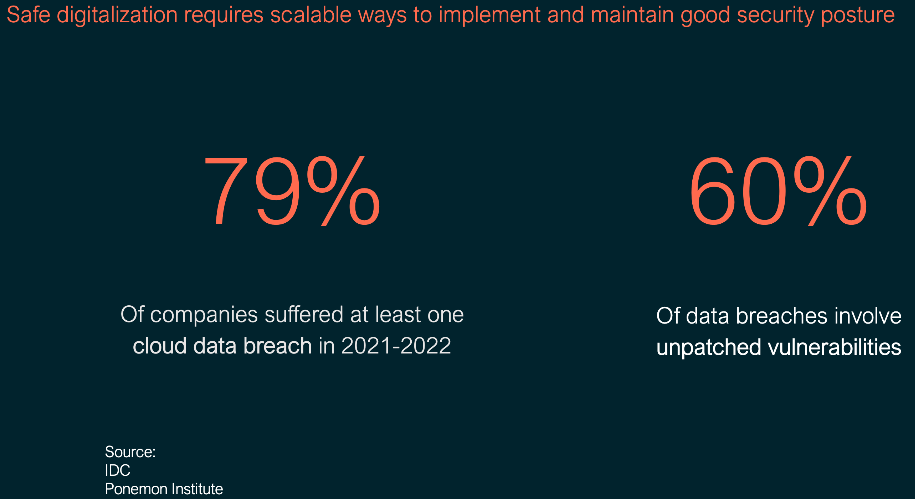
Threat and Vulnerability management, an absolutely essential part of security for your organisation. Though my dislike for statistics is known, SIXTY percent of breaches are claimed to be from unpatched software and though statistics may be guided by the authorising (paying) agency/vendor, it does not change the underlying seriousness that we all face with keeping our devices secure from breach through managing the software installed on those devices.
When determining the lowest possible cost method of managing Threat and vulnerabilities on your digital estate, look to utilise the existing licensing you may already have in your cyber security suite already.
Introduction
This post will focus on the capabilities within Microsoft Business Premium with Defender for Business or Microsoft Defender for Endpoint P2 as these licenses are included for many businesses today and a very affordable way to ensure security against vulnerabilities for your business.
M365 Business Premium (Defender for Business) and Defender for Endpoint P2 have built in Threat and Vulnerability management (assessment), a great way to improve your organisations security posture at no cost if you have the above licenses.
Using Microsoft TVM
I read an updated post this morning about a recent VMware vulnerability (CVE-2022-22954), these are easily surfaced through the Microsoft security centre as a part of your M365 tenant enabling you to patch the respective endpoint devices quickly.
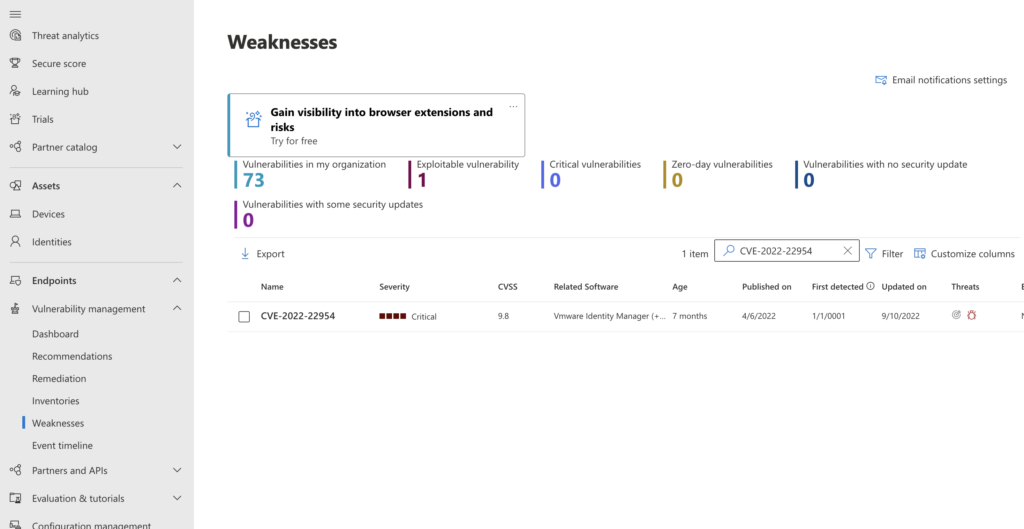
The TVM feature being exposed through security.microsoft.com is relatively new to Business Premium (must be using Defender for Business) but worth its weight in gold and another example of prevention being most critical.
Check your Microsoft security portal regularly for CVEs and other vulnerabilities that could affect your organisation.
