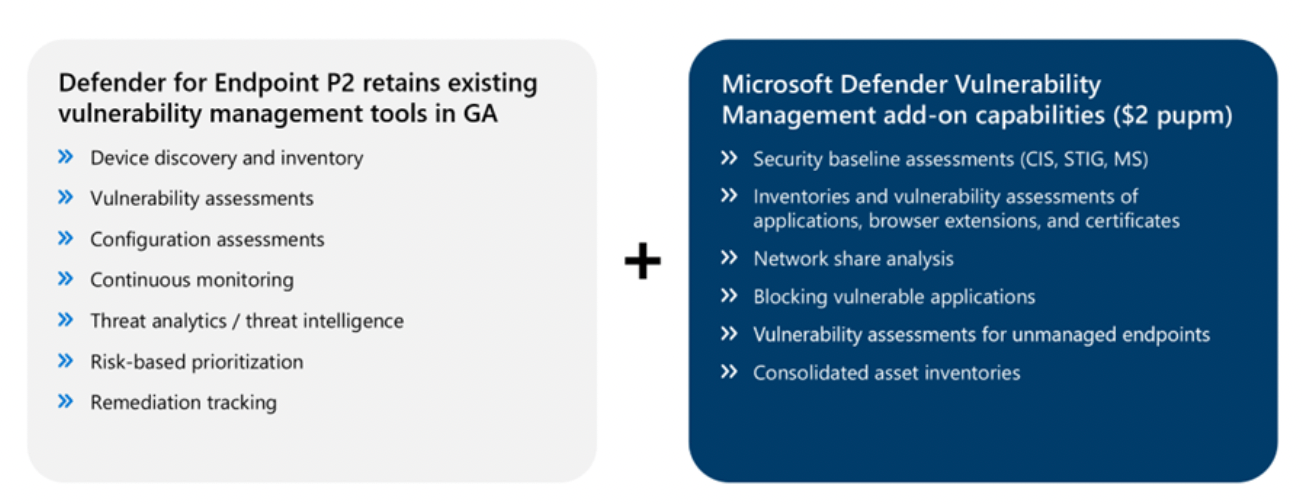
Microsoft Defender vulnerability Management dropping shortly
Read More: Microsoft Defender vulnerability Management dropping shortlyMicrosoft Defender Vulnerability Management dropping shortly for customers as an add-on for Microsoft Defender for Endpoint P2 or a standalone license. Vulnerability assessments and Management of these vulnerabilities has been missing from the Microsoft stable and this is a great addition for customers as it brings the element of protection to what was previously only…
Follina 0 day – Office lets the bad guy waltz right in, WRTF!
Read More: Follina 0 day – Office lets the bad guy waltz right in, WRTF!Follina 0 day – Microsoft Office Macro protection eaten for breakfast!, those of you who know me, know that I embrace Microsoft Defender as a security tool that is top notch, not just my view but the view of the analysts that report on cyber security as well, here for example with the Mitre Evaluations…
Threat Hunters, Hard job, tough to find too!
Read More: Threat Hunters, Hard job, tough to find too!Threat Hunters, Hard job, tough to find too! – the following article has been kindly shared with permission by GravityWall.net from an original article written on their website here. Employing good cyber security candidates is hard So many considerations: technical vs team fit vs ability to learn etc etc, I recently came across this very…
