Eek… Disabled Entra identity user, still able to log in to their M365 Apps
Read More: Eek… Disabled Entra identity user, still able to log in to their M365 AppsEek… Disabled Entra identity, user was still able to log in to their M365 Apps
Encryption #1 – Microsoft Bitlocker, deploying via Intune, GPO or Powershell?
Read More: Encryption #1 – Microsoft Bitlocker, deploying via Intune, GPO or Powershell?Encryption #1 – Microsoft Bitlocker, deploying via Intune, GPO or Powershell? Introduction Encryption is a practise that has been in use since time immemorial, it is written in the historical record that in 600 BC encryption was being used by the Spartans as Thales introduces to us here. The reason for encrypting is fairly self…
