From Backup to resilient cyber security
Read More: From Backup to resilient cyber securityIn the Beginning From Backup to resilient cyber security: Best practises for Information Technology such as “Least privilege access”, “Admin account segregation”, “Operating system patching”, “Multi-factor authentication”, even “Patching and updating applications” have been around for many years, undertaken as ritual by many Information Technology departments within businesses across Australia as best practise maintainence, without…
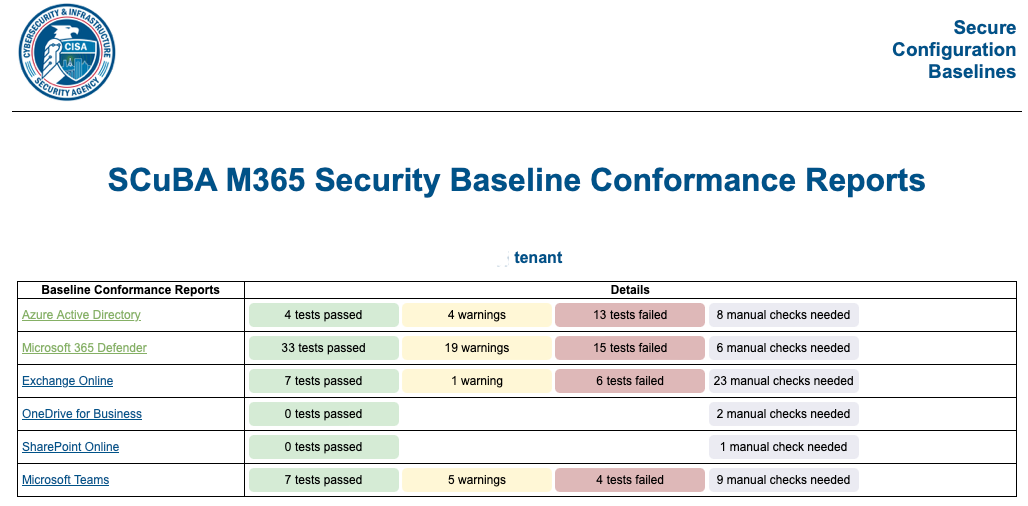
Secure Cloud Business Applications – assess your security
Read More: Secure Cloud Business Applications – assess your securitySecure Cloud Business Applications, assess your security – Best of all it is at no cost and provides guidance on best practise security guidelines for business. When reducing the likelihood of a successful cyber attack we need to break down the approach into various elements, a security assessment such as the CISA SCUBA tool is…