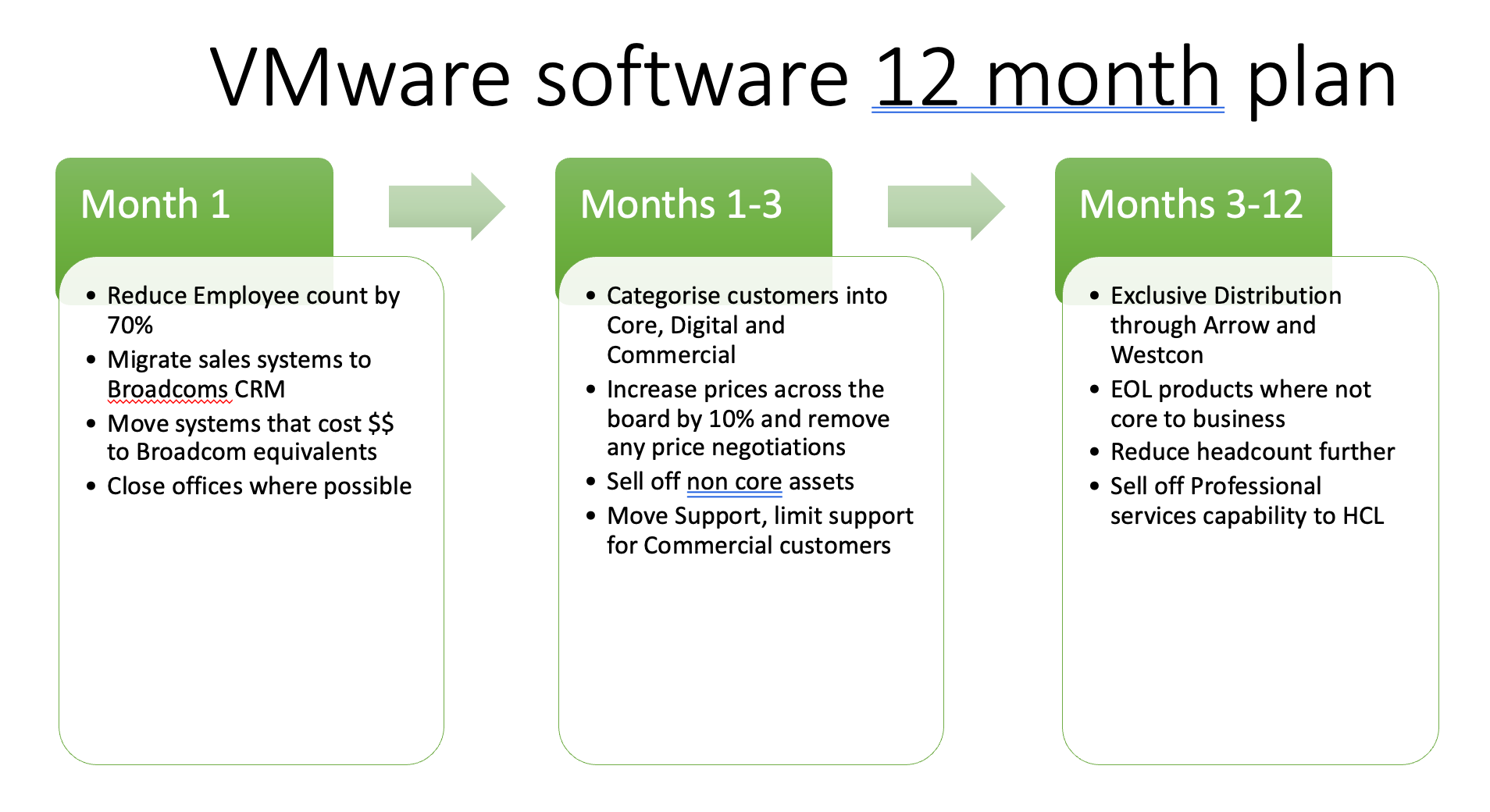
VMware software the next 12 months
Read More: VMware software the next 12 monthsBrian Madden wrote a solid article on VMware recently and what it presents is a very honest opinion on the numbers of a post Broadcom owned VMware world. The key to how Vmware is going to change is in one statement from Hock Tan, and this is:
Broadcom acquires Vmware
Read More: Broadcom acquires VmwareThis article is an opinion piece and is solely the authors views mixed with a little bit of external data and any of the following should be taken as personal opinion. Broadcom seeking to acquire VMware – too big to fail. Update – Broadcom acquires VMware! Update: I have written about the next 12 months…
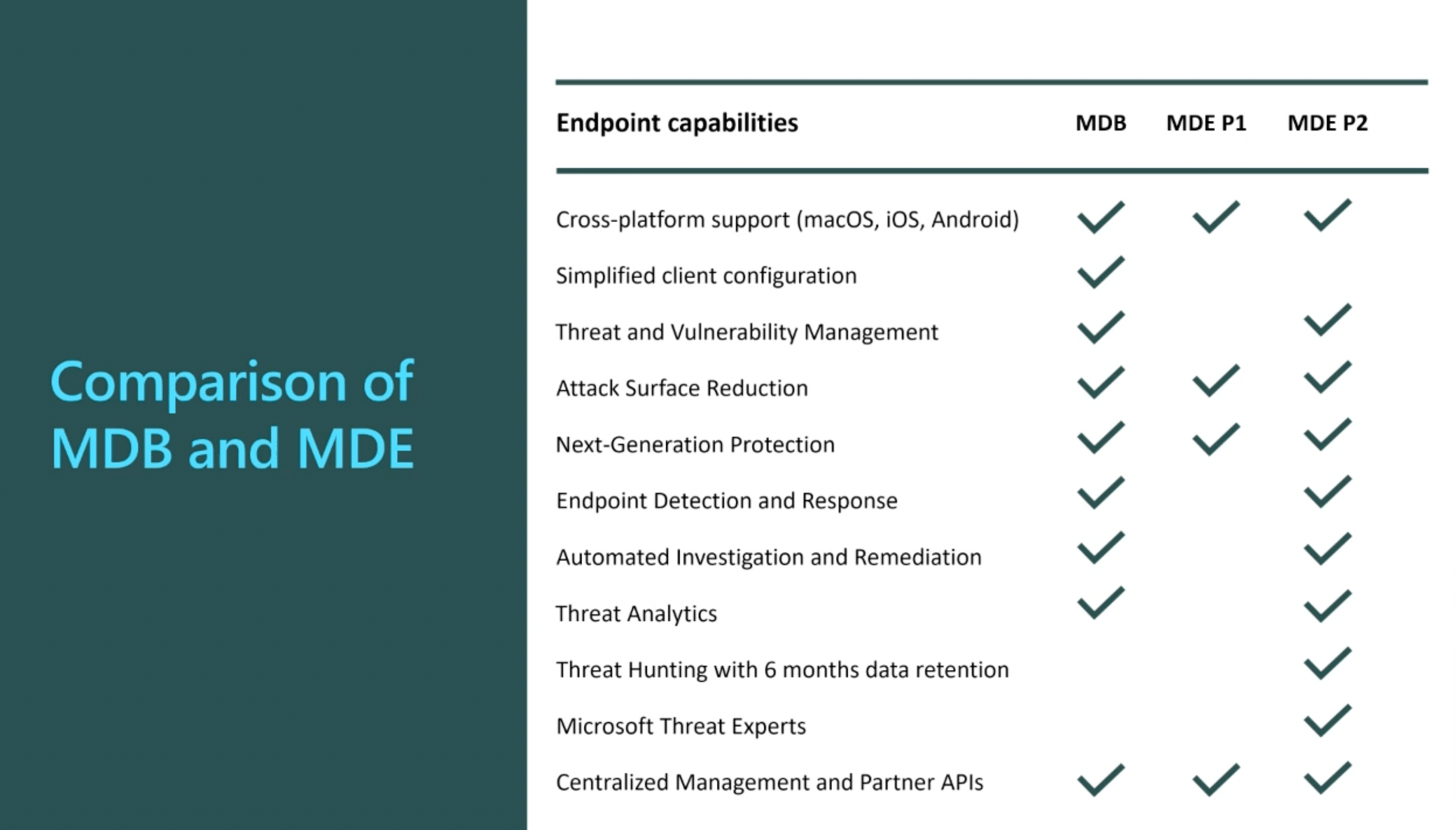
Microsoft Defender for Endpoint training resources
Read More: Microsoft Defender for Endpoint training resourcesMicrosoft Defender for Endpoint training resources: The goal of this page is to put together a level 101/201 resource for consultants and end customers to utilise to find out more about Defender for Endpoints, I will update the details as they change but this is current as of May 2022. Microsoft Defender for Endpoint training…
Microsoft Office app licensing for MSPs utilising RDS
Read More: Microsoft Office app licensing for MSPs utilising RDSMicrosoft Office app licensing for MSPs utilising RDS – short answer is, if you are an Managed Service Provider (MSP) and you are not a Qualified Multitenant Hoster (QMTH) then you can not provide the Microsoft Office apps via Remote Desktop Services (RDS) to your clients. Recently this question was given to me to answer…
Trend XDR – Microsoft sentinel Integration
Read More: Trend XDR – Microsoft sentinel IntegrationUsing Trend XDR – Microsoft sentinel Integration is an excellent way to connect to additional sources of telemetry data and add this to your corporate instance of Microsoft Sentinel for SIEM and SOAR capabilities. I discovered this article this morning in my feed and thought it would be great to share as it is a…
Easy Fail – Australian critical infrastructure
Read More: Easy Fail – Australian critical infrastructureThe Easy Fail in critical infrastructure should have all of us worried right now, whether it is the water being turned off, the traffic lighting systems that we all rely on to get around the cities we live in or much worse, the Electricity that we used to power our homes and provide us warmth…
Why do businesses not do cyber security!
Read More: Why do businesses not do cyber security!for very long), everything a business spends money on that does not make money is an expense and some expenses are more critical than others.