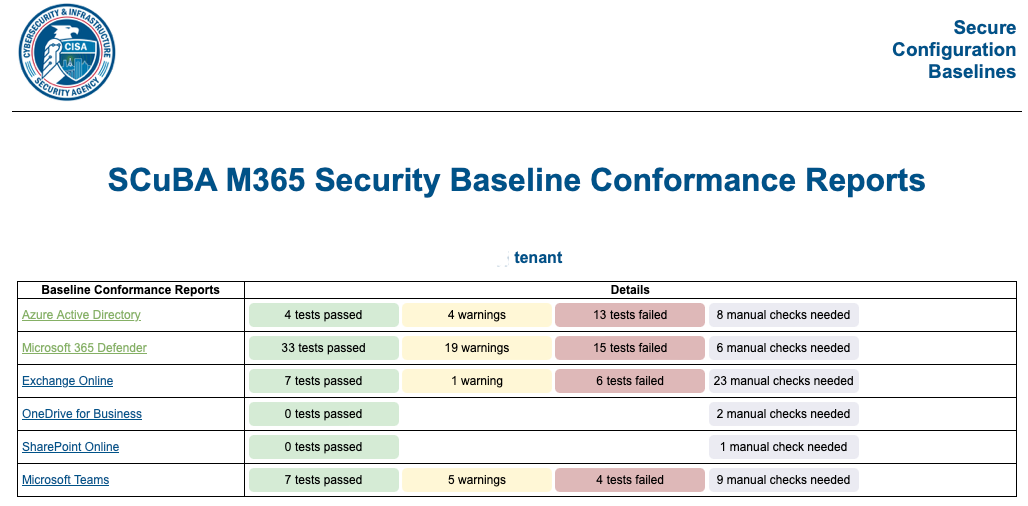
SCUBA now scans Google
Read More: SCUBA now scans GoogleSCUBA is not Scuba, one is a pursuit I would like to try one day and the other is something to deetect misconfigurations and some security vulnerabilities in a cloud environment (the one in all CAPS). CISA SCUBA is maintained and is free, it works for Microsoft 365 environments and now they have updated for…
From Backup to resilient cyber security
Read More: From Backup to resilient cyber securityIn the Beginning From Backup to resilient cyber security: Best practises for Information Technology such as “Least privilege access”, “Admin account segregation”, “Operating system patching”, “Multi-factor authentication”, even “Patching and updating applications” have been around for many years, undertaken as ritual by many Information Technology departments within businesses across Australia as best practise maintainence, without…
CVE-2023-23397: Microsoft outlook vuln
Read More: CVE-2023-23397: Microsoft outlook vulnCVE-2023-23397: Microsoft Outlook Vuln: elevation of privilege vulnerability leads to NTLM credential theft: Very quick and short post today, I have already been contacted today around mitigations for this vulnerability and wanted to get some quick steps out early incase your business is unsure how to check whether you are at risk. My post assumes…
101: Basic Security Posture for WordPress
Read More: 101: Basic Security Posture for WordPress101: Basic Security Posture for WordPress, WordPress is one of the most popular internet technologies in use today, as a tool for amateur and professionals wanting to blog, to sell, to consult or to do almost anything else, nothing comes close to the WordPress ecosystem for flexibility and extensibility – want to build a store…
Microsoft Sentinel – reducing spend and log complexity first
Read More: Microsoft Sentinel – reducing spend and log complexity firstMicrosoft Sentinel – reducing spend and log complexity first, Microsoft sentinel is one of the easiest SIEM platforms to switch on and be usable without configuration. But the devil is in the details of what should be configured to ensure that the signal data being ingested is most useful, minimally duplicated and at the lowest…
Secure Cloud Business Applications – assess your security
Read More: Secure Cloud Business Applications – assess your securitySecure Cloud Business Applications, assess your security – Best of all it is at no cost and provides guidance on best practise security guidelines for business. When reducing the likelihood of a successful cyber attack we need to break down the approach into various elements, a security assessment such as the CISA SCUBA tool is…