Hyperbole – Cyber incident response
Read More: Hyperbole – Cyber incident responseHyperbole (love the word!) ….. I would be disappointed if my business leaders thought that my security team could not respond to a cyber incident. The linked article describes that business leaders do not feel their organisation could respond to a cyber incident. So what is the problem? The article is not an accurate impression?…
Controls vs. Control functions
Cyber security planning
Read More: Controls vs. Control functionsGetting your terminology right is extremely important and I for one have made this error before. Control – Anything directly or indirectly used that affects the frequency or magnitude of a loss. Control Function – How a control directly or indirectly affects the frequency or magnitude of a loss.
Cyber security planning
You will be Attacked! What do you do?
Read More: You will be Attacked! What do you do?Cyber Security is a necessary part of your operation, no Cyber Security plan places your business at risk of being ruined, unlike traditional theft where a criminal needs to breach your physical office location. A Cyber Security attack from criminals is targeted across as many businesses as they can reach, searching for an easy victim,…
Single Sign On (sso)
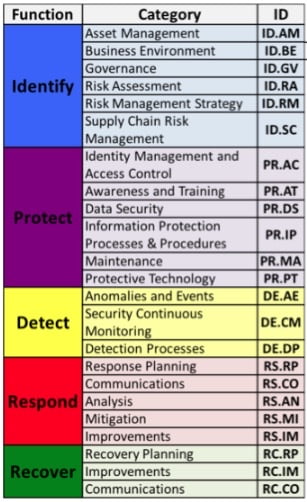
CSF framework: 1. Identify; 2. Protect. Cyber Maturity Level:⭐️⭐️
Read More: Single Sign On (sso)redentials, that credential is able to be used by each system querying a central system (Authentication service) to provide the user access to a service or system. This is different from a Password manager or “Screen Scraping” where a user name and password is “replayed” into the session.
CSF framework: 1. Identify; 2. Protect. Cyber Maturity Level:⭐️⭐️
101 Cyber security primer
Read More: 101 Cyber security primerCyber Security assessments are critical to understanding where your organisation is maturity wise.
Starting out – New Security officer
Read More: Starting out – New Security officerStarting out with an organisation and don’t know where to start?
Employees vs Home owners
Read More: Employees vs Home ownersOr a look into the psychology I have written about this before and today I saw a question today on linkedin related (Thanks David) …….. But I ran out of words to post as a comment. I want to start by suggesting that often security officers and auditors do not think about the companies assets…
Teach your employees information security
Read More: Teach your employees information securityWhen it comes to securing an organisations digital assets there are several approaches to minimising the risk as there is no solving a moving target. One that is not given the priority is the most obvious and the largest source of risk to a business: people, that is you and me, we are idiots and…