The cyber security landscape has seen huge expansion and growth in the past 5 years and End Point Detection and Response (EDR) has been one of the biggest areas of expansion.
https://www.morphisec.com/hubfs/2020%20State%20of%20Endpoint%20Security%20Final.pdf
According to Ponemon Institute, 68% of organisations suffered one or more endpoint attacks that successfully compromised data or IT Infrastructure.
In 2018 Gartner had named EDR as a key capability for cyber security controls, by 2019 EDR was well on the way to becoming a Gartner product category by itself and leaving Antivirus behind as a legacy.
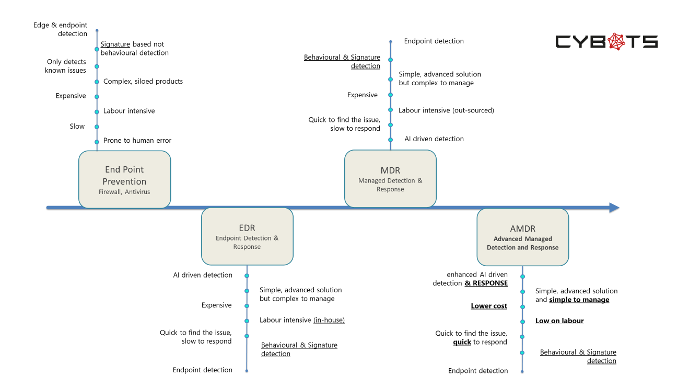
The Short journey from AV to AMDR
Extended Detection and Response
https://www.gartner.com/reviews/market/endpoint-detection-and-response-solutions
As cyber criminals evolved their methods of attack, standard AV is no longer able to cope with these modern attacks in any form, EDR has been the cyber security response.
Fundamentally EDR takes Anti Virus (AV), shakes it up, accelerating it beyond the end point as an isolated island to be protected. EDR achieves this by creating the context between what many Endpoints are detecting, correlating all of this data and finally cross checking all of this data against the vendors Threat Intelligence source to provide deeper insights to the potential attack in play based what is known from existing attacks and what is possibly unknown using User and Entity Behaviour Analytics (UEBA).
The Mitre Att&ck Framework (https://attack.mitre.org) was born specifically because cyber criminals are becoming more sophisticated in their attacks on organisations working easily around AV running on Desktops. Where an AV solution could detect a file that was MALWARE by known fingerprint via a virus definition or by suspicious behaviour, an AV solution alone was not adequate to detect an attack running potentially “normal” commands, moving laterally on the network, seeking reconnaissance, gaining access footholds on systems and ensuring persistence.
The end goal; obtaining the necessary privileged credentials to fully discover all assets and exfiltrate or encrypt data to exhort or sell on the Dark web for profit.
Thus, Cyber criminals had moved beyond the lone machine compromise, becoming more sophisticated. EDR rose and met this new challenge, EDR would not just look for malware on an end point, EDR could also determine that suspicious activity might be occurring on the network because it could accept multiple telemetry sources and correlate these as suspicious behaviour for a Security Operations expert to analyse and confirm or accept as OK.
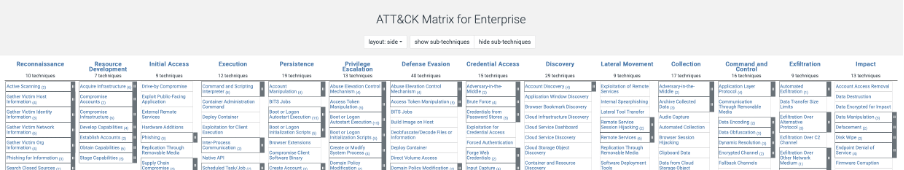
An AV solution can do very little to prevent a modern cyber attack where some or all of the above techniques are employed.
EDR as a solution should be a baseline for all organisations as it seems to be an essential control, so why is Extended Detection and Response not implemented as a Risk control for all Organisations who are beyond reactive cyber security?
As is often the case with software products, promise vs reality rarely match customer expectation or promise.
This is the reality of EDR, it is difficult and it is complex, each endpoint sending 1000s of Telemetry data points to a central collector, when taken across hundreds to thousands of endpoints; becomes hundreds of thousands to millions of events to be correlated every, single, day by security teams.
Millions of correlations are reduced to thousands by good EDR software, after configuration and tuning to remove “suspicious” activities that are infact innocent privilege escalations that occur every day on production IT infrastructure, or any of the myriad of normal day to day operations in a business.