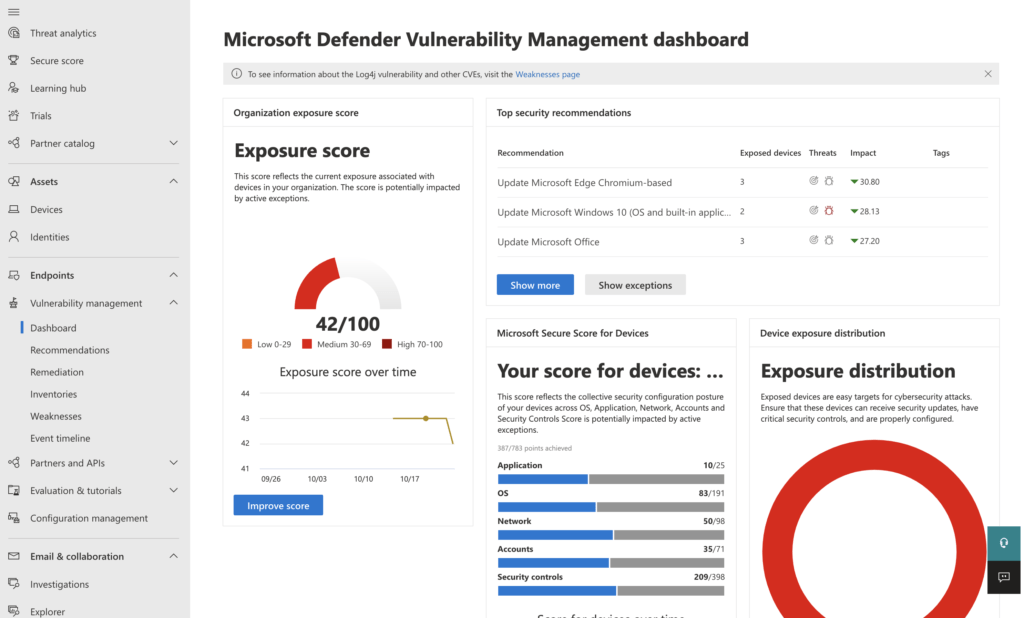
- The above image shows Michael’s demo Microsoft tenant (if you are a partner with an MPN, then access CDX for your own demo labs and much more to help your clients) and some of the vulnerabilities that Michael’s test endpoints have exposed.
Looking at the vulnerabilities listed in a priority order based on likelihood of being used in a breach is a good way to determine priority for resolving these issues.
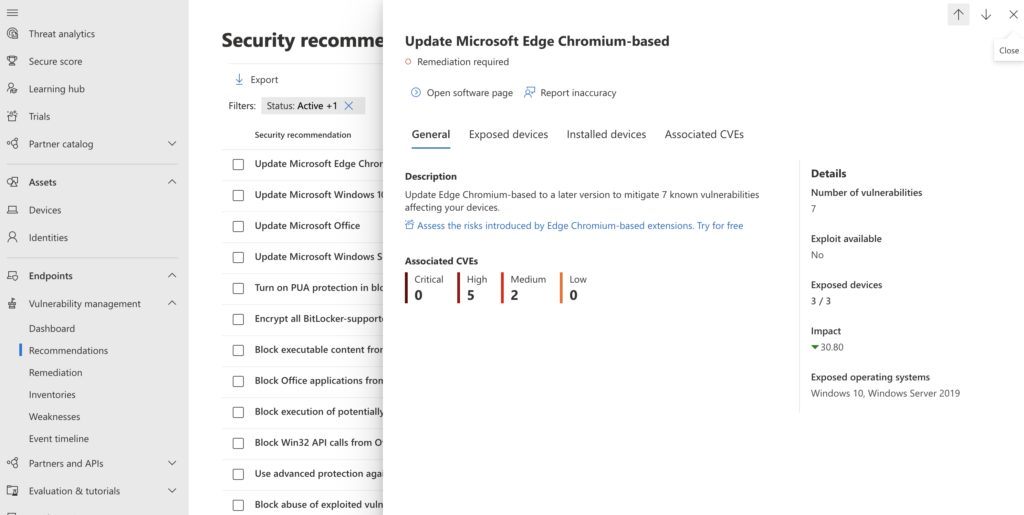
2. Opening the “Update Microsoft Edge Chromium-based” link will provide further information as well as provide a mechanism for your Microsoft Endpoint Manager Team to roll out a software update for the Edge browser and removing this Threat from your list.
In summary
Managing the many versions of software running on 100s to 1000s of endpoints (Desktop or server) and other devices is by no means as easy of straightforward as has been presented above, a small demo lab can not contain all the permutations and intricacies that even a mid sized business will face.
Your goal should be to start using the Microsoft Security centre as a daily dashboard for updating your knowledge as to what is happening across the broader industry and what CVEs and other threats and risks have been identified that may affect your business.
Use the information exposed through the Dashboards to gain and maintain an understanding of your security posture at all times.





