Data Incontinence – when leaks sneak out
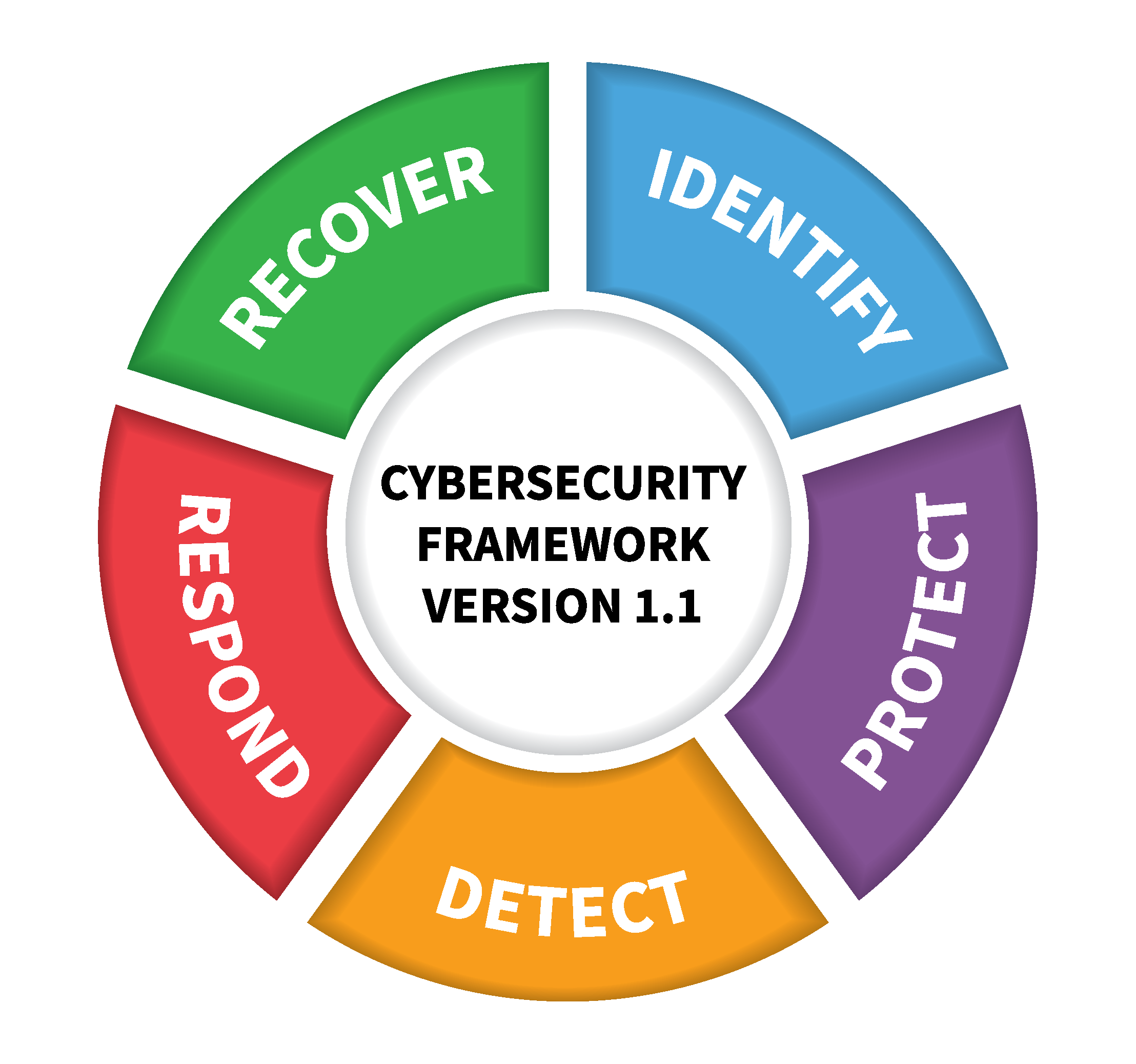
CSF framework: 1. Identify; 2. Protect. Cyber Maturity Level:⭐️⭐️
Read More: Data Incontinence – when leaks sneak outTo prevent data being used against you in the future either through competitive, intellectual or malicious usage or publication? What should you do?
