Carrots, sticks and donkeys do improve cyber security, part 1.
More specifically how to Use the ACSC recommendations to achieve cyber resilience augmented with what organisations are already doing well today.
As most organisations in Australia already understand, the Australian Signals directorate Essential Eight is a list of 8, easy (definitely easy) steps to implement to reduce risk of cyber breach by 85%.
Introduction to using the carrot and stick approach
Let us start by explaining the Carrot and stick methodology, it is well known for those of us as old as I, that donkeys used to be a feature of many spaghetti westerns and cartoons. Donkeys are creatures with more than a little bit of “Sass” and determination to “not do” what is requested of the donkey controller – at least in the cartoons.
The Carrot vs the stick is a reference to “motivating this stubborn creature using a reward rather than whipping its behind with the stick to get its compliance. Compliance as cyber security experts know is a great result but is not achievable using a carrot or reward in most cases and the stick, or legislation by government or industry tends to be the only way to achieve this.
Until today at least, because today I want to teach you a way to help your Small to mid sized business leaders understand the importance of building a robust and consistent cyber security program in to the business.
Most of what we will cover can be done without ANY additional software licenses, no software to purchase on top of your existing Microsoft 365 Business Premium license which many of you are using today already in the small to medium business space. Your Managed Service provider may have to help with services to implement some features but the Business Premium license will cover most of what we will discuss in the next 5 parts.
Starting business, cyber security = zero focus
Most of us have wanted to start a business of our own in our lifetimes and some of us (“royal” us) will be successful to forging our own career path with our own small business success.
There are many small businesses in Australia all contributing to keeping clients services and people employed and we as citizens rely on them small too mid sized business to provide a continued prosperous existence.
Small businesses truly are the backbone of the Australian economy, representing more than 95 per cent of all businesses, employing around 45 per cent of all Australians, and accounting for approximately 35 per cent of our economic output.
Commbank
Self starter SMB business leaders have to be good at a few things, good knowledge in their chosen subject areas and tenacity and determination, grit and persistence too!
What they are often not good at is the day to day of maintaining their operation, this is why they employ great people to work for them and add to capabilities where the business owner may not have a lot of knowledge or ability.
Information technology and its poor cousin cyber security (in small business these are one and the same) do not normally come into this hiring cycle until something goes wrong or the employee who “stupidly” put their hand up to fix the printer can not perform their day to day role anymore due to the explosion of printer problems – we have all been there!
The first step towards a cyber security program
This is part one of 5 parts where we will break down the Australian Cyber Security Centre 38 mitigations into bite sized carrots for organisations to determine for themselves what makes sense to their own operation.
The Australian Signals Directorate Essential 8 is a subset of the ACSC 38 and should be the starting point for any small businesses cyber resilience strategy; as you move along the program and implement controls, it becomes more compelling to implement further controls because they make your business more secure.
This can be an excellent motivation to take to you business leaders or clients for improving cyber security and therefore resilience – performing gradual steps to get to the goal, gamifying what is a dry and technical subject to those outside the cyber security industry.
The ASD essential 8
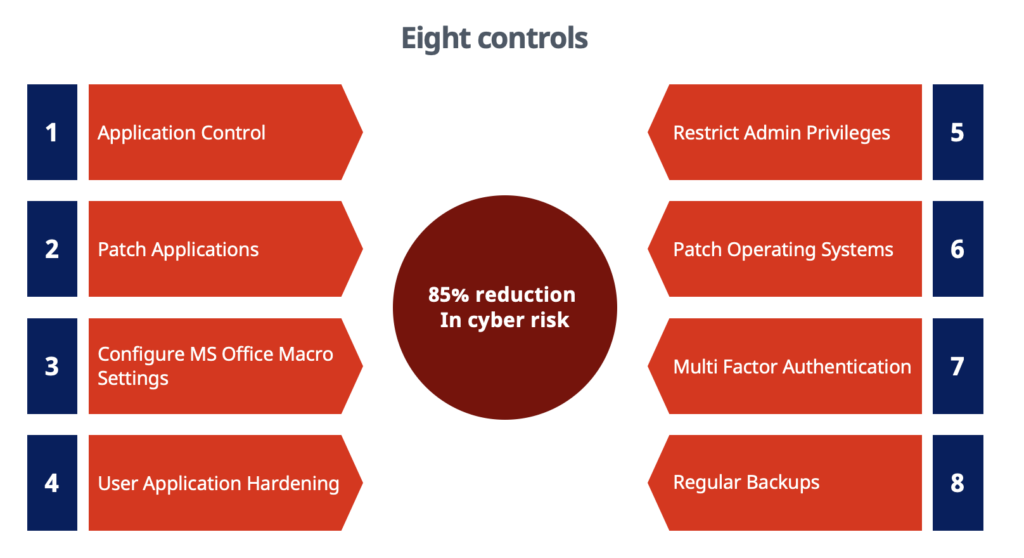
Note: The Australian cyber Security centre provides a great number of resources for organisations looking to enhance their cyber resilience and become more protected against cyber attack.
I have built a series of articles to help a business towards this goal with the help of their Managed Service Provider or a cyber security professional, all without sticks or donkeys and more carrots.
1. Start with Business survivability
Small businesses go “out of business” for a just a few reasons’, many SMB owners that I have spoken with in the last several months have said that they could not survive more than a couple of weeks of complete outage.

