Please forget the, “It won’t happen to me“, or “My business is too small to be a target“, every single internet facing IP address on the planet is being probed at many different times again and again for any weakness: an open port, a vulnerable service, a legacy app that is not patched etc etc.
In the same vein, every company, every government department and every individual on the entire planet has received Phishing emails – let me qualify; If you have an email address that was not created last week! and then double qualify, Gmail will automatically SHOVE them into your Spam folder, go look there…..
Cyber Security is a necessary part of your operation, no Cyber Security plan places your business at risk of being ruined, unlike traditional theft where a criminal needs to breach your physical office location. A Cyber Security attack from criminals is targeted across as many businesses as they can reach, searching for an easy victim, just like a predator will take the slowest and the weakest victim in a herd, because its easy!

The Weakest is lunch, the next weakest is Dinner
— the hungry Lion
Attackers are not going after 1’s and 2’s, they target thousands of businesses at the same time and quickly narrow their “sales” funnel down to the weakest “customers”.
Because of this, your business is at risk, guaranteed…… no Maybe, no if, no but, no nothings!
Now whether you choose to do anything about your risk is up to you, maybe you do a lot of sky diving, tightrope walking, lion taming, shark baiting etc, then it is understandable that you do not take the risk of Cyber Breaches as a big issue;
by the way, Lion tamers do not make up a large percentage of business owners from what I can research about this hobby….
For anybody else, you are putting your livelihood at risk if you do not have plans and processes to protect your income from Cyber Criminals
Cyber criminals or Hackers are in a new world of criminal engagement, there are no borders anymore. There are no “police” patrolling the streets at night looking for “odd” behaviour, and often after a breach has occurred no one can help you get your money or data back! There are also too many cyber criminals for any Authority to be able to assist with.
Create a Cyber Security plan
There are so many great resources online for all businesses, to help them with the first steps in Cyber Security Maturity, many of these are free and will get your business to the first steps towards being protected from cyber crime as much as possible.
I recommend that an organisation just starting to evaluate their Cyber Security posture should look at The Australian Cyber Security Centre website and complete the evaluation as a very first step:
https://www.cyber.gov.au/acsc/small-and-medium-businesses/cyber-security-assessment-tool
Use the information from this assessment to start building a cyber Security plan for your business, every business is different and the framework that is correct for your business is unique.
If your organisation is a little more Cyber Mature then, start with a Framework approach, such as the NIST CSF to determine what is most critical to your business and determine a starting point.
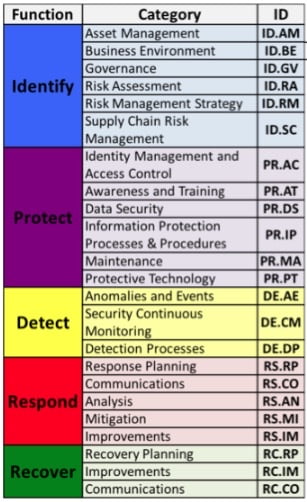
The successful components of a Cyber Security Framework according to the NIST CSF are:
| Function | Explanation |
| Identify | What do we need to protect? |
| Protect | Implement methods to protect those assets |
| Detect | Implement methods to detect Cyber Security Incidents |
| Respond | Build plans and processes to respond to Cyber Security incidents |
| Recover | Implement methods to recover from Cyber Security incidents |
Each organisations Cyber Security Framework may be different to this, it may be more simple than the above or it may be more complex. The benefit of using an internationally accepted model though is that it becomes easier to relate to management and it will work into other internationally recognised standards such as the Mitre Att&ck framework to provide a Holistic approach to Cyber Security.
Final Note
Every business that is, “in business” will be a target of an attempted attack, not once but as many times as their business proves to be an easy target,
Do not be an easy target!
I will continue to add to these to help business looking for ideas to improve their Cyber Security Maturity so please check back regularly.





Leave a Reply