Sugar And Statistics, sprinkles of nothingness
Read More: Sugar And Statistics, sprinkles of nothingnessSugar And Statistics, sprinkles of nothingness: Last night I went fishing in our new boat and we caught 2 Dusky Flatheads, ugly but a great eating fish, sorry I digress but it seemed important at the time, here they are – we had no time to name them: Sorry I got distracted (a challenge with…
Protecting Australian Business from Cyber Crime
Read More: Protecting Australian Business from Cyber CrimeProtecting Australian Business from Cyber Crime, easy title to write and a topic beyond complex to implement for many small to mid sized businesses in 2022, Australia. The secret is that it is not complex to get started on a cyber security journey, it is easy to do the basics and reduce the risk of…
As Secure As Practical (ASAP)
Read More: As Secure As Practical (ASAP)As Secure As Practical (ASAP) – As Soon As Possible. In the past few months of 2022 in Australia alone there have been a number of significant cyber breaches across many of our major brand names and this terrible trend is poised to continue to get worse until such time as our organisations uplift their…
Michael Brooke presents the ASD essential 8 on Safari
Read More: Michael Brooke presents the ASD essential 8 on SafariMichael Brooke presents the ASD essential 8 on Safari; recently I had the opportunity to work with TechforGood, an organisation making a difference with Social organisations across Australia. I have two passions other than fishing and family (so four passions in total), these are: Cyber security, the field of cyber security is an industry where…
Protection before Detection – Endpoint detection response
Read More: Protection before Detection – Endpoint detection responseProtection before Detection – Endpoint detection response Endpoint Detection and response gets a lot of attention from the entire cyber security industry, EDR as it is commonly known is a valuable tool in a corporate kitbag, but is Endpoint and response something that should be acquired first, second or where? If we review the Australian…
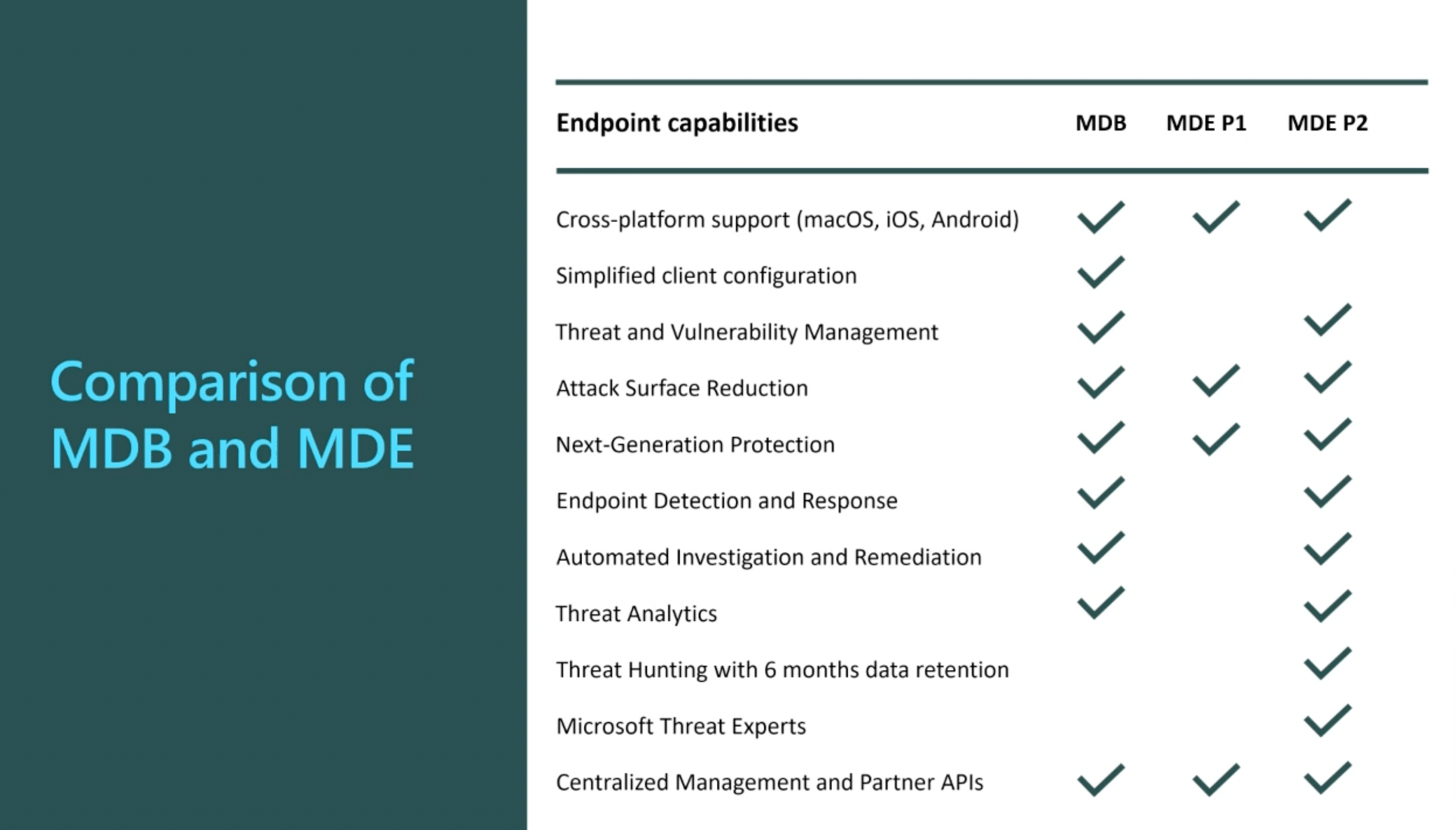
Microsoft Defender for Endpoint training resources
Read More: Microsoft Defender for Endpoint training resourcesMicrosoft Defender for Endpoint training resources: The goal of this page is to put together a level 101/201 resource for consultants and end customers to utilise to find out more about Defender for Endpoints, I will update the details as they change but this is current as of May 2022. Microsoft Defender for Endpoint training…
Easy Fail – Australian critical infrastructure
Read More: Easy Fail – Australian critical infrastructureThe Easy Fail in critical infrastructure should have all of us worried right now, whether it is the water being turned off, the traffic lighting systems that we all rely on to get around the cities we live in or much worse, the Electricity that we used to power our homes and provide us warmth…
SIEM – Security Information & event management
Read More: SIEM – Security Information & event managementSIEM – Security Information & event Management platforms are mature cyber security solutions, often having come from a legacy of application log gathering with the data being used for availability and performance as well as access management, it has been a simple and logical transition into security log gathering and analysis of that data for…
101 Cyber security primer
Read More: 101 Cyber security primerCyber Security assessments are critical to understanding where your organisation is maturity wise.
Privilege access Management
Read More: Privilege access ManagementPrivileged Access Management, cyber attacks often still operate primarily on the premise that a logged in user has privileged access to their workstation or Laptop, this aspect has never changed despite platform providers ‘improving’ their security models over time.