As most organisations in Australia already understand, the Australian Signals directorate Essential Eight is a list of 8, easy (definitely easy) steps to implement…
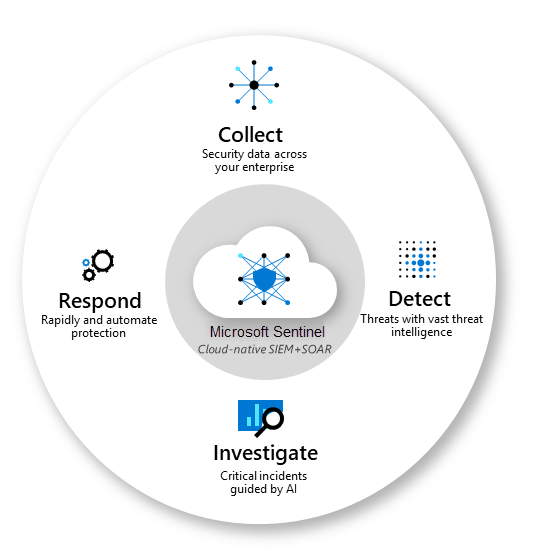
#1, Down and Dusty with Microsoft sentinel
Read More: #1, Down and Dusty with Microsoft sentinel#1, down and Dusty with Microsoft Sentinel. Sentinel is one of Microsofts Crown Jewels hidden so well in plain sight that many Managed Service Providers and cyber security teams do not even know it can help them significantly with investigating Indicators of Compromise or investigating a cyber attack to find the source and the target.…
The No.1 way to protect Data, Defender for Business and Premium
Read More: The No.1 way to protect Data, Defender for Business and PremiumThe No.1 way to protect Data, Defender for Business and Premium, MSP’s and businesses looking for better coverage of the ASD Essential 8 with the fewest possible products should look at Microsoft Defender for Business or Business Premium preferably. This morning a colleague (thanks Ross) sent me this article and it reminded me that we…
Threat Hunters, Hard job, tough to find too!
Read More: Threat Hunters, Hard job, tough to find too!Threat Hunters, Hard job, tough to find too! – the following article has been kindly shared with permission by GravityWall.net from an original article written on their website here. Employing good cyber security candidates is hard So many considerations: technical vs team fit vs ability to learn etc etc, I recently came across this very…
Easy Fail – Australian critical infrastructure
Read More: Easy Fail – Australian critical infrastructureThe Easy Fail in critical infrastructure should have all of us worried right now, whether it is the water being turned off, the traffic lighting systems that we all rely on to get around the cities we live in or much worse, the Electricity that we used to power our homes and provide us warmth…
Cyber Attack Vectors 2022; where marketing and reality diverge
Read More: Cyber Attack Vectors 2022; where marketing and reality divergeCyber Attack Vectors 2022; where marketing and reality diverge. The Identity Theft resource centre ‘Q1 2022 Data Breach Analysis’ report is an interesting 2022 report with a not surprising result to many cyber security professionals. Human Error is the number One source of cyber breach The number one attack vector “Cyber attack” is in-fact Human…
An Empirical Assessment of Endpoint Detection and Response Systems against Advanced Persistent Threats Attack Vectors
Read More: An Empirical Assessment of Endpoint Detection and Response Systems against Advanced Persistent Threats Attack VectorsAn Empirical Assessment of Endpoint Detection and Response Systems against Advanced Persistent Threats Attack Vectors. Recently I wrote about EDR failure to detect and respond to cases of Advanced Persistent Threats here after discovering a research paper on the topic when researching the use of Machine Learning in cyber security Detection and response solutions such…