Two options exist for the traditional EDR to manage the correlations, neither are ideal:
- Increase alert thresholds to reduce false negatives
- Increases false alarms
- Decrease alert thresholds to reduce false positives
- Increases possibility of missing real compromise
For large corporations where there is an operational Security Operations Centre (SOC) with Security Operations staff handling alerts 24/7, the problem may be manageable.
Managed Detection and Response (MDR) Providers are the next industry step in preventing Cyber Attacks.
Organisations of all sizes and scale have the same requirement to detect and respond to a cyber attack, an EDR solution is simply not able to be applied equally to all Organisations.
The requirements needed for monitoring and maintaining an EDR solution may not stack up with the expertise required to manage the alerting generated on a daily basis.
Further to this, an organisation may not have a desire or need to employ a team of security analysts or extend their SOC for the occasion when they are breached and need this expertise – on average less than once per year per organisation.
This is why Gartner have predicted that 50% of enterprise EDR customers will be using Managed Detection and Response providers by 2023.
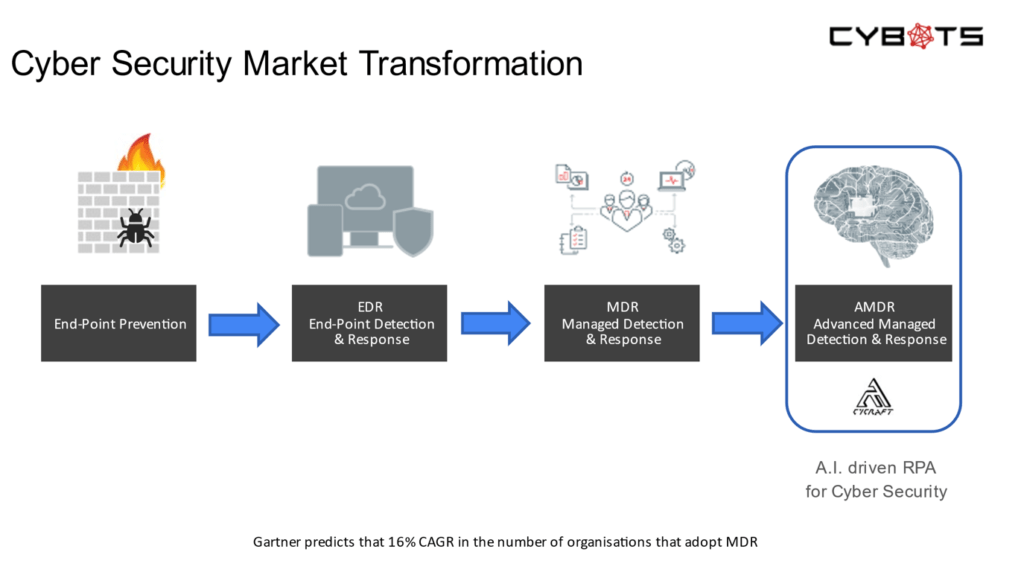
The primary difference between EDR and MDR is “provider” – MDR services provide an organisation with a service that provides all the correlation and threat intelligence , threat hunting and expert analysis for a businesses security needs.
MDR providers came into the main-stream because the cyber security industry is acutely aware that organisations understand the difficulty of EDR management for most businesses and that is that the promise does not match the reality.
Using MDR the businesses Cyber security Protection, Detection and Response is outsourced, therefore the business needs only be concerned with the running of their income generating functions, whilst having experts manage their cyber security.
There are problems with the MDR approach that makes the solution less than ideal for many organisations, including:
- What data is being collected from the EDR/XDR clients?
- If Personally identifiable, is data sovereignty an issue?
- How much data is being sent from the client to the MDR provider
- Is the scanning real time or scheduled
- Mean Time To Detect (MTTD)
- Slow because humans have to handle many clients
- Mean Time To Respond (MTTR)
- Slow because humans have to resolve issues across multiple clients
- Remediation Process
- What information does the MDR provider give the client
- What needs to be paid for separately
- Human operators have fatigue and False Positive issues, or mistakes
- Requires Administrative rights to all machines at the client site
MDR solutions are a viable proposition for customers who do not wish to implement EDR due to its overheads, complexity, requirement for Security personnel specialisations/expertise.
Probably the most significant downside with traditional MDR solution is that the provider is simply taking on the responsibilities of managing an EDR platform with all the challenges that this may bring, taking all the shortcomings and applying this across many more end points along with the issues of correlating thousands of end point devices. An individual client can become lost in an alert storm.
