Data Incontinence – when leaks sneak out – It is the new thing, right? media reports almost daily that sensitive data is leaving our organisations via attacker or attackers unknown; who are breaching corporate networks and applications to exfiltrate data.
But, is it also likely the people who leave your employment take data with them and that this happens much more often than a data breach by an anonymous criminal from Crimea smoking cigarettes and drinking Red Bull? (No offence for my Crimean smoking friends, I do draw the line with Red bull though!)
FACT: Ex-employees have been “taking” data for as long as people have been employed, but the seriousness of this has only become a problem since Cloud Storage and bandwidth became so vast and ubiquitous.
It may be only the client contacts on ones phone (everyone is guilty of this!) or the sneaky email forwarded to a Gmail account or far more maliciously; a copy of the Customer database onto a USB stick.
To prevent data being leaked, What should you do? What can you do?
An organisation can not protect all “bits and bytes” of information from being a potential target of data theft, but you can create a plan to identify, restrict access and protect the data that is critical to the business and having a mitigation strategy in place for all other data regardless of criticality.
Start by doing an assessment (IDENTIFY) on your data
Identifying your Assets (NIST CSF)
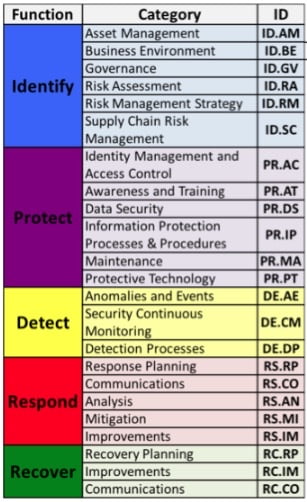
Identify
- Determine what data you have that needs to be secure (not the fantasy football picks).
- Categorise this data by importance/cost to the business (if stolen) and risk if it was to be misused.
- Review your data categorisation, assign each data store a weighted score; business cost vs business risk.
- Locate and document each data source
- How it is accessed/used, stored at rest and backed up.
- Who has access to the data
- Do all users who have access actually need access, remember “Least Privilege”
- Using the collected information, peer review with the respective Business units – use their input about the data and their understanding of the risk to the business
- The business may have a different view on the importance or not – this is ok so long as each party understands the risk.
- Generate a report using “Board of director language” – no tech speak (KISS), a simple report with;
- the data classifications
- risk to the business if breached
- likelihood of breach with current tools
- processes and people involved
- cost to resolve.
- Include in costs, services, maintenance (for staff to manage), annual renewals etc
- If a vendor solution can it be used across multiple silos/projects to enhance the security of the business overall.
Finally ensure your proposal fits nicely into frameworks and industry best practise, thus ensuring you have corroborated your corporate security program with what is industry best practise. This ensures the plan can be justified and defended through the outcomes that are proposed.
GOOD LUCK! there is much more that has been missed from this list, this is just a starting point.
A good place to start is the NIST CSF; familiarise yourself with the language used here:
And the Australian Cyber Security Centre has a lot of advice as well here.
When your business implements a solid strategy around the data you own then you have the best chance of protecting it from internal and external threats – no leakage! or maybe a little…
Data Leakage Summary
Your business data is the lifeblood of your existence, so make sure to protect it. If you have not been breached then you will be, if you have been breached, you will be breached again.
There are people in this world that have no greater goal than causing pain to others even without financial outcomes.

To limit and secure sensitive data exfiltration by internal employees either accidentally or intentionally, implement a Data Loss Prevention and Detect and response strategy, for data that is stored as well as data that is in-flight either on the network or outside the Firewall.
Solutions to secure your organisation from Breach and data loss are primarily categorised as;
- Data Loss Prevention (DLP) and Client Access Security Broker (CASB) and these solutions will help manage the risk to your organisation of both Employees leaving and taking data or breaches where data is being exfiltrated. These solutions fit into the NIST CSF categories of 2.Protect, 3.Detection
- Advanced Managed Detection Response (AMDR), Managed Detection Response (MDR), Endpoint Detection Response (EDR) and eXtended Detection Response (XDR), these solutions look for signs of breach and fit into the NIST CSF categories 3.Detection and 4.Respond
Contact us here if you would like assistance with Data Leakage or anything else.






Leave a Reply