Supply chain attacks can be a very serious issue, instead of one hacker to one client, the issue becomes one hacker to many hundreds of client businesses being affected.
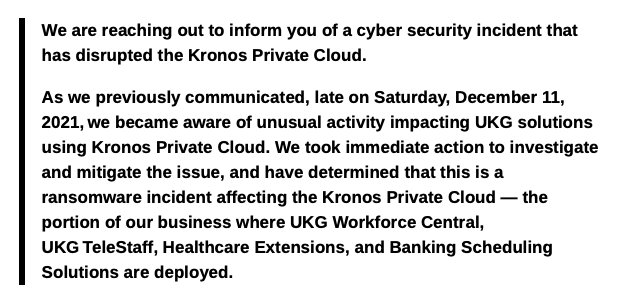
Many/most staff use the same password for work related services (Kronos) as they do for their corporate work accounts.
Therefore each Kronos customer must be forcing all users to reset their passwords immediately if they are not using federated authentication.
Kronos clients: millions of people may not be paid, can not see their scheduled work times, can not schedule annual leave etc – massive disruption.
Cost to Kronos: both financially and reputation wise, visibility to citizens is high at the worst time of the year – in addition to clients in critical industries.
Risk of this issue occurring: 100% (not a stat)
To over simplify, to mitigate this:
1. Teach your users (again) to never open any email they do not know the source of.
2. Email Security and DMARC
3. Patch your operating systems always
4. Patch your applications
5. Web security like CASB – prevent a connection back to a C2 server
6. NGAV and EDR
7. Application allow / block lists
8. Office macro blocking
9. Use Multi factor authentication always
10. Use strong passwords or go even better with Password less
11. Teach your users (again) to never open emails they do not know the source of.
If this list looks familiar, then thank you 🙂 ASD Essential 8 is your MVCS (Minimally Viable Cyber State)





