In a Surprise to No one, GenAI is not good at some tasks
Read More: In a Surprise to No one, GenAI is not good at some tasksIn a Surprise to No one, GenAI is not good at some tasks, knowing my experience with Generative AI large language models and their capability to date, it is not surprising to see the Australian government trial ended with a “not quite good enough” (linked). LLM’s are good for basic tasks, not people replacing tasks…
Facebook marketplace scams
Read More: Facebook marketplace scamsFacebook marketplace scams, nothing special about these scams in general, the ‘seller’ will answer your questions and be fairly polite about it, to add some urgency they will say that they have had a lot of interest or that they can not hold the item without a deposit being held. If you state that you…
Add AI to cyber security software, just because….
Read More: Add AI to cyber security software, just because….Add AI to cyber security software, just because…. Not calling out any particular vendor here, but calling out the fact that it has required a marketecture shift to AI is the new snake oil for a vendor to adopt an old technology, Bayesian Machine Learning is nothing new, more details are here about Bayesian ML…
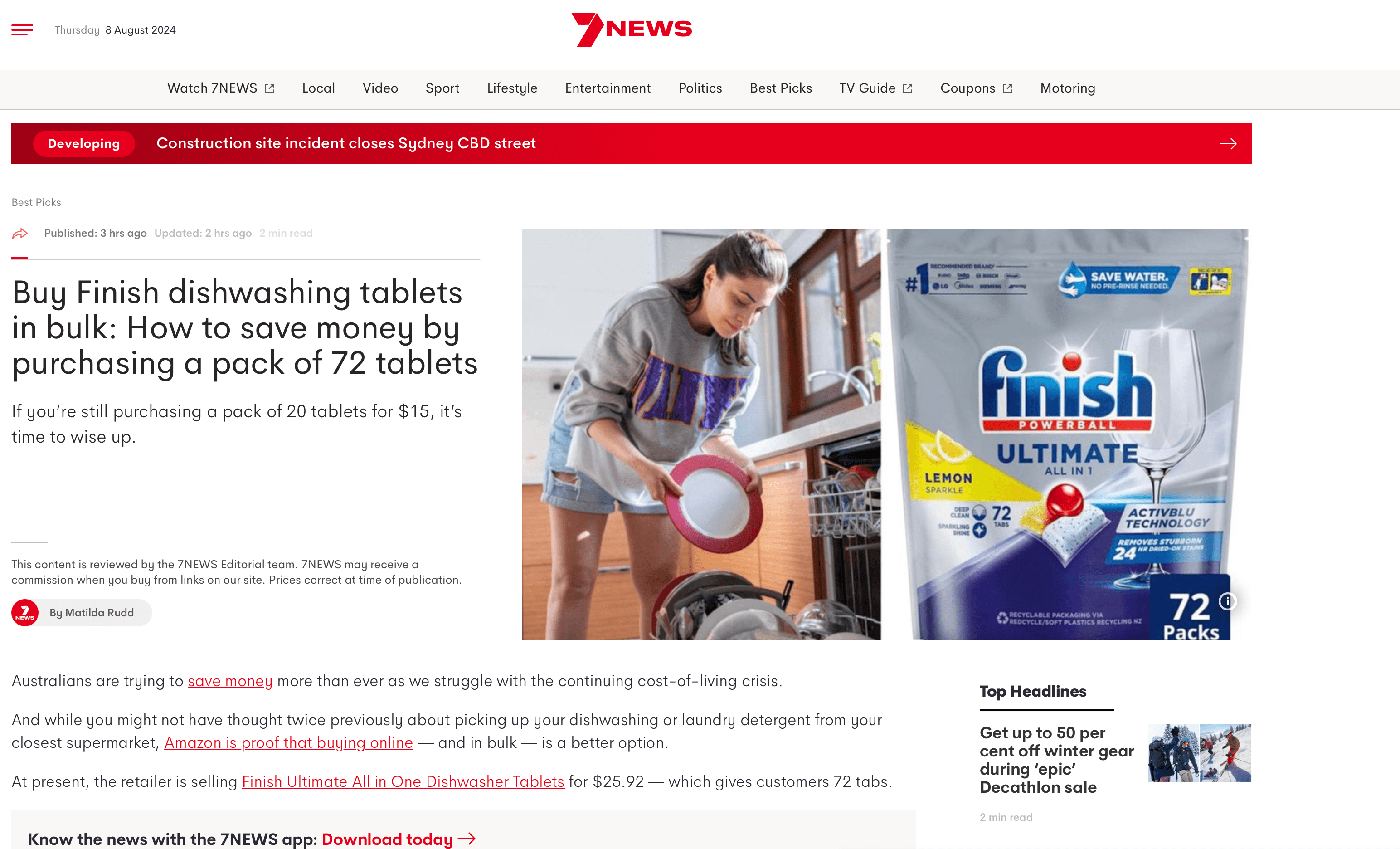
Dishwasher tablets vs Dishwashing powder – Do not be Fooled
Read More: Dishwasher tablets vs Dishwashing powder – Do not be FooledDishwasher tablets vs Dishwashing powder – Do not be Fooled Ever wonder about the price you are paying for Dish washings? Nah me either, happily in the knowledge that I could get Finish dishwashing tablets for cheap from the local “cheapie” shops in Australia I would save big time over what ColesWorth steal from their…
Avoiding a Global outage – By not running the software that caused it!
Read More: Avoiding a Global outage – By not running the software that caused it!Avoiding a Global outage – By not running the software that caused it! In a article this morning ABC journalism competently managed to demonstrate a complete lack of awareness in the topic they were reporting on and a media story was born that has no basis to even exist in this reality, or the next.…
Safeworlds TV Scam is finally being uncovered
Read More: Safeworlds TV Scam is finally being uncoveredSafeworlds TV Scam is finally being uncovered, several years ago I was introduced to an opportunity that seemed “too good to be true”, a chance to ‘invest’ (invest is a term I will come back too) in the next big thing, bigger than Google and Youtube, bigger than eBay (in 2013), larger than Amazon and…
The fallout, Indonesian Ransomware incident 2024
Read More: The fallout, Indonesian Ransomware incident 2024The fallout, Indonesian Ransomware incident 2024, depending on how you look at this it is a bit of a disaster, because rather than simply resolve the problem – it is very likely that the Indonesian Government will want to decentralise their data to avoid any ransomware incident in the future affecting such a large swath…
TeamViewer has No place in a modern business – second breach in a year
Read More: TeamViewer has No place in a modern business – second breach in a yearTeamViewer has No place in a modern business – second breach in a year
No Company needs MOVEit, Tell me otherwise?!
Read More: No Company needs MOVEit, Tell me otherwise?!No Company needs MOVEit, Tell me otherwise?! MOVEit is in the cross hairs again, a second critical vulnerability – meaning it is trivial to compromise. Vulnerabilities in software don’t seem to be managed well by some, this second critical vulnerability should have been discovered and mitigated when doing the requisite post incident activities from MOVEits…