Or in other words detection and response solutions should not be a first step in a cyber resilience strategy – after the horse has bolted is too late to be worried about how the animal got out of the stable.
The Australian Cyber Security Centre does not even list Endpoint detection and Response solutions in their Essential 8 mitigations, instead the ACSC provides a less than stellar statement stating:
| The ACSC has witnessed the benefit of EDR software deployed to user computers, especially before a targeted cyber intrusion occurs, that logs which programs ran (including individual processes and DLL files), what changes were made to the Windows Registry and the file system, and what network connections were attempted and established. |
Strategies to Mitigate Cyber Security Incidents | Cyber.gov.au
This is because detection and response solutions are only somewhat successful, “witnessing benefit” is not confirming usefulness.
With any business or corporate there are only a few things that are critically important and it is not the majority of the assets as described in the Zero Trust Network Architecture. Budget should be first spent on preventing what is business fatal from occurring, which is the theft of information or data – thereby ensuring business continuity.
Organisational value
The value of a business boils down to very few parts (if I have missed any then apologies, I am not a business expert):
- Intellectual Property (IP): documents, plans or the secret sauce that creates your competitive advantage.
- Capital: money in the bank or owed to the business or the cash that lets you operate.
- Customers, products, services: upcoming work, active projects, products.
- Employees, the resources that allow you to have a successful business
With any cyber resilience strategy the goal therefore is to protect the data at all times and to provide continued business operations under any circumstances, in our case these would be related to cyber incident.
Ensuring that a business can operate successfully and continue in the case of a cyber incident “post breach”, primarily without loss of its critical value: IP, Capital, Customer details and employees is what cyber security professionals must be doing for organisations.
We must be cognisant that for all the flash marketing being targeted at us as professionals for cyber security tools, as well as the many Account managers telling us that we will be breached if we do not buy their product, our goal is protection of data first and to be fair, it is a bit boring!
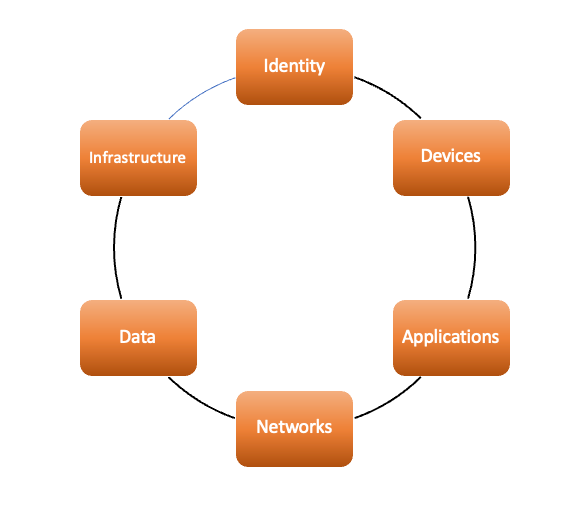
- Within the cyber security industry we define asset classes to be protected, the above is from the Zero trust Network Architecture model but there are many other models with a similar set of assets.
- Identity – you and me
- Application – the conduits to the data
- Data – the critical value of the organisation
- Network – the mechanism used the connect all the parts together
- Devices – what the user accesses the application with to get to data
- Infrastructure – houses the applications and the data
Data = Business (life, death)
All other assets can be made redundant or rebuilt, except data – data may be restored but it can never be made private again after being accessible on the Dark web. As the Intellectual property (data) of a business can not be “un-stolen”, “de-exfiltrated”, “re-secreted” therefore Data must be the most important asset to secure for any business where their IP is critical to their operation.
The problem with detection and response
The problem with detection and response products and marketing is that although the valuables are stored on the assets, detecting and responding to the assets being attacked does not address the most significant problem for the client: “What was stolen” or “what did the malicious actor steal”.
Is looking for a water leak in “plumbing”, where an organisations cyber security should be focused? Primary controls must be pro-active, so that data can not be exfiltrated even during a breach.
Endpoint detection and response solutions do not provide protection from cyber breach; early enough or at all to prevent data exfiltration; and worse still, if the malicious actor is an internal disgruntled employee then the Detection and response solutions will provide no alarm whatsoever making an Endpoint Detection and Response tool irrelevant.
It is about the data
Ransomware without exfiltration was 2020 and earlier, now it is 2022 and ransomware actor add the additional step of exfiltrating data so that it can be sold for profit if the ransomware’d client decides not to pay to recover their encrypted data.

The point in the image above, “Malicious insiders” are a risk as called out by the Australian Cyber Security Centre or ACSC in 2018 and breaches based on employees doing ‘inappropriate’ things have already been implicated in the Microsoft and Okta breaches in 2022 and will continue to increase as “payment for credentials” type threat actors continue to advertise they will pay for access.
In 2022 and beyond, focused end point and extended detection and response products are NOT suitable cyber security mitigation solutions as a primary control or in isolation for an organisation to be cyber resilient, detection and response tools will not help in the most important aspect of business: protecting, and preventing data from being ex-filtrated and by a malicious actor or sold on the dark web for profit.
Keeping data where data should be is the first step, preventing a malicious actor or malicious insider from being able to send this data out from the business systems. If this fails then determining what data has been exfiltrated is the next important step to complete – not what machines are compromised. Knowing the extent of a data breach allows legal and the board of directors to quickly provide a message to market and allay the fears of clients and shareholders quickly.
And this is before we consider an accidental breach of data, where an employee emails the wrong spreadsheet externally, which is still one of the most significant sources of cyber breach in 2022. Another area where an detection and response solution is not effective. The reality is that cyber breach due to an actual cyber attack in 2022 is still tiny, a fraction of a percent.
The solution
A business relies on its Intellectual property, customer lists, financial assets, therefore they need to protect this sensitive information from being accessed by the wrong people and in the case where the wrong person does gain access, prevent the data being exfiltrated and usable.
Some tips for this are:
- SaaS solutions by the major vendors are more secure than your on-premise infrastructure, without question.
- Detection and response to a cyber incident is not sufficient for securing corporate assets: Detection and Response is reactive, there is no element of true protection in E(X)DR, EDR agents react to a problem using ML training models.
- Data governance and Information protection is more critical than detection and response in a business today, the use of an information protection strategy and solution goes much further than a detection response tool, in that it protects the organisation from malicious insiders, accidental data exfiltration as well as cyber attack (when properly configured) through a Cloud Access Security Broker or Secure Access Service Edge solution/s.
- Look at data encryption products and solutions to ensure that data even if leaked, is not usable
- Categorise, classify and tag documents and data incase of data leak
- Look for software vendors who can provide the telemetry from many sources including Information Protection, Data loss prevention platforms etc, AWS, AZURE, Google Cloud, On- Premise legacy, End Point devices, Directory, Network etc.
Just as calling the fire brigade to ask them to put out a house fire, it is too late, the damage has been done whether by flames or by exfiltration of your corporate data with a cyber incident, detection and response solutions in isolation can not protect your organisation adaquately.
If you would like assistance from us please click here: