Trend XDR – Microsoft sentinel Integration
Read More: Trend XDR – Microsoft sentinel IntegrationUsing Trend XDR – Microsoft sentinel Integration is an excellent way to connect to additional sources of telemetry data and add this to your corporate instance of Microsoft Sentinel for SIEM and SOAR capabilities. I discovered this article this morning in my feed and thought it would be great to share as it is a…
WAZUH Open source security platform
Read More: WAZUH Open source security platformWAZUH Open source security platform is a fork of OSSEC, it has been around since 2015 as a product and is growing in adoption. What is Wazuh Wazuh is an eXtended Detection and response platform that does not claim any level of either: Artificial Intelligence Machine Learning or, that it is easy These are the…
EDR, XDR – NDR
Read More: EDR, XDR – NDRWith the uptake of Cyber Security solutions by clients globally it was only a matter of time for EDR tools to be mainstream for customers as it is today in 2022. NDR is also starting to make progress towards mainstream adoption in 2021 as detailed in the below image.
AV NGAV EDR XDR MDR AMDR
Read More: AV NGAV EDR XDR MDR AMDRThe cyber security landscape has seen huge expansion and growth in the past 5 years and End Point Detection and Response (EDR) has been one of the biggest areas of expansion. https://www.morphisec.com/hubfs/2020%20State%20of%20Endpoint%20Security%20Final.pdf According to Ponemon Institute, 68% of organisations suffered one or more endpoint attacks that successfully compromised data or IT Infrastructure. In 2018 Gartner…
Artificial Intelligence?
Read More: Artificial Intelligence?Artificial Intelligence is not always Artificial Intelligence, every Cyber Security vendor selling solutions today is either putting an “using AI” sticker on their website, or they are investigating how they can use Artificial Intelligence “AI” and Machine Learning “ML”in their branding. It stands to reason as the terms are well on the incline of the…
Data Incontinence – when leaks sneak out
CSF framework: 1. Identify; 2. Protect. Cyber Maturity Level:⭐️⭐️
Read More: Data Incontinence – when leaks sneak outTo prevent data being used against you in the future either through competitive, intellectual or malicious usage or publication? What should you do?
CSF framework: 1. Identify; 2. Protect. Cyber Maturity Level:⭐️⭐️
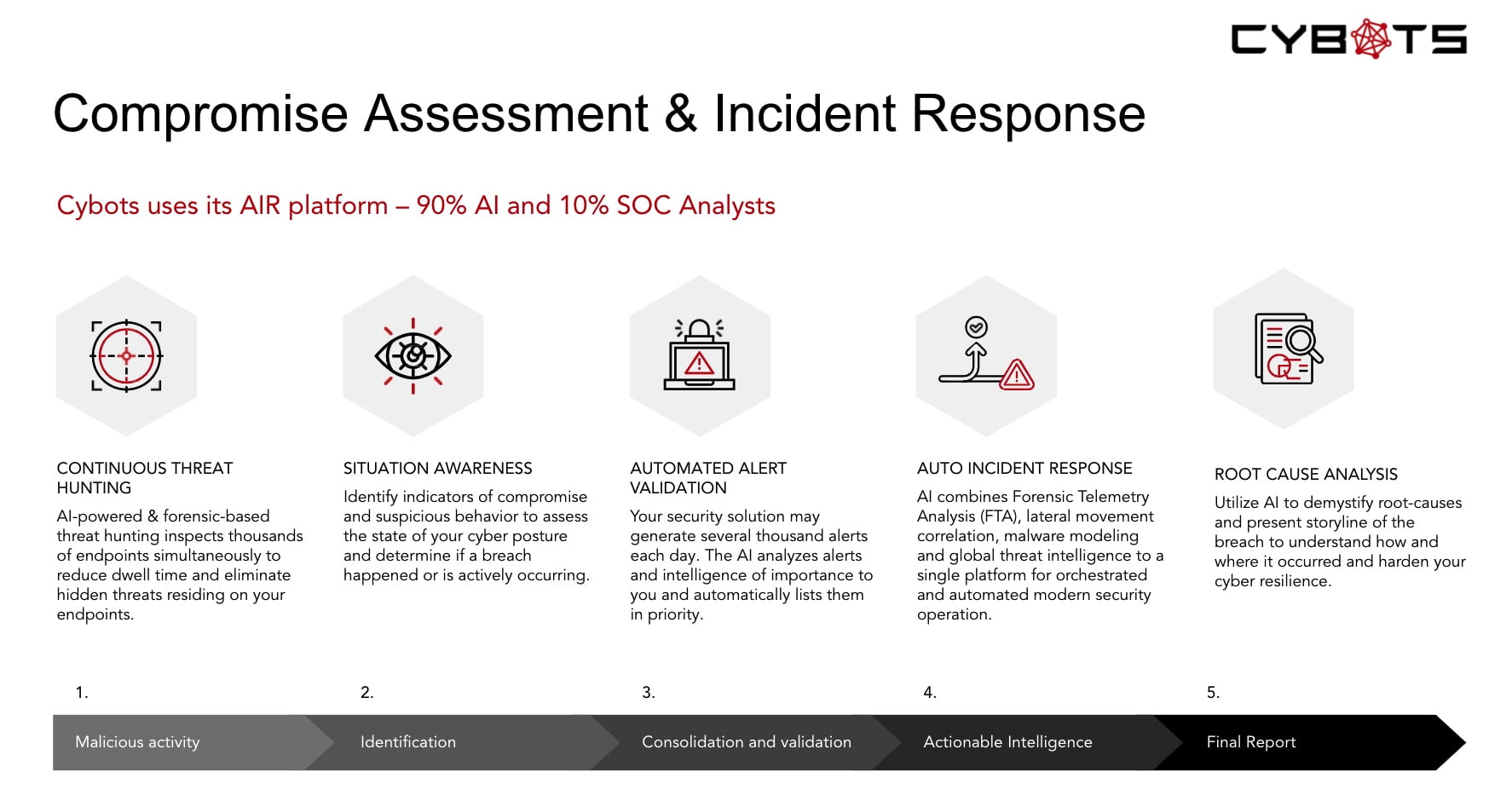
Managed Detection and Response (mdr)
CSF framework: 2. Protect; 3. Detect; 4. Respond. Cyber Maturity Level:⭐️⭐️⭐️
Read More: Managed Detection and Response (mdr)Detection and Response or the may be eXtended Detection and Response, this depends on the Solution provider of MDR. Newer solutions exist now termed as Advanced Managed Detection and Response which is a merging of MDR along with additional capabilities to provide advanced Detection and Response capabilities.
CSF framework: 2. Protect; 3. Detect; 4. Respond. Cyber Maturity Level:⭐️⭐️⭐️