A cyber security issue is almost always a ‘long’ incident lasting at least 7 days and more than likely twice this, and sometimes the incident will affect your most critical applications, or all applications.
Cyber incident business considerations
There are many considerations for a small business owner, including:
- Will a customer ‘churn’ to a new provider if their supplier can not service them for 2 weeks/less
- Would the business need to reduce employees because they couldn’t pay, who are difficult to replace
- Can you receive enquiries, new business, support clients during an outage
- What are the implications of data theft? (personal information, sensitive information etc)
Keeping small businesses lights – where cyber security starts
According to Veeam, 58% of backups fail according to this article here, taking the vendor bias out and accepting that a failed backup could be a file share that was missed leading to a reporting fail, the actual number of failures would still be very high.
Extrapolating figures out to how many businesses are not having reliable backups within a 30 day period could also be in the order of 10-20%. If your business is one of the 20% could you continue to operate after a data breach that ransomwares your data or deletes your business apps?
Data protection challenges are undermining organizations’ abilities to execute digital transformation (DX) initiatives globally, according to the Veeam Data Protection Report 2021, which found that 58 percent of backups fail, leaving data unprotected.
Continuitycentral.com
Reliable access to your business data is equal to the companies “life blood”, if a business relies on any “IT” system for their continued operation then they must have a reliable backup of that platform. But also they must be able to recover the data and have a backup system to allow their users to continue operating in the event that this data has been encrypted or deleted.
Mitigation strategies to recover data/system availability
The ACSC 38 mitigations and one of the most critical ASD essential 8 controls are related to backup, this is also where we recommend that your organisation starts the cyber resilience journey and this is for a few reasons.
- You and your MSP understands backup and the importance of this
- It may not be running correctly at the moment
ASD 8 regular backups

Start cyber resilience with backups, check that you run a successful back up each evening, of all your data.
Ask your backup team, how do they currently check that your data was successfully backed up and dis there a second and third copy of all critical data – with at least one copy being offsite and therefore unable to be accessed by an possible active Malicious actor on your network.
- Create inventory of platforms to be backed up, consider inter dependancies
- Make sure Virtual environments are backed up as well as the data if possible, e.g. in addition to backing up a database server ensure that the database itself is backed up to file and logs truncated etc.
- SaaS and SaaS may have vendor backup occurring frequently.
- Don’t always rely solely on vendor backup for critical systems you should always have more than one copy of data.
- Determine frequency of backup required per application.
- Ensure that backup reporting is updated daily and is successful
Note: If you have a managed backup then check with your provider that the backup is achieving the above results.
Business continuity
Although not an essential 8 control, business continuity ‘BC’ is as critical as a successful backup, without BC there is no platform to recover to.
- Create an asset list of your applications
- Create a business continuity plan with all the steps to recover in the case of a disaster – cyber or otherwise. This plan will be a part of your Cyber resilience plan at a later step.
- Plan recovery based on criticality of applications to your operation – what could you survive without for a period of time, consider also dependancies like directory service SSO or Web app needs a database etc in this planning
System Recoverability
System recoverability goes “hand in glove” with Business Continuity, the modern IT landscape tends to be virtualised and recovery planning is simplified because of this.
- Ensure that applications and servers can be recovered if needed and the time required to recover each system.
- Test recoverability regularly, every 6 months at least to confirm that recovery plans are still relevant for your needs
- Look to consolidation and optimisation of application vendors and services where possible to speed up recovery and simplify platforms management.
Malicious insider
Malicious insiders are the people who you trust and who betray that trust for personal gain or maliciousness. It is difficult to prevent an insider from performing an attack on your network because they have access by default. This use case is one that the Zero Trust Network Architecture ‘ZTNA’ aims to address, because within the ZTNA everyone is considered external and a risk to the organisation. This is also a use case for Microsoft Purview Information Protection an inclusion with an M365 E5 license and the various compliance SKUs available with F licenses etc.
When starting out consider some basics:
- Ensure that employees only have access to what they need access to
- Don’t save the payroll xls on the group share
- Plan 6 monthly reviews of user access to data
- Remove Accounts that are not being used: Contractors, ex employees, services accounts as soon as possible, disable and change the password immediately.
- Review whether your business needs to use an Information protection solution, this is easier to implement now than later when the categorisation and tagging of legacy data needs to be also considered and implemented.
Summary, carrot and stick is about motivation not punishment.
In conclusion, to help organisations implement a secure process we should start with a framework. The ASD essential 8 provides this starting point and will help business to become more secure in a measurable way.
- Build a Business continuity plan today – later this will become part of your Cyber resilience program.
- Ensure that your backups and disaster recovery processes are in place.
- Check that backups are occurring successfully every day for all systems.
- Review these plans every 6 months
- Test recoverability every 6 months
- Consolidate application vendors and services where practical, application function overlap means more data to back up, more opex in monthly subscriptions and slower recovery in the case of an incident.
I realise I missed the donkey and there are no sticks because cyber resilience is about positive change.
So without further ado this Donkey is the cutest one I could find on my free images search…

Please contact us here if you would like any help or would like to write with us.
Part 2 (coming soon)





One response
[…] entities, through the Essential 8 cyber security controls which I have previously covered here and here are critical starting points for not just Australian businesses, but all […]