Follina 0 day – Office lets the bad guy waltz right in, WRTF! those of you who know me, know that I embrace Microsoft Defender as a security tool that is top notch, not just my view but the view of the analysts that report on cyber security as well, here for example with the Mitre Evaluations for 2022 where Microsoft Defender for Endpoint P2 shows its ‘chops’ and performs like the participants on “Dancing with the Stars”, not the ones who get booted early on, of course!
UPDATE: Defender for Endpoint has been updated and can block Follina (01/06/2022)
Introducing Follina, infecting your PC today
Follina is a new Microsoft Office code execution Maldoc with a twist, the twist being that the steps put in place to prevent exactly this type of breach do not actually prevent it from working as of the 30/05/2022.
The Follina Vulnerability is an interesting one as the Maldoc is not detected by Microsoft Defender for Endpoint nor is it captured by Microsoft Office even with Macros disabled, as Follina is not running a macro at all. Follina relies on Microsofts own Diagnostic tool MSDT for execution.
“A remote code execution vulnerability exists when MSDT is called using the URL protocol from a calling application such as Word,” the advisory stated. “An attacker who successfully exploits this vulnerability can run arbitrary code with the privileges of the calling application. The attacker can then install programs, view, change, or delete data, or create new accounts in the context allowed by the user’s rights.”
Arstechnica
Microsoft Defender for Endpoint P2 (Endpoint Detection and Response) misses this malware and likely so do many of the Endpoint Detection and response ‘EDR’ solutions out on the markets as of the 28/05/2022, I have previously written about EDR as not being the be all and end all, despite what the EDR sales person tells you.
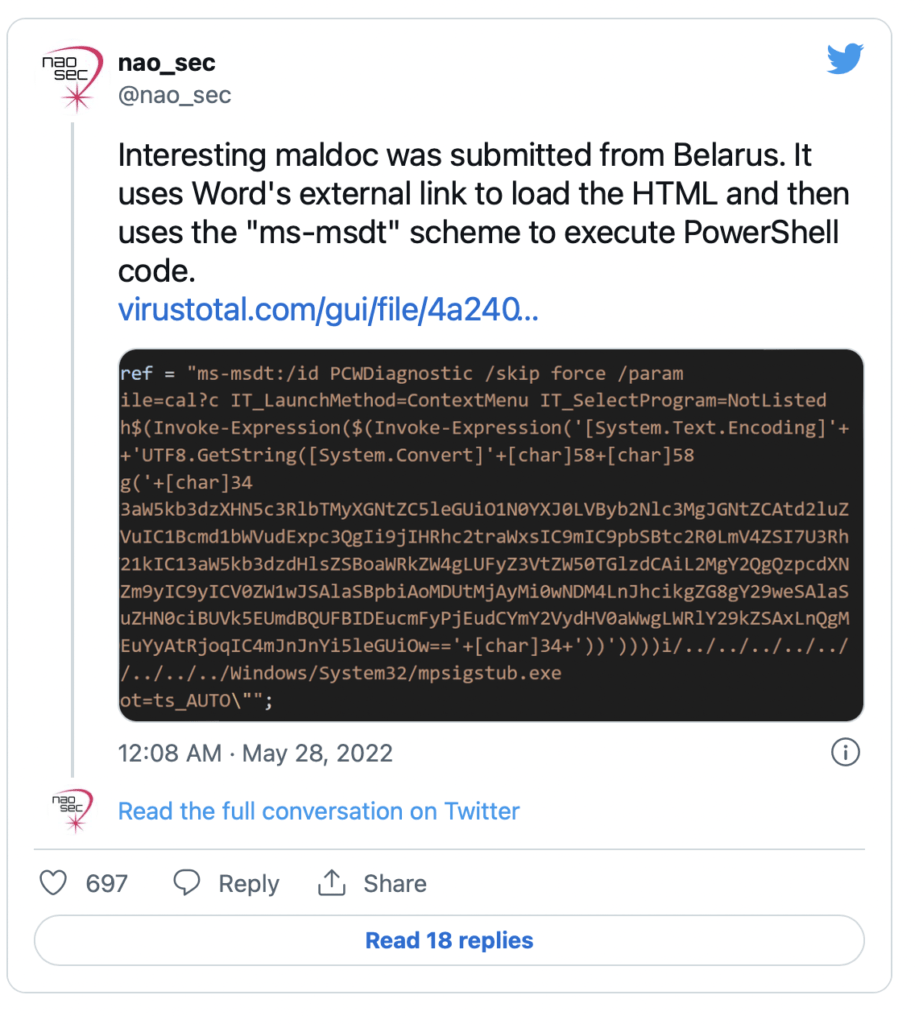
Follina is tricky in that it does not actually perform any actions that would trigger Microsoft Office Macro blocking etc, again humans outsmart technology, finding a new way of crafting code that evades detection and needs to be patched.
Rather than rewrite the seriously good details already published regarding this vulnerability, I will link to the original article on Medium, here is the Follina Zero day write up.
Follina, Zero day mitigation
Microsoft have mitigated the Follina Maldoc in its most recent Insider and Current versions of Microsoft Office (this is disputed in some circles), but as many businesses and home users are likely not on the current version they may need to perform some additional steps to protect their devices from infection.
For organizations relying on Microsoft Defender’s Attack Surface Reduction (ASR) rules, Huntress advises activating the “Block all Office applications from creating child processes” in Block mode, which would prevent Follina exploits.
Another mitigation, from Didier Stevens, would be to remove the file type association for ms-msdt so that Microsoft Office won’t be able to invoke the tool when opening a malicious Folina document.
Running the rule in Audit mode first and monitoring the results is recommended before using ASR, to make sure that end-users are not experiencing adverse effects.
Bleeping Computer
Advice is to update your Microsoft Office environment to the latest versions for 99% of your devices, as well as test those complex 10 year + super macros that keep your business operating for correct function before implementing on those 3 power users in the organisation who have the ability to still use Office Macros.
Follina maldoc conclusion
Microsoft Attack Surface Reduction (ASR), a part of Microsoft Defender for Endpoint P2 and Microsoft Defender for Business provides ASR rules, Attack surface reduction rules provide vulnerability management capabilities to an organisation, meaning that where a maldoc or other other malware might exploit a Zero day vulnerability – ASR can still ‘Save the day’ by limiting what the infected file can perform on an Endpoint.
This is another case for Defence in depth, the Zero Trust Network Architecture principles are at play here, and that is to do many things and not have all your eggs in a single basket.
I may have written about Zero Trust before with slight sarcasm as a Monty Python skit is likely to show, but in the words of Homer Simpson “Hold my beer”, I will be coming back with an updated opinion piece on the Zero Trust Network Architecture soon with a fresh and revamped opinion.
My advice is to look towards additional technologies in your security program like Application Allow listing software which can prevent applications and code running based on what should be normal operations for your business. When looking at application allow and block listing software look to solutions such as Microsoft Business Premium (Applocker) or Microsoft Defender for Business (through an indicator) – for small organisations with limited requirements or a product like “Airlock Digital” which is produced right here in Australia.
Please leave a comment in the comments section or contact us here for any assistance.





