In the Beginning
From Backup to resilient cyber security: Best practises for Information Technology such as “Least privilege access”, “Admin account segregation”, “Operating system patching”, “Multi-factor authentication”, even “Patching and updating applications” have been around for many years, undertaken as ritual by many Information Technology departments within businesses across Australia as best practise maintainence, without a second thought.
These principles today form some of the basics that are known as best practise cyber security and make up a part of modern cyber resilience.
Yet a number of factors have conspired over the to make what should be best practise and basic security posture and cyber resilience a science that seems overwhelming for many.
Therefore to obtain a level of cyber resilience businesses need to start from the basics, the basics that extend regular tasks such as daily backups to include cyber resilience with these goals:
- Protection against opportunistic cyber events and minimisation of affect in the case of an active cyber attack.
- Ensure that the business can recover quickly in the event of a disaster, data leakage or intrusion incident (cyber or otherwise)
- Minimise the extent of an incident, disaster or otherwise
- Ensure that your data is private, consistent and secure
Breaking cyber security down it comes down to the following elements:
People, Process and technology in this order.
- People; get the people in the business onboard with why they need to implement security controls.
- With big name breaches such as Medibank, Optus and Latitude this is easier than ever before.
- Your people have opinions and ideas about what is most important and preferences and biases.
- Process:
- What are the critical systems?(CRM, ERP, Booking etc)
- What is the likelihood of an incident affecting these platforms, what is the cost of an incident and what is the cost to secure
- Calculate cost to make asset resilient
- Business continuity planning, Incident response planning, damage control planning
- Technology:
- The cyber security software market is awash with solution choices and therefore making the right decision is complicated and a mistake is costly.
- Without a framework for security controls, costs will quickly become overwhelming.
- Technology debt is the enemy of cyber resilience, often preventing organisations from being cyber resilient through making decisions in isolation rather than strategically.
This complexity has led us to the current day where in Australia Enterprise organisations are being breached with alarming frequency because cyber resilience is not the consideration it needed to be for management boards and the respective business owners.
Recent examples:
- Optus: A breach through inadequate authentication to secure data access via an API, no auth was required for an API used to return customer information from the public internet.
This breach was further complicated through Optus not having sufficient data governance processes in place to remove data once it was no longer needed, e.g. when a customer churns away and the data needed to be removed.
https://www.upguard.com/blog/how-did-the-optus-data-breach-happen
- Medibank: A breach due to limited Identity security, Multi-factor authentication was not enabled and the model of least privilege not in place.
In addition to this a lack Data governance led to more data being able to be illegally exfiltrated than should have been.
https://www.upguard.com/blog/what-caused-the-medibank-data-breach
- Latitude: the latitude breach is a third party supplier breach and information is still being brought to light but an employees credential was used to access data containing citizen data on third party systems, including drivers license scans.
A third party supplier breach is a very common form of attack, at least one of your employees has a credential for sale on the dark web, they most likely even used their business email address and business password to register with this third party website.
Dissecting the three breaches above from the publicly available information and applying cyber security insights leads to a single alarming conclusion, these three organisations would have been secure had they done the basics right, this is known as a “secure posture” and is critical in all business from the smallest to the largest enterprise to ensure Confidentiality, Integrity and Availability of the core business asset (Data) – the CIA triangle represents this extremely well.
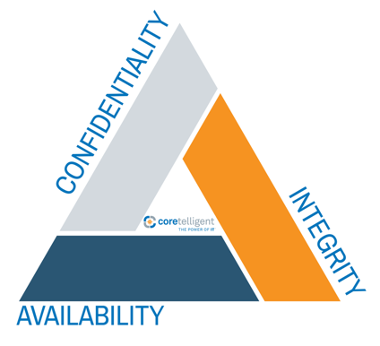
https://www.csoonline.com/article/3519908/the-cia-triad-definition-components-and-examples.html
Perhaps even more critically this “Secure posture” and securing a businesses data from criminal actions forms the basic principles for an organisations ongoing and improving cyber resilience https://en.wikipedia.org/wiki/Cyber_resilience.
