CVE-2023-23397: Microsoft Outlook Vuln: elevation of privilege vulnerability leads to NTLM credential theft:
Very quick and short post today, I have already been contacted today around mitigations for this vulnerability and wanted to get some quick steps out early incase your business is unsure how to check whether you are at risk. My post assumes that you have Microsoft Defender for Business or Defender for Endpoint Plan 2 implemented and working correctly.
With MDE and MDB it is easy to determine the software running on your managed devices and let me show you how, as well as how to use your 365 Defender portal to see what Threats are being actively exploited in the wild, this ensures that your Security team are working on the highest risks first and correctly prioritising your efforts.
Defender 365
Firstly if are a Microsoft M365 client then you have access to an amazing free tool to consolidate all your Threat hunting and analytics efforts called M365 Defender, you must be familiar with this tool and it should be a daily view for your sec ops people.
Go to Defender 365 here
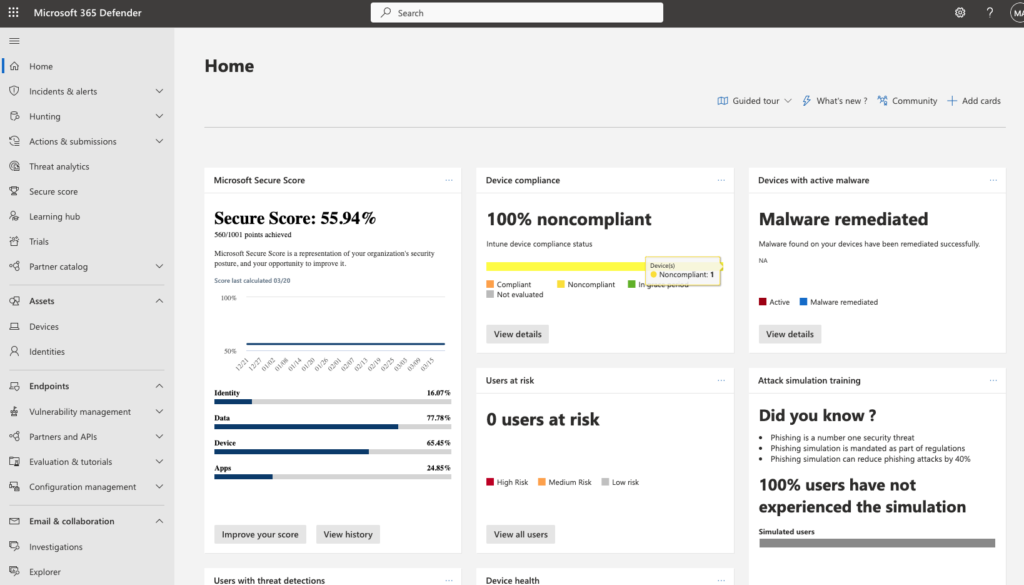
The above view is the Home Screen for Defender 365, here there is an abundance of information to help your organisational security.
Most important on this Home Screen is your “Secure Score”, yours should be at least 75% to start with and the Australian Victorian government recommend 85% as a good baseline.
But the Secure Score is for another day, today I want to focus on determining whether you have vulnerable versions of Outlook (2019 and earlier).
Choose the Threat analytics blade from the menus on the left, if you have not been here before then after my blog post you will want to check here at least every week for updates.
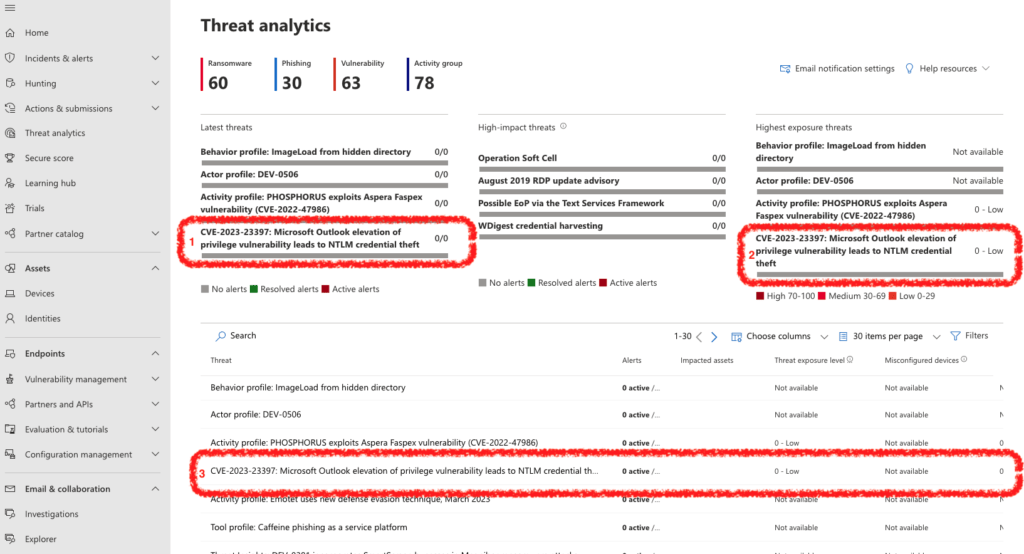
Above in my Threat analytics blade there are three important elements to point out.
