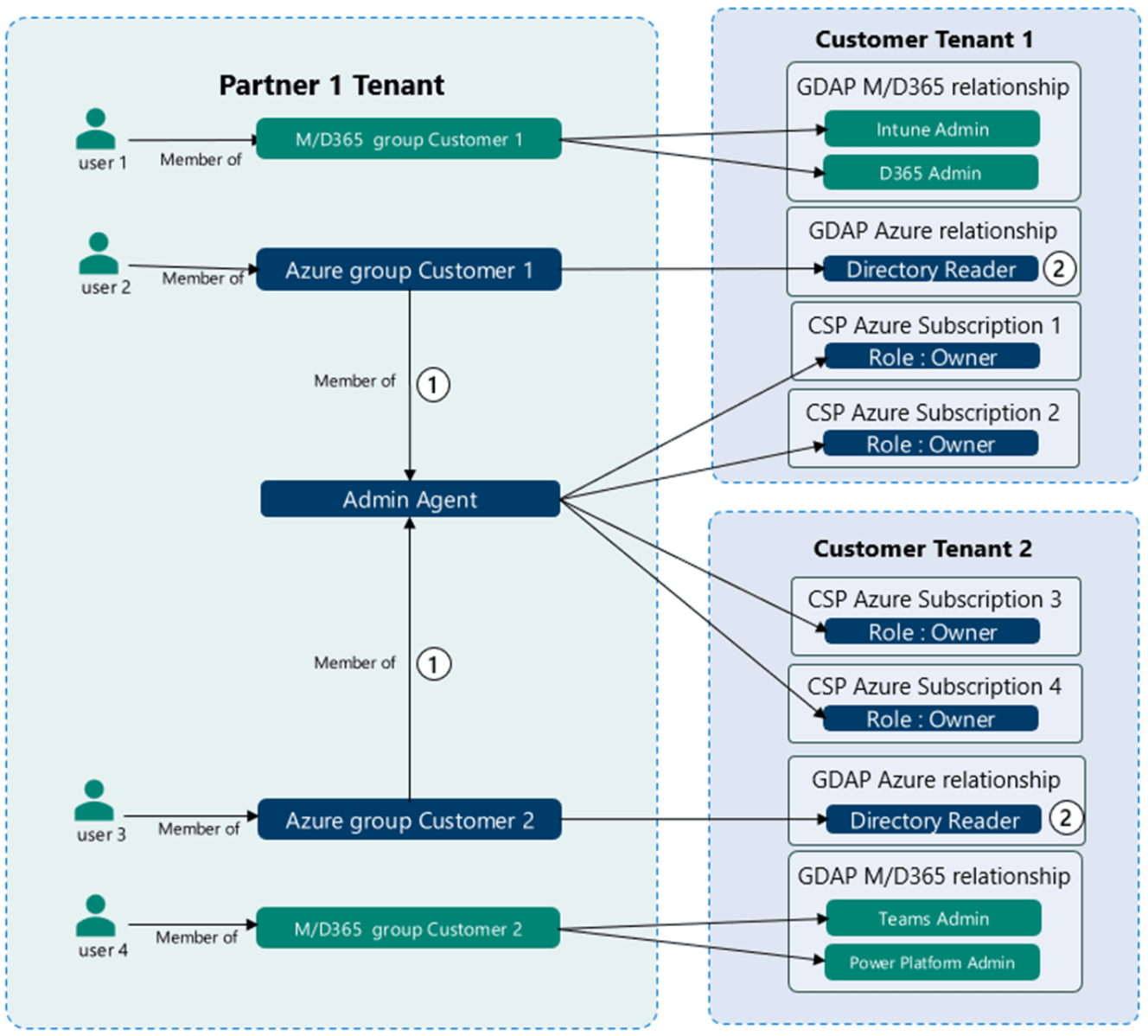
MSP’s Enable GDAP or lose access to your O365 customers
Read More: MSP’s Enable GDAP or lose access to your O365 customersMSP’s Enable GDAP or lose access to your O365 customers, Microsoft has released a new more secure method for Managed Service Providers to perform administrative tasks against their clients called Granular Delegated Admin Privileges or GDAP for short. Introduction GDAP provides a much better Least Privilege Access model as is a core component of many…
Protecting Australian Business from Cyber Crime
Read More: Protecting Australian Business from Cyber CrimeProtecting Australian Business from Cyber Crime, easy title to write and a topic beyond complex to implement for many small to mid sized businesses in 2022, Australia. The secret is that it is not complex to get started on a cyber security journey, it is easy to do the basics and reduce the risk of…
“Okta parses passwords in clear text”, What does that mean to me?
Read More: “Okta parses passwords in clear text”, What does that mean to me?“Okta parses passwords in clear text”, What does that mean to me? This is really NOT an Okta problem but an industry problem – my industry, cloud SSO authentication should always and only be against known “good” Authenticators such as Microsoft, Google, Apple and others for all cloud based SSO. Passwords should never be out…
Follina 0 day – Office lets the bad guy waltz right in, WRTF!
Read More: Follina 0 day – Office lets the bad guy waltz right in, WRTF!Follina 0 day – Microsoft Office Macro protection eaten for breakfast!, those of you who know me, know that I embrace Microsoft Defender as a security tool that is top notch, not just my view but the view of the analysts that report on cyber security as well, here for example with the Mitre Evaluations…
Once the horse has bolted – or detection and response should not be an early stage cyber resilience control
Read More: Once the horse has bolted – or detection and response should not be an early stage cyber resilience controlOr in other words detection and response solutions should not be a first step in a cyber resilience strategy – after the horse has bolted is too late to be worried about how the animal got out of the stable. The Australian Cyber Security Centre does not even list Endpoint detection and Response solutions in…
Zero trust Network Architecture, layers!
Read More: Zero trust Network Architecture, layers!medieval parlance. Unfortunately without adaquate planning and architecture just like castles, ZTNA “Stacks” fall over and sink into the ground.
Zero trust buzzword bingo
Read More: Zero trust buzzword bingoDescribing a host of solutions and practises that are already in-place for experienced security teams and being considered by the many not so experienced security teams looking for guidance, ZTNA is not a one size fits all and the marketing around ZTNA does make this any clearer for business.