Sugar And Statistics, sprinkles of nothingness
Read More: Sugar And Statistics, sprinkles of nothingnessSugar And Statistics, sprinkles of nothingness: Last night I went fishing in our new boat and we caught 2 Dusky Flatheads, ugly but a great eating fish, sorry I digress but it seemed important at the time, here they are – we had no time to name them: Sorry I got distracted (a challenge with…
Safe worlds update
Read More: Safe worlds updateNews.com.au wrote about the Safe worlds TV scam last year here: Safeworlds $49 million of investors money disappears. Alex Turner-Cohen is working on a podcast to be released in 2024 that will go a long way to uncovering what has happened with Safe worlds TV and to hear from the people who lost money investing…
User vs Device Licensing, Microsoft Defender for Endpoint unmasked
Read More: User vs Device Licensing, Microsoft Defender for Endpoint unmaskedUser vs Kiosk Licensing, Microsoft Defender for Endpoint unmasked, the full story. Once upon a time… Once upon a time far back in technology history (2021 and prior I believe) Microsoft Defender for Endpoint Plan 1 or Plan 2 could be purchased per device or per user, this method of procurement made sense, and still…
NSW Clubs – Impacted by Breach of customer data
Read More: NSW Clubs – Impacted by Breach of customer dataNSW Clubs – Impacted by Breach of customer data Another Australian business affected through a 3rd party cyber incident, though in the linked article (at the footer of this post) great pains are taken to explain that it is not their own systems but rather a 3rd party, yet who owns the data that has…
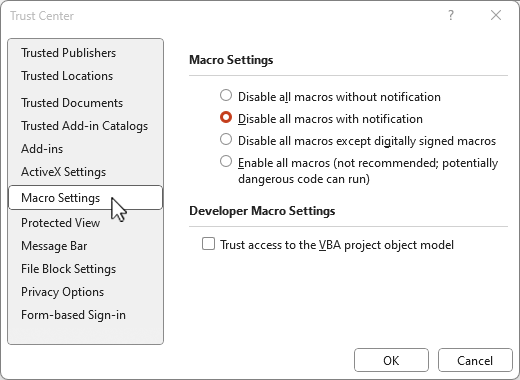
Microsoft Office Macro security – Are you covered?
Read More: Microsoft Office Macro security – Are you covered?Microsoft Office Macro security – are you covered? Microsoft Office macros are an amazing way to automate and script many parts of a business process, sometimes directly on an Office document, Spreadsheet or PowerPoint but also for interacting with third party data, the operating system and more, which is also why the recommendation today in…
AI devices currently, nothing but “hot Air”
Read More: AI devices currently, nothing but “hot Air”AI devices currently, nothing but “hot Air”, problems with what is possible with our voice, conflicts with the ideas of start up founders to make money. Mr Who’s The Boss, a YouTube influencer and content creator summarised this with another AI device vying for our wallets here very succinctly. If you plan to buy this…
SCUBA now scans Google
Read More: SCUBA now scans GoogleSCUBA is not Scuba, one is a pursuit I would like to try one day and the other is something to deetect misconfigurations and some security vulnerabilities in a cloud environment (the one in all CAPS). CISA SCUBA is maintained and is free, it works for Microsoft 365 environments and now they have updated for…
Data Cleansing and Large Language Models
Read More: Data Cleansing and Large Language ModelsData Cleansing and Large Language Models, what is great about large language models for enterprise is also what is potentially most problematic. Training an LLM using your data will bring amazing upsides to productivity, for example, maybe I have a customer who requires my assistance to build out a programme of work for a project.…
Consulting Integrity
Read More: Consulting IntegrityConsulting with Integrity is critically important in my industry of Cyber Security, there are many consultants preaching to be what they are not, “knowledgeable” people. The Cyber security industry is fully of vendors and sellers trying to position security tooling as a solution to a cyber risk problem. I want to share a recent story…
Targeted Business Email Compromise through weaponising your own tenant!
Read More: Targeted Business Email Compromise through weaponising your own tenant!Targeted Business Email Compromise through weaponising your own tenant!, As we in the ‘Industry’ are well aware, 90% of Cyber security incidents start with email, its simple, we all use it and an email attack targets the weakest link in our security posture, me and you. During the past month an old/new cyber criminal attack…