Zero Trust vendor architecture: Ethical, or not ethical?
Read More: Zero Trust vendor architecture: Ethical, or not ethical?A vulnerability is disclosed in Palo Alto VPN hardware/software, the company who discovered this: Randori may not have disclosed this to the vendor in a timely fashion. The premise that is suggested for this, is that as Randori are a Red Teaming company they used this Vulnerability to infiltrate their clients who used Palo Alto…
No business too small to be a target for Cyber crime
Read More: No business too small to be a target for Cyber crimeSmall to Mid enterprise companies in Australia are extremely vulnerable to revenue disruption and most likely financial disaster from cyber breach – Auto parts importer lost $880k 2 months ago as an example, not the typical target for a cyber criminal, or is it? Yesterday in one Risk Intelligence report we ran for a client…
AV NGAV EDR XDR MDR AMDR
Read More: AV NGAV EDR XDR MDR AMDRThe cyber security landscape has seen huge expansion and growth in the past 5 years and End Point Detection and Response (EDR) has been one of the biggest areas of expansion. https://www.morphisec.com/hubfs/2020%20State%20of%20Endpoint%20Security%20Final.pdf According to Ponemon Institute, 68% of organisations suffered one or more endpoint attacks that successfully compromised data or IT Infrastructure. In 2018 Gartner…
Artificial Intelligence?
Read More: Artificial Intelligence?Artificial Intelligence is not always Artificial Intelligence, every Cyber Security vendor selling solutions today is either putting an “using AI” sticker on their website, or they are investigating how they can use Artificial Intelligence “AI” and Machine Learning “ML”in their branding. It stands to reason as the terms are well on the incline of the…
Data Incontinence – when leaks sneak out
CSF framework: 1. Identify; 2. Protect. Cyber Maturity Level:⭐️⭐️
Read More: Data Incontinence – when leaks sneak outTo prevent data being used against you in the future either through competitive, intellectual or malicious usage or publication? What should you do?
CSF framework: 1. Identify; 2. Protect. Cyber Maturity Level:⭐️⭐️
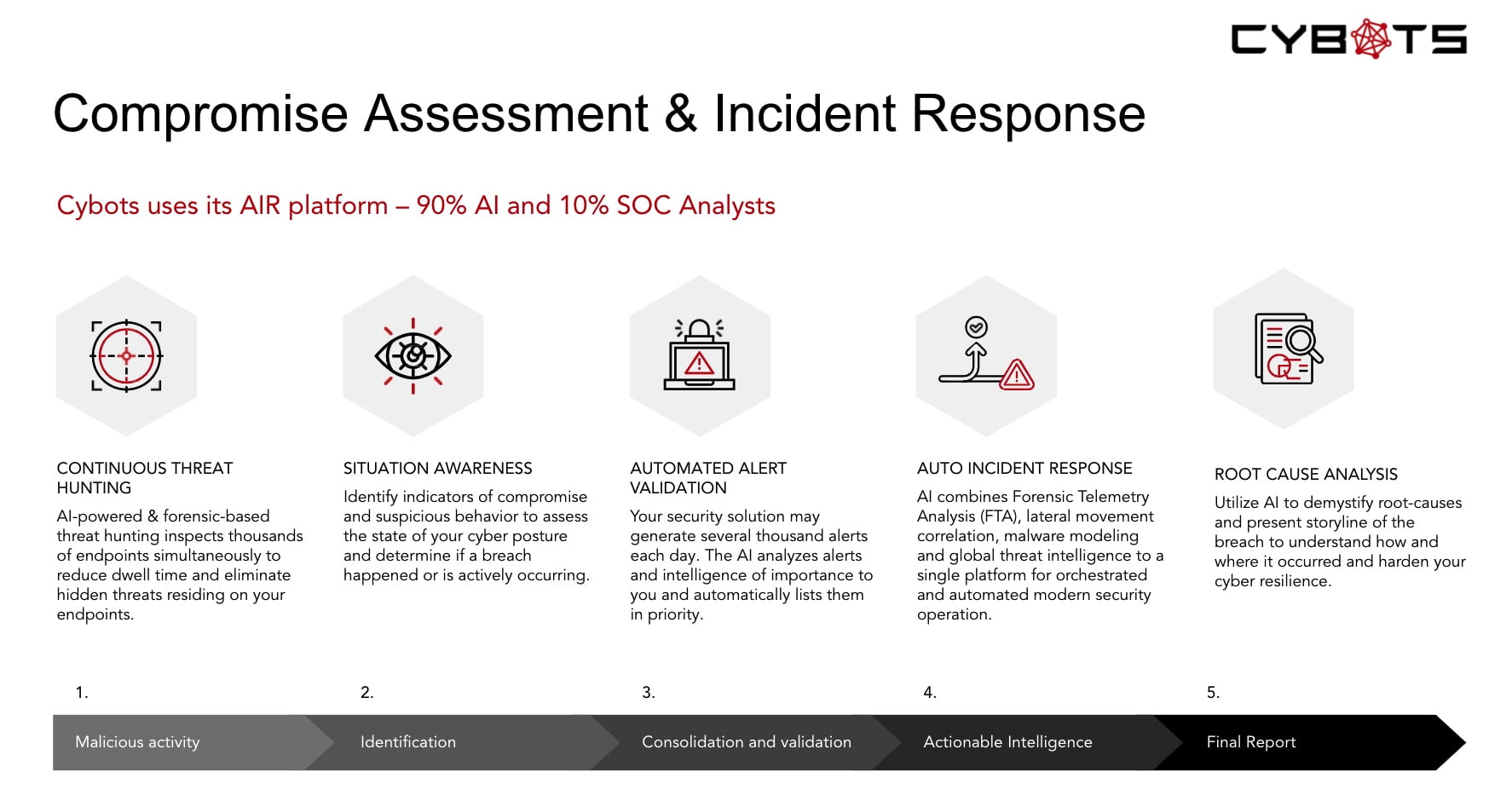
Managed Detection and Response (mdr)
CSF framework: 2. Protect; 3. Detect; 4. Respond. Cyber Maturity Level:⭐️⭐️⭐️
Read More: Managed Detection and Response (mdr)Detection and Response or the may be eXtended Detection and Response, this depends on the Solution provider of MDR. Newer solutions exist now termed as Advanced Managed Detection and Response which is a merging of MDR along with additional capabilities to provide advanced Detection and Response capabilities.
CSF framework: 2. Protect; 3. Detect; 4. Respond. Cyber Maturity Level:⭐️⭐️⭐️
Advanced Managed Detect Response (AMDR)
CSF framework: 2. Protect; 3. Detect; 4. Respond. Cyber Maturity Level:⭐️⭐️⭐️
Read More: Advanced Managed Detect Response (AMDR)MDR stands for is the next generation of cyber security Detect and Response solutions in the market to target breaches and other malicious activity, eXtended Detection and Response XDR stood for an extended range of detection capability (Network and other devices/ sources of data) and AMDR will take over where XDR lets go.
CSF framework: 2. Protect; 3. Detect; 4. Respond. Cyber Maturity Level:⭐️⭐️⭐️