Cyber Attack Vectors 2022; where marketing and reality diverge. The Identity Theft resource centre ‘Q1 2022 Data Breach Analysis’ report is an interesting 2022 report with a not surprising result to many cyber security professionals.
Human Error is the number One source of cyber breach
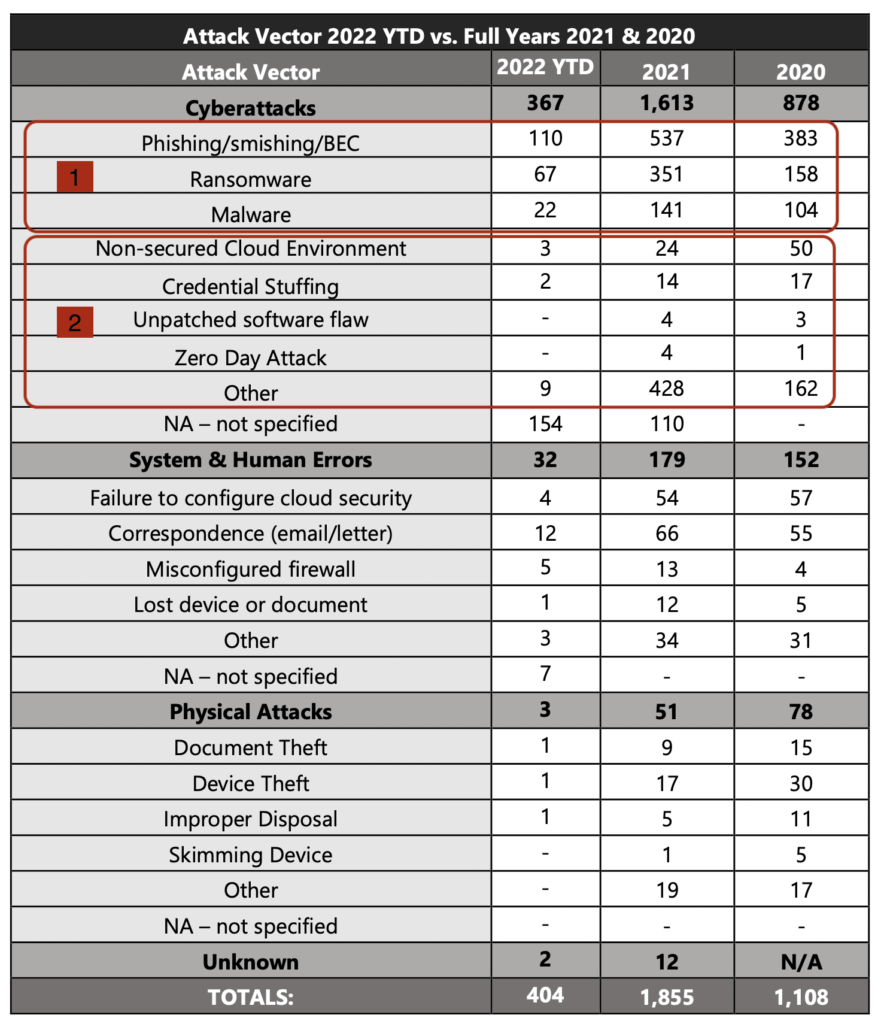
The number one attack vector “Cyber attack” is in-fact Human error causing cyber attack, even if the report does not portrait it in this light.
From the analysis of breaches for Q1 2022, the breakdown is as follows from 367 notified attacks:
- Human error sourced attacks consisted 199 notified breaches
- System or advanced cyber attack consisted of 5 notified breaches
There were a number of not specified, these could easily go into either bucket as they may be unknown or they may simply be “not disclosed”.
My summation of this data is that it is us as employees and fallible human beings still cause the vast majority of breaches to occur.
The “Attack Vectors 2022” report is from across the United States of America, meaning that from the 10’s of millions of businesses running in the USA, the percentage number of notified attacks is infinitesimally small, so small as to be exponentially less than your chance of winning the lottery! in fact not even close to winning a lottery.
Today you are ‘probably’ safe’ish
For the majority of organisations it means that the cyber security controls you have in place today (Q2 2022) are holding up against the attacks that are commonplace, today.
Tomorrow is a different story and as malicious actors gain techniques and technologies to assist them in their craft you will need to gain the edge in the real living game of”Cat and Mouse” against criminals looking for easy pickings or more recently with LAPSUS$ looking for notoriety and fame.
Safe’ish is not where any organisation wants to be. The unwavering advice I always have for clients is “never be at the back of the herd” you can click here for what this means.
Tomorrow
What you have today may be enough to keep the “wolf from the barn door”, but tomorrow is a different story.
Many of your cyber controls are good enough – or you have been lucky with cyber aware staff and Next generation Antivirus (NGAV) gets you so far, as does your other security controls in place on your systems. Your email service probably blocks 99% of malware email if using Microsoft Online for email or Google mail, but occasional malicious content will still get through.
Training is critical, all employees must be trained on what will and will not occur: E.g with Business Email Compromise (BEC), make all staff aware that money will never be requested via email alone.
- Put processes in place for this eventuality where a phone call to the recorded requestors mobile must back up the email request with a confirmation of account details, or better still eliminate this as a method of accessing capital.
Next steps
Do NOT to look for cyber security tools and do not have cyber security companies tell you what you need to do to be secure – just like buying a car because the dealer tells you there will be no more “deals” for the remainder of the year; be in control, be informed and work with a frame work approach, such as:
- ACSC Australian Signals Directorate Essential 8 – Ideally this if you are Australian. The remaining 30 odd controls are very important as well. I have a handy file I created here that I use with partners
- Center for Internet Security (CIS 18 controls)
- NIST CSF – The NIST CSF is detailed and can be quite complex for beginners
Many Managed Service Providers can assist with building a cyber security plan for your organisation following the many frameworks available and these frameworks put into perspective the most critical controls that your organisation must put into place to secure the: Indentities, Network, Applications and most importantly, your “Secret sauce” or Data.
Do these things as soon as possible
I speak with around 10 different Managed Service Providers and resellers every week and the most surprising thing is the number who report that most, if not all of their clients DO NOT use “Multifactor Authentication” or MFA, because it is too hard.
One MSP’s customer had been breached twice in a year and STILL thought MFA is too difficult. MFA is included with some cloud identity providers including Microsoft Online and Google Mail so there is no excuse not to implement the single most important way to limit the effect of stolen credentials.
- Implement Multi Factor authentication immediately (99.9% effective against stolen credentials)
- Train all your staff through regular activities and online phishing awareness testing
- Ensure you have Backups in 2-3 locations and that the backups work
- Implement a Strategy to Patch Operating systems and Applications within 48 hours
- Implement some form of Application control to prevent the spread of malware
Use the frameworks above to create your own Essential controls, as not all controls are needed for all businesses, except Multi Factor Authentication, every single business must implement this ASAP, unless you want to be the weakest animal in the herd.
The initial report is linked here: IDTheftCenter
Please contact us here if you would like further information or assistance with any cyber security questions.






Leave a Reply