Why now? Why is Australia being targeted?
Criminals do not care about who they hurt, being connected only by an I.P address completely removes an attacker from their victims, if the affected person is not known then I can sleep at night. Besides this attack is against a company right? Who gets hurt when a company is attacked? A simple mind will assume, the company loses money yet has insurance to cover it.
A more nuanced answer is that “it depends”, a cyber attack and a data exfiltration can personally harm citizens, with drivers licenses being stolen all the data needed to perform a financial transaction is available, with a medical record a citizens reputation could be completely decimated with a past revelation. Besides these data based attacks is the immediate Spear phishing attack where criminals are successfully stealing company funds by gaining access to a users mailbox and impersonating a request for a invoice payment, I have personally been involved in a couple of these in the past 6 months where the money lost was over $30,000 Australian dollars in the highest case.
To push this point further, the following is a recent excerpt from an interview with a criminal who claims to have been a part of ReVil, the hacking group that “may” be responsible for the Medibank breach.
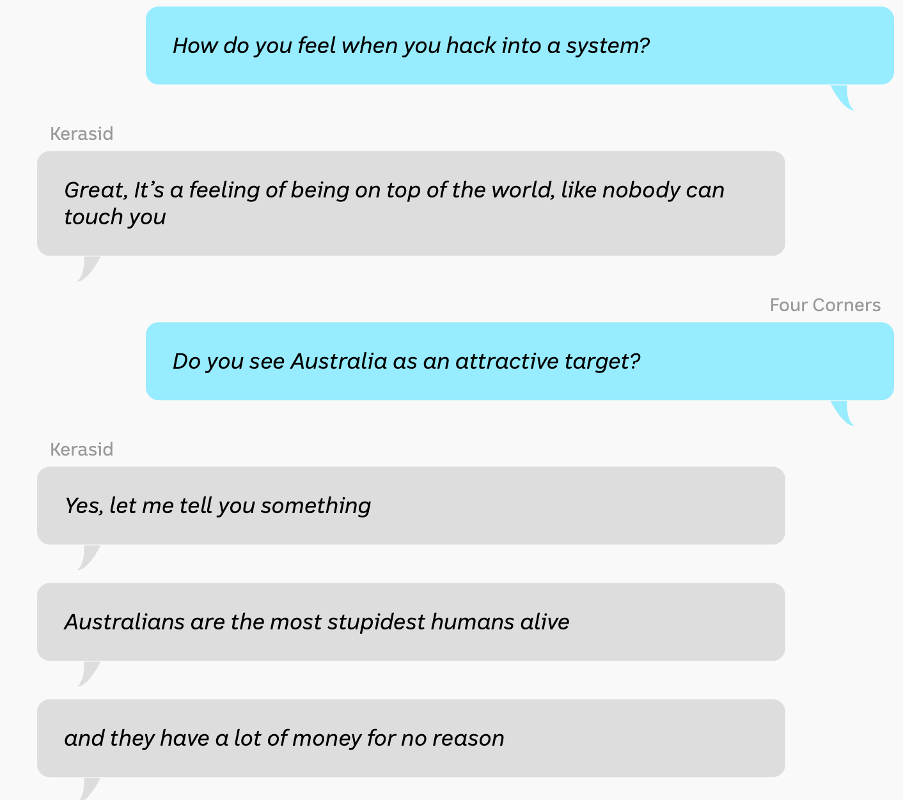
Australians and Australian businesses are wealthy by international standards and our businesses have a less than suitable security posture through a combination of lack of regulation and a fairly “friendly” Australian attitude in business.
Criminals such as the hackers we face today do not share our values, they do not care about people, they do not care about society, they have few motivations: Greed, pain and notoriety.
This leads to today in April 2023 where Australia is the new “land rush” for criminals, and Australia is now the number 1 location for cyber security breaches with 7,400 breaches per 100,000 user accounts:
Your business will be a target either opportunistically or targeted, no doubt, because some of your corporate email addresses are already in a dark web data cache available for purchase: your employees are on Linkedin (breached), yahoo (Breached), Optus, Medibank or latitude and in some cases they used the single password that they can remember without writing down.