CSF framework: 1. Identify; 2. Protect. Cyber Maturity Level:⭐️⭐️
Managed Detection and Response (mdr)
CSF framework: 2. Protect; 3. Detect; 4. Respond. Cyber Maturity Level:⭐️⭐️⭐️
Read More: Managed Detection and Response (mdr)Detection and Response or the may be eXtended Detection and Response, this depends on the Solution provider of MDR. Newer solutions exist now termed as Advanced Managed Detection and Response which is a merging of MDR along with additional capabilities to provide advanced Detection and Response capabilities.
CSF framework: 2. Protect; 3. Detect; 4. Respond. Cyber Maturity Level:⭐️⭐️⭐️
Advanced Managed Detect Response (AMDR)
CSF framework: 2. Protect; 3. Detect; 4. Respond. Cyber Maturity Level:⭐️⭐️⭐️
Read More: Advanced Managed Detect Response (AMDR)MDR stands for is the next generation of cyber security Detect and Response solutions in the market to target breaches and other malicious activity, eXtended Detection and Response XDR stood for an extended range of detection capability (Network and other devices/ sources of data) and AMDR will take over where XDR lets go.
CSF framework: 2. Protect; 3. Detect; 4. Respond. Cyber Maturity Level:⭐️⭐️⭐️
Client Access Security Broker (casb)
CSF framework: 1. Identify; 2. Protect; 3. Detect; 4. Respond. Cyber Maturity Level:⭐️⭐️⭐️
Read More: Client Access Security Broker (casb)A Client Access Security Broker is a an important component in an enterprise organisation. A Client Access Security Broker or CASB for short provides: 1. Identify; 2. Protection; 3. Detection capabilities for the organisation on the NIST CSF framework model. How it does this is by inspecting traffic that is being sent to and from…
CSF framework: 1. Identify; 2. Protect; 3. Detect; 4. Respond. Cyber Maturity Level:⭐️⭐️⭐️
EndPoint Detection and response (edr)
CSF framework: 2. Protect; 3. Detect; 4. Respond. Cyber Maturity Level:⭐️⭐️⭐️
Read More: EndPoint Detection and response (edr)Endpoint detection and response solutions are now a mainstream Cyber Security solution for organisations with a moderate level of Cyber Security maturity. An EndPoint Detection and Response (EDR) platform helps an organisation with: 2. Protect; 3. Detect; and 4. Respond on the NIST CSF Framework
CSF framework: 2. Protect; 3. Detect; 4. Respond. Cyber Maturity Level:⭐️⭐️⭐️
Identity and Access Management (iam)
CSF framework: 1. Identify; 2. Protect. Cyber Maturity Level:⭐️⭐️⭐️
Read More: Identity and Access Management (iam)Of the many technologies available to organisations today, Identity Access Management or IAM is arguably one of the most mature of all. Legacy companies such as IBM, CA, Oracle, Microsoft and newer innovators such as SailPoint have been providing Identity and Access Management solutions for several years and this market is mature and the problem…
CSF framework: 1. Identify; 2. Protect. Cyber Maturity Level:⭐️⭐️⭐️
Multi Factor Authentication
CSF framework: 2. Protect. Cyber Maturity Level:⭐️
Read More: Multi Factor AuthenticationIf your organisation does not use Multi Factor Authentication yet, then Read on and before you do anything else. Next ensure you get Multifactor authentication implemented ASAP for the sake of your job and your business. The Problem Passwords are not secure in isolation, they need to be remembered and they need to be changed…
CSF framework: 2. Protect. Cyber Maturity Level:⭐️
Does size matter – mdr vendors
Read More: Does size matter – mdr vendorsWhen selecting a vendor for your Managed Detection and Response (MDR) requirements, what are the most critical considerations? Personally I had always considered that the size of the organisation providing my MDR needs was a strong point in favour of vendors like CrowdStrike, SentinelOne, Rapid7, FireEye etc etc…… Once upon a time there was also…
Privileged Access Management (PAM)
CSF framework: 1. Identify; 2. Protect; 3. Detect. Cyber Maturity Level:⭐️⭐️⭐️⭐️
Read More: Privileged Access Management (PAM)This is what PAM solves; the admin account problem – as all account passwords need to be managed how do you do this, the administrative accounts issue is where PAM is your answer.
CSF framework: 1. Identify; 2. Protect; 3. Detect. Cyber Maturity Level:⭐️⭐️⭐️⭐️