- Latest threats being found in the wild, these are the threats that you need to keep your attention on to determine how broadly they become exploited and organisations are targeted.
- Highest exposure threats, these are the threats that have the most significant risk to businesses right now based their severity as well as their usage in the wild, in other words patch, isolate or otherwise mitigate Immediately.
- Most important is how do these affect my organisation, what data has Defender for Endpoint, Defender for Identity, Defender for Cloud Apps, Azure AD identity protection and Defender for Office 365 collected to determine what devices and applications are vulnerable in our business.
For my new tenant (my prior tenant has been decommissioned due to a 12 month limit), I currently have no devices susceptible to CVE-2023-23397.
Selecting the vulnerability will provide more details about the threat in my environment across all the platforms I have secured with Microsoft Defender, this is the power of eXtended Detection and response (XDR) with a comprehensive platform:
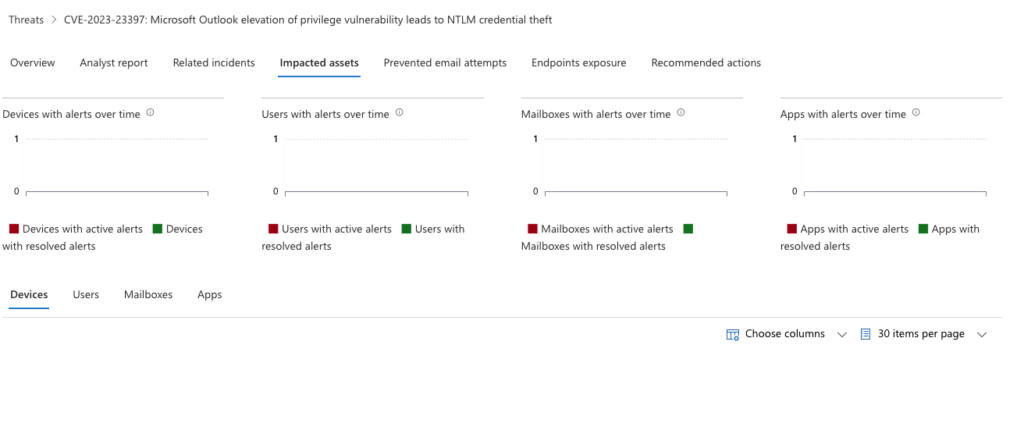
Please take a look at your Defender 365 interface today, some options are not available depending on your licenses but I can assist with this if you need help.
Mitigations
Some good mitigation advice from Practical365 is below:
PowerShell script (CVE-2023-23397.PS1) runs against on-premises and cloud servers to check if items contain a property that’s populated with a UNC path. The audit mode of the script reports what it finds in a CSV file that administrators can check to decide which of the reported items to remove from mailboxes. Running the script in clean-up mode permanently removes the offending items.
- Blocking TCP 445/SMB outbound from your network to stop the NTLM traffic.
- Patch Outlook with the security updates available from Microsoft. If a security update isn’t available for a version of Outlook running in your organization, update Outlook to a supported version. This action is your number 1 priority. If vulnerable Outlook clients remain active, your organization is open to exploitation.
- Microsoft recommends that you consider adding on-premises accounts to the Protected Users Security Group. Windows 2012 R2 and newer domain controllers support this group, which prevents the use of NTLM as an authentication method by group members. Microsoft warns that adding everybody to the group might impact applications that require NTLM, so this is a tactic best used for selected high-profile accounts. Be sure that you read the documentation for the Protected Users Security Group before you use this tactic.
Summary
As is regularly the case doing the basics right will keep your organisation safe from this vulnerability, the ASD essential 8 and the Singapore Governments Trust Mark both recommend that software is patched frequently and soon after patches are available.
Despite this CVE-2023-23397 is a significant vulnerability if your business still has old versions of Outlook in the wild so if you need to perform some “out of band” remediation work then look at your patch management processes moving forward and your asset inventory platform to make certain you are getting all the data you need to resolve this.
- Make sure you also consider devices that might not be present in the above reports, servers for example may be running an old version of Outlook.
- Patch Applications regularly, this is basic security posture activity
- Look at Attack surface reduction rules within Defender for Endpoint and Defender for Business to reduce your attack surface for Zero days.
Please reach out to me if you need any assistance with this or other challenges, I work for Crayon and my goal is for all organisations to have at least a moderate security posture to build apon.
Feel free to email me at: [email protected]





