Sandboxing with Windows 10 – Microsoft Defender Application Guard
Read More: Sandboxing with Windows 10 – Microsoft Defender Application GuardSandboxing with Windows 10 – Microsoft Defender Application Guard, the feature to sandbox suspicious or unknown documents has been in Windows for some time and is very useful in preventing Malware from Office macros and other runtime nasties from being able to infect your machine. Sandboxing allows applications / documents etc to run inside their…
An Empirical Assessment of Endpoint Detection and Response Systems against Advanced Persistent Threats Attack Vectors
Read More: An Empirical Assessment of Endpoint Detection and Response Systems against Advanced Persistent Threats Attack VectorsAn Empirical Assessment of Endpoint Detection and Response Systems against Advanced Persistent Threats Attack Vectors. Recently I wrote about EDR failure to detect and respond to cases of Advanced Persistent Threats here after discovering a research paper on the topic when researching the use of Machine Learning in cyber security Detection and response solutions such…
Microsoft Defender Endpoint Deployments
Read More: Microsoft Defender Endpoint DeploymentsRecently I have been deploying Microsoft Defender for Endpoints into my lab environment as a part of my job function. I am responsible for aiding resellers and Managed Service Providers (MSP) to implement Microsoft Security solutions for their business customers. Personally I have been working with tech for many years but almost always using Microsoft…
Mic
Microsoft Defender for endpoint server licensingRead More:Microsoft Defender for endpoint server licensing, Microsoft licensing is hard to follow at the best of times, not to mention product name changes/updates, licensing terms etc etc. Recently I have been involved in licensing questions for reseller and Managed Service Providers (MSP) across my region and Microsoft Defender for endpoint server licensing has come up…
Mic
Microsoft Defender for endpoint server licensingConfiguring Microsoft Autopilot clients
Quick guide
Read More: Configuring Microsoft Autopilot clientsConfiguring Microsoft Autopilot clients – Microsoft has some impressive functionality with their Microsoft 365 Business Premium licensing (for under 300 users) and with Microsoft Endpoint manager, I have mentioned in other posts about Microsoft Defender for Endpoints as another excellent way to improve your security without the traditional cost associated with tools such as CrowdStrike…
Quick guide
Microsoft Defender for Identity
Read More: Microsoft Defender for IdentityMicrosoft Defender for Identity is the Microsoft offical method of protecting Active Directory and on-premise infrastructure from cyber breach. Microsoft Defender for Identity integrates with Azure Arc to add many additional layers of telemetry to Microsoft Sentinel for SIEM and SOAR providing organisations with detection and response to both on-premise and cloud focused cyber attacks.…
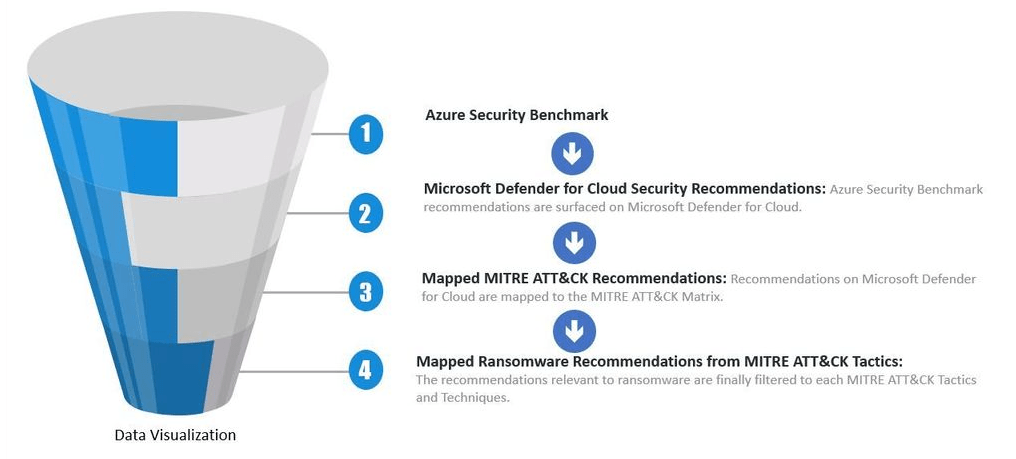
New Ransomware Recommendation Dashboard in Microsoft Defender for Cloud
Read More: New Ransomware Recommendation Dashboard in Microsoft Defender for CloudNew Ransomware Recommendation Dashboard in Microsoft Defender for Cloud, Microsoft have released their new Ransomware recommendation workbook for Microsoft Defender for Cloud. As a Microsoft Partner or a Microsoft customer having Microsoft Defender for Cloud is included with your M365 Business Premium and M365 E5 licenses and an excellent way to determine your organisations security…
Lapsus$: Microsoft and Okta “breaches”
Read More: Lapsus$: Microsoft and Okta “breaches”Lapsus$: Microsoft and Okta “breaches”: When our children start being involved in masterminding cyber “breaches”, the methods change………. Microsoft and Okta were attacked in the same way as my 9 year old daughter uses when she wants more Roblox time……. 30-40 messages in short succession until I relent (or I put imessage into silent mode),…
WAZUH Open source security platform
Read More: WAZUH Open source security platformWAZUH Open source security platform is a fork of OSSEC, it has been around since 2015 as a product and is growing in adoption. What is Wazuh Wazuh is an eXtended Detection and response platform that does not claim any level of either: Artificial Intelligence Machine Learning or, that it is easy These are the…