Advanced Managed Detection and Response (AMDR)
The next client revolution of EDR/XDR/MDR, is the Advanced Managed Detection and Response provider (AMDR) or Artificial Intelligence Driven Managed Detection and Response provider.
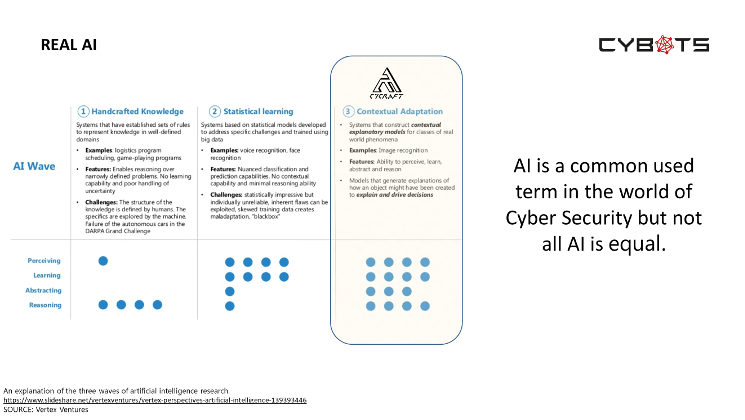
Cybots AI is the first AMDR provider in the world and Cybots are leading the implementation of Artificial Intelligence in analysing telemetry, correlation then applying threat intelligence to provide Protection, Detection and Response, thereby managing this complexity completely for clients.
The AMDR takes a forensic approach to the problem of processing the vast amounts of telemetry data sources and correlation functions traditionally completed by SOC operators and Tier 1 and Tier 2 Security Operators.
First; with the end point, only metadata that needs further processing is sent for deep analysis, reducing the amount of traffic between the device and the network to the range of hundreds of kilobytes per day.
Next; Cybots AMDR implements Artificial Intelligence (AI) machine learning (ML) algorithms to process all the telemetry data before automatically applying Threat Intelligence insights from multiple sources to the suspicious data, identifying known threats and attacks based on Threat intelligence. Any advanced suspicious activity is automatically reviewed by a Cybots Tier 3 Security expert to analyse, around one in every ten suspicious actions, making AMDR FAST.
MSSP AMDR advantages
What AMDR gives the MSSP providing the service is a much lower total Cost of Ownership and much improved MTTD and MTTR:
- All correlation and analysis processing completed before the MSSP or SOC operations team receive the alert.
- No false positives, no configuration required
- Initial compromise alert is generated within 60 seconds from detection
- 15 minutes later – Full flight plan of incident; infected end points, threat intelligence information, remediation plan – including files to isolate are in the hands of the response team
- Story board of incident displaying all aspects of the cyber attack are presented to the incident response team.
Client Organisation
AMDR gives organisations the ability to provide the highest level of Cyber security risk reduction by outsourcing their Protection, Detection and Response services to a AMDR provider.
- No false positives, no configuration
- No personal data is transmitted to the AMDR platform
- No administrative rights are given to the AMDR provider
- The response to a Cyber attack is 1 minute for the initial report and 15 minutes for the full remediation plan.
- No security specialisation needs to be hired, the AMDR provides the response plan down to the End Point and files that need to be removed.
- Client can use AMDR as a part of their SOC team, using the AMDR for all security Expertise.
Summary
In Summary, whether looking at EDR or MDR as a solution to an organisations protection, detection and response requirements, consider all the variables of your chosen path.
EDR / XDR solutions have a steep learning curve with no easy path to correct implementation, when an organisation can not implement correctly there is no “free” consultancy service to help. EDR solutions have a very high Total Cost of Ownership (TCO) with very little relief, if purchasing a 12 month subscription a client may only receive 6-8 months of useful service due to implementation timelines.
MDR provider solutions will take over EDR for the majority of clients due to the fact they hide the complexity for the client as the MDR provider manages this risk. The costs behind the MDR veil is similar to the EDR customer so be careful for charges related to false positive alerts and investigations that do not need to occur.
Advanced Managed Detection Response (AMDR) provider solutions like Cybots are the next generation in MDR services. Fully automated, using advanced Artificial Intelligence, no human analysis needed to perform 90% of the correlation, threat hunting or threat analysis; therefore speeding up threat hunting to minutes from first sign of compromise. Expert oversight is minimal and there is nothing to pay above the service price.
Disclaimer: Michael is employed by Cybots AI, although article has been written from the perspective of a logical journey through Detection and Response maturity, it is an opinion by an employee of the company mentioned.






Leave a Reply