Microsoft Office Macro security – are you covered?
Microsoft Office macros are an amazing way to automate and script many parts of a business process, sometimes directly on an Office document, Spreadsheet or PowerPoint but also for interacting with third party data, the operating system and more, which is also why the recommendation today in 2024 is to prevent macros from being used by most users, “with Great power comes great responsibility” as Peter Parkers’ Uncle Ben first told him in 1962, with a sense of foreboding maybe?
The good ol’ office Macro went from being a method to autofill or autocomplete actions into a full blown programming environment and even a language in Microsoft Visual Basic for Applications.
The problem with Macro Security
Office Macros have immense power as I have discussed and many users within an organisation simply have no need to be able to run them, unless business processes have been tied into a Macro, in which case they shouldn’t be, a macro is not an application, it can not be designed with Security Systems Development Lifecycle as a core principle as the development environment does not even support any sort of security model.
What has occurred in many organisations though is that Microsoft Office Macros run parts of the business, no longer bound by a small number of users, the capability to run Macros ends up being enabled on all devices and this becomes an important Cyber Attack vector for Threat actors with historical threats such as Emotet etc which utilised Microsoft Office documents to perform their attacks.
Microsoft Apps for Business has a secret
I didn’t realise until very recently that a difference between Microsoft Apps for Business and Microsoft Apps for Enterprise is Microsoft Group policy support and in this context specifically, support for modifying Microsoft Office security settings with Group policies is not possible with Apps for Business.
This is a significant failing in my opinion and in the journey to improved basic security postures for businesses looking to achieve any sort of cyber security framework compliance like the Australian Signals Directorate Essential 8, which requires Blocking Macros from the majority of users without a specific requirement – something that can not be achieved with the productivity suite that 90% or more of small businesses in Australia utilise.
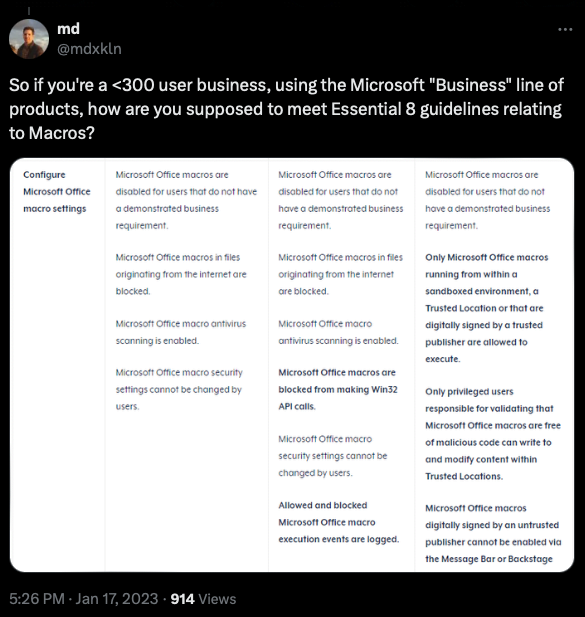
Born’s Tech and Windows World writes about this very well in the following article:
But, I hear you say, Attack surface Reduction Rules are configured via Intune, these will work right? Nope, they do not, they still leverage the same group policy elements and therefore do not function to block Microsoft Office Macros.
To say I am very disappointed in Microsofts approach here would be an understatement, a critical control in all cyber security Frameworks is not possible with the Microsoft security basics productivity suite “M365 Business Premium“, I hope and have my fingers crossed that this is simply an oversight on Microsofts part and when I wake up, it will be fixed.
There is a work around though, and I will cover this below.
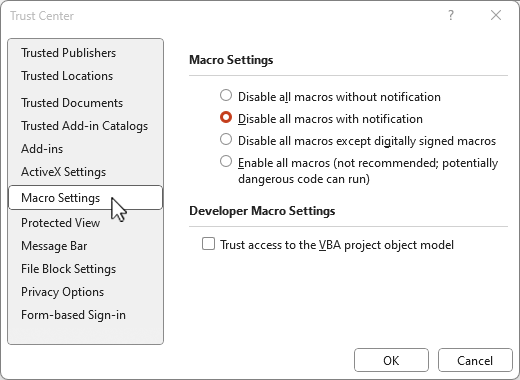
block Macros with Apps for Business (today at least)
Firstly, Jeffrey Appel writes on how to configure the Macro blocking settings here so please have a read and see if it solves your issue, if not then please read on.
Someone has spent some time to create these ADMX and ADML configurations to change the user settings in a device registry, thereby avoiding the problem with needing Microsoft Apps for Enterprise:
I found the above by following a Reddit topic on the same issue, here. be aware that any Office configurations you make centrally using office policies will stop these user settings working, therefore you must make sure that only user settings are pushed out to your users.
The configuration works today as confirmed by an MSP I was speaking with today but the capability could change at any time.
Important note: Always test before deploying and I can not guarantee that any of this works or is safe from malware or other malicious behaviour.
Conclusion
It is extremely disappointing to me that such a fundamental capability to reduce a device attack surface is not available to users of the M365 Business Premium licensing, it simply does not make sense from a pragmatic point of view to alienate most sub 300 seat organisations from this safety setting, especially when so many other security features are available in a M365 Business Premium.
I have to believe that as a Cyber Security Consultant, this is an oversight that will be rectified soon by Microsoft and until that time, to reach the Australian Signals Directorate Essential 8 ML 1 your business requires Microsoft Applications for Business, meaning your starting License SKU is at least: M365 E3 along with additional licensing required for several features.





Leave a Reply