Opportunistic will likely be an email spray attack sent out across a collection of email addresses looking for a 0.1% response rate.
Targeted will be when your organisation is known: Australian government, Universities, Medical providers, Critical infrastructure providers where an outage causes citizen harm and unrest leading to wider problems.
Calculating risk
As alluded to earlier cyber resilience is about ensuring that your business can keep operating in the case of a cyber attack, or recover rapidly if business continuity is affected, therefore always consider your reliance on technology and the systems you have in place to determine the likelihood, risk and implication of any of your core business systems being unavailable.
An example of Risk vs cost vs likelihood is the Coles supermarket outage in 2020: https://7news.com.au/lifestyle/shopping/coles-registers-suffer-nationwide-technical-failures-leaving-shoppers-unable-to-pay–c-1376329
The effect of this outage is immediately calculable in lost revenue, consumers unable to purchase goods for 3-4 hours from their local Coles, would have immediately moved to Woolworths or Aldi’s to purchase those items.
How would a situation like the above play out for your business, the cost might not financial, it might be reputation, the loss of customers, negative health effects, Significant customer outages of impact.
What business must do as a minimum-security posture will depend on many factors:
- Size: Small business needs to be resilient but may have a more basic posture than a hospital with critical functions, or an enterprise.
- Industry: Regulated or not, government or private have different needs post a basic security posture.
- Regulation and recommendations such as the Australian government provides for government organisations such as ASD 8 and ISM or ISO 27001 for international businesses add their own requirements.
- Recognition: Many cyber-attacks are opportunistic, starting with a credential “pair” purchased on the darkweb and a credential use, or an email phishing attack.
- If you are a well-known brand or a critical infrastructure or government org then your business will be a number one target for criminals or State based hackers paid to compromise foreign governments.
Steps to move from Backup to cyber resilient:
- Follow a framework, all frameworks fall into levels of maturity. These levels of maturity allow for an organisation to self-designate what they may need to achieve and at which level of capability.
Following a framework places your business needs first and vendor technology second by mapping security controls, the benefit to the business and then
Each framework has similar mitigations due to the fact that cyber breaches tend to happen in the same way. The following are not in order of preference:
- Australian Signals Directorate Essential 8 https://www.cyber.gov.au/resources-business-and-government/essential-cyber-security/essential-eight
- Zero Trust Network Architecture https://pubs.opengroup.org/security/zero-trust-principles/
- Center for Internet Security https://www.cisecurity.org/controls/v8
- National Institute of Science and technology – Cyber Security Framework https://www.nist.gov/cyberframework
- Use the best people you have and the best that you can find, within the business there are employees looking to advance their careers and even for small businesses an internal resource needs to be responsible for the cyber security resilience of the business.
- Seek out diversity as the least likely candidate could be your star cyber security leader someone who can learn and pickup cyber security practises quickly.
- Utilise good Partner organisations, some will offer full VCISO services through to security control implementation but leverage these capabilities to strengthen your cyber resilience.
- Create processes and procedures for Incidents, leverage your existing Backup and business continuity plans and extend these to cover cyber security incidents and events, such as Incident response, new threats (software vulnerabilities), 3rd party supplier breach notification, notification process.
- Assign a resource to be responsible for this to ensure that it is completed.
- Ensure that all employees are aware that they work in a no blame environment, in the case that a user clicks on a phishing link or malware, then you want to know this as soon as possible.
- Assess your systems and applications (assets) for criticality, potential for cyber attack and cost to secure, build a risk register from this information. Assign costs for protecting vs each risk and impact if breached.
- For a first glance, consider the applications that the key operators in the business need to utilise every day for a starting point.
- There are tools and consultancies that can assist with the collection and also the technical knowledge of what needs to be done to secure the various platforms.
