AI the biggest hype bubble for 2024
Read More: AI the biggest hype bubble for 2024AI the biggest hype bubble for 2024 If you are not already aware of the fact that AI is going to take your job and then subsequently take over the world, then you are living under a rock. Before that time (the end of the world) though there are a plethora of opportunities for you…
ASD8 – Implementing Australian Signals Directorate Essential Eight with Microsoft
Read More: ASD8 – Implementing Australian Signals Directorate Essential Eight with MicrosoftASD8 – Implementing Australian Signals Directorate Essential Eight with Microsoft. Introducing ASD8 and Microsoft The Australian signals Directorate has been a frontrunner in creating, guiding and improving the cyber security posture of Australian Government and non government entities, through the Essential 8 cyber security controls which I have previously covered here and here are critical…
A man, a Goat, and a Boat meets generative AI
Read More: A man, a Goat, and a Boat meets generative AIA man, a Goat, and a Boat meets generative AI Ask a Large Language model the question, “A man is walking with a goat and they come to a river with a small boat on their side. How can they get across the river?” The answer that is generated is not the sensible answer, being…
Ticketmaster – When a third party supplier breach is not what it appears
Read More: Ticketmaster – When a third party supplier breach is not what it appearsTicketmaster – When a third party supplier breach is not what it appears. As many of us learnt whilst growing up, most of the time obfuscating facts to portrait yourself in a brighter light actually creates a bigger problem. Now as an adult I am not going to have my parents tell me off but…
Kicksec’s Data has been breached – again
Read More: Kicksec’s Data has been breached – againGlossed over the email from Firstmac on Friday, reporting that my data has been gathered in a “limited” cyber security breach of their systems, limited now days includes sensitive citizen data clearly.
Microsoft Copilot for Security Ninja Now operating and at your service!
Read More: Microsoft Copilot for Security Ninja Now operating and at your service!Microsoft Copilot for Security Ninja Now operating and at your service I recently completed my Microsoft Copilot for Security Ninja training, now I’m ready for those Security copilot conversations with Partners and customers….. of course this is not true! I am but a mere amateur. I do have the ‘certificate’ but I am no expert…
LogRythm, Exabeam, Splunk, Qradar, Palo Alto …. arrr
Read More: LogRythm, Exabeam, Splunk, Qradar, Palo Alto …. arrrLogRythm, Exabeam, Splunk, Qradar, Palo Alto …. large cyber security acquisitions are happening to the left, to the right and straight ahead too, what is going on and why is this occurring? For those 15 of you who have not read the news yet, here it is: LogRythm and Exambeam join forces, Splunk is acquired…
NSW Clubs – Impacted by Breach of customer data
Read More: NSW Clubs – Impacted by Breach of customer dataNSW Clubs – Impacted by Breach of customer data Another Australian business affected through a 3rd party cyber incident, though in the linked article (at the footer of this post) great pains are taken to explain that it is not their own systems but rather a 3rd party, yet who owns the data that has…
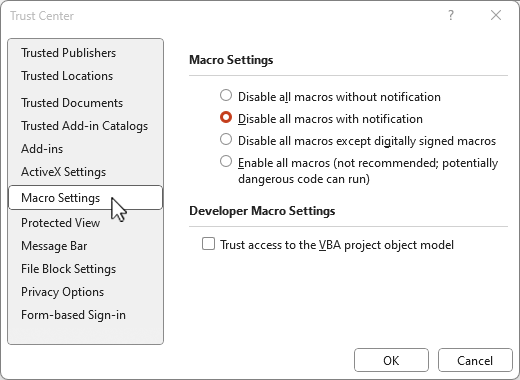
Microsoft Office Macro security – Are you covered?
Read More: Microsoft Office Macro security – Are you covered?Microsoft Office Macro security – are you covered? Microsoft Office macros are an amazing way to automate and script many parts of a business process, sometimes directly on an Office document, Spreadsheet or PowerPoint but also for interacting with third party data, the operating system and more, which is also why the recommendation today in…
AI devices currently, nothing but “hot Air”
Read More: AI devices currently, nothing but “hot Air”AI devices currently, nothing but “hot Air”, problems with what is possible with our voice, conflicts with the ideas of start up founders to make money. Mr Who’s The Boss, a YouTube influencer and content creator summarised this with another AI device vying for our wallets here very succinctly. If you plan to buy this…