The “Compliance with the NSW Cyber Security Policy” special report released on the 28th October 2021 should be a serious concern to every NSW resident who has their Personally Identifiable Information being “securely” held by a government agency.
Vic, NSW, QLD, SA, NT and TAS could very likely be transposed with NSW and these findings may be the same.

The highlighted above section is most saddening and maddening in equal amounts, private citizens sensitive data is being held by agencies not secured, because the basics of good practise in IT are not being achieved by some government organisations.
https://www.audit.nsw.gov.au/sites/default/files/documents/Compliance%20with%20NSW%20Cyber%20Security%20Policy%202021.PDF (also downloadable at the end of this article)
As this document has been released, it is irrelevant that these agencies are anonymous. Each and every NSW (most likely Australian government agency) will be a target for attackers, as a nation we are basically being “put on notice”.
Maybe Australian really is the lucky country and malicious actors have not noticed we are not prepared? seriously though, there are nations who want nothing more than to access to as much government data as they can gather.
Will this be the start of a flood gate of cyber breaches against Australia?
If your details get stolen – that is serious enough, right? well how about…..
A malicious hacker wants to change your data? What happens when someone who doesn’t like you pays an attacker to change your data: Your drivers license suddenly has additional “penalty points” added to it and you are arrested for driving while disqualified; or, your marriage status is changed; or, your children exam results are altered?
This is a small number of possible scenarios of what could be done with your information, in most cases the agencies who reported do not even have a complete backup and recovery strategy.
A baseline, not an aspiration (ASD 8)
You may be immediately thinking, “Cyber security is hard, I am not surprised that NSW agencies are lacking sophistication against attack”.
The lack of adherence to the ASD 8 is not a cyber security complexity problem, it is either a mis-management or it is a mis-communication between Information Technology at these agencies and the Stakeholders of these government agencies.
Where is the education and communication between Tech/Security and Management?
The Australian Signals Directorate (ASD) 8 was initially released in 2017 and agencies have known since this time that they need to improve their infrastructure maturity and build cyber resilience into their operations: ASD 8 link.
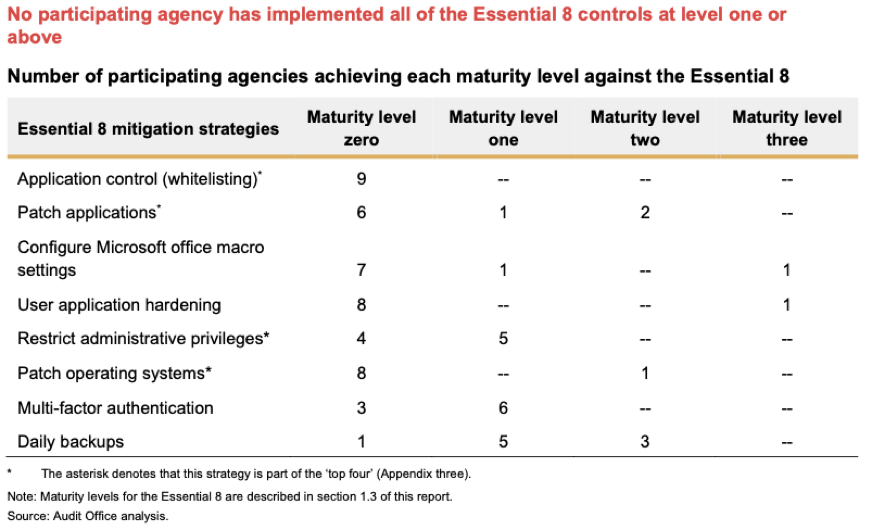
The “The CSP requires agencies to report maturity against the Essential 8 using a four point scale based on the ACSC maturity model. The ACSC maturity model for the Essential 8 has been revised a number of times, including a significant revision in July 2021. At the time of the audit, the broad definitions in the CSP for each maturity level8 were:
- Level Zero: Not meeting the criteria for Level One
- Level One: Partly aligned with the intent of the mitigation strategy
- Level Two: Mostly aligned with the intent of the mitigation strategy
- Level Three: Fully aligned with the intent of the mitigation strategy.
Out on a limb here, the ASD 8 is an easy to implement set of basic or entry level requirements that every business in Australia, even every home user should be already be practising as a part of good hygiene.