- Your cloud provider does not secure your Identities, Devices or Data against a cyber attack, typically they will be able to restore 30 days of data in the case that this is necessary, this is not sufficient in any but the smallest businesses.
- Implement technical controls, now you have the people and the framework, align these to your assets.
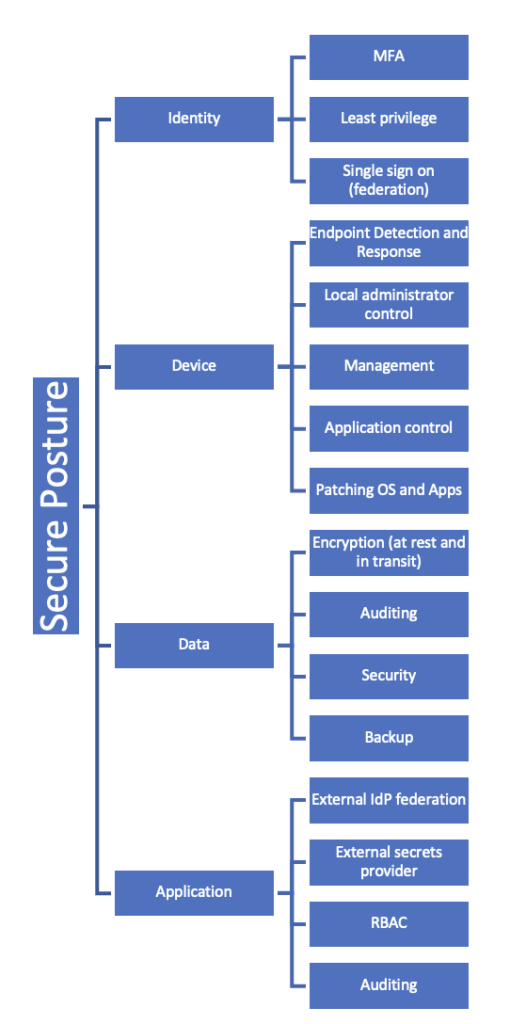
Larger and legacy organisations will also include Infrastructure and Network as Assets to secure.
The above image is an indication of some of the security controls that cyber security frameworks will recommend as required for any organisation, this list may have different controls and order of implementation.
- Iterate, very few organisations have the resources or capital to implement everything that is needed for cyber resilience at the outset. Even if a business could implement every control at once there will still be evolving gaps as criminals get smarter and as a business onboards new applications and processes / people.
- Plan cyber resilience as a part of the ongoing management of the business, leverage your cyber security partner and resources to ensure that you are upto date with the latest threats and risks and can respond appropriately
- Budget for ongoing cyber security activities either internally or externally and leverage vendor assessments where funded when they align with your goals. The outputs of these can provide insights into the unknown unknowns and providing there is no compulsion to purchase they can provide good value “free consulting”.
Summary: From backup to cyber resilient
The evolution of the Information technology age has brought about vast change, many for the better and some for the worse. Business has evolved from on-premise to cloud due to more plug and play, more flexibility, better scaling and more application availability rather than Bespoke, along with this has come more complexity less visibility and more potential for a cyber attack.
Your organisation can get to a strong secure posture rapidly by engaging on the journey early, you will be the target of a breach, this is no question, you must ensure that your business is as secure as practical and to get here as quickly as is possible.
There are many ways to achieve a secure posture, from security controls and solutions to help your organisation gain cyber resilience but start early, engage the appropriate cyber security specialists to ensure that your business is doing the right things first.
- Adopt a cyber security Framework
- Use smart people inside your organisation and from partners
- Create processes to handle any cyber security activities
- Assess your platforms and build an asset register
- Implement technical controls
- Iterate, improve and repeat
First step may be to engage your technology partner, use their cyber security knowledge and expertise learnt through dealing across many similar clients to your industry vertical as a starting point.






One response
[…] to ensure all Australian business are cyber aware and cyber secure, starting with assessing your risks here against cyber crime and then how to do it here these steps may be too advanced for your business so […]