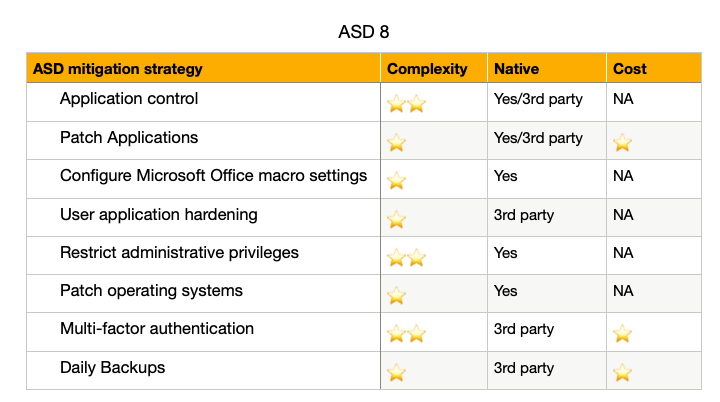
The ASD mitigation strategies are tasks that an Information Technology (IT) team should be managing on an every day basis, planning and working towards full compliance; starting in 2017, but already being managed capably in 2017 as a mature IT organisation tends to do.
None of the recommendations from the ASD are complicated, almost all of the recommendations are required for a business to operate in a normal day to day scenario, these are NOT cyber security practises, they are simply “good practice”.
The question that may be asked is what happened to the IT teams in these government departments, why are normal operational activities not happening as they should in a mature business?
The solution
The solution is not a cyber security one, each organisation does not need a cyber security expert to solve, they need a pragmatic and patient project manager and project implementation team.
The solution to Australian government organisations obtaining a minimally viable platform is fairly straight forward and it is cheap and easy for most of the ASD eight.
What the ASD recommendations state as necessary are primarily native controls, built in the respective applications and platforms. Even if these government organisations focus on the major platforms they will at least find they can comply with Level zero and Level one maturity, close or exceeding Level two maturity – remember that zero of the reporting agencies achieved level 3.
(1 ⭐️ = easy, cheap ⭐️⭐️⭐️⭐️⭐️ = complex, expensive)
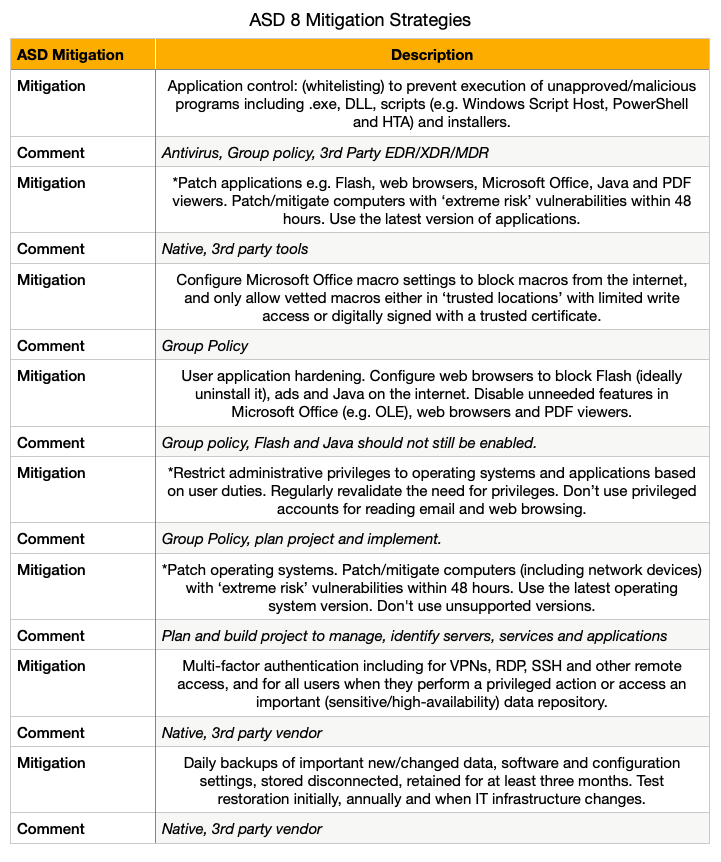
The table describes the mitigation and commentary, there are many ways to solve each Mitigation.
For the sake of this document, the writer is going with the most cost effective approach for each. These mitigation strategies are: 1. not new and 2. they do not have any license cost in most cases.
- Using the ASD 8, break these into 8 work streams.
- Rank most critical (Top 4) by easiest to most complex, then the remaining 5 – 8
- Calculate cost to implement.
- Evaluate existing personnel – capability to implement solutions
- Evaluate existing technology coverage of controls (Native, 3rd party)
- Set objectives, time lines and minor/major milestones
- Communicate to executive team: problem(why), plan/budget/resources needed
- Execute
Within 12 months, your organisation will be a star and so will your team who successfully implemented the most critical controls for a modern organisation.
In Summary
As citizens, you should be concerned with the current security of your information. The question of who is managing the implementation of these fairly basic mitigation strategies should be a worry to everyone who has entrusted a government agency to store your personal data, realistically you have no choice but to let these agencies have your data.
The ASD 8 could be easily implemented in 12 months by all businesses across Australia, let alone the NSW government organisations in this report.
The next report is due in less than 12 months, let us all see just how quick our public services can get up to speed and start to protect your information in a secure and responsible manner.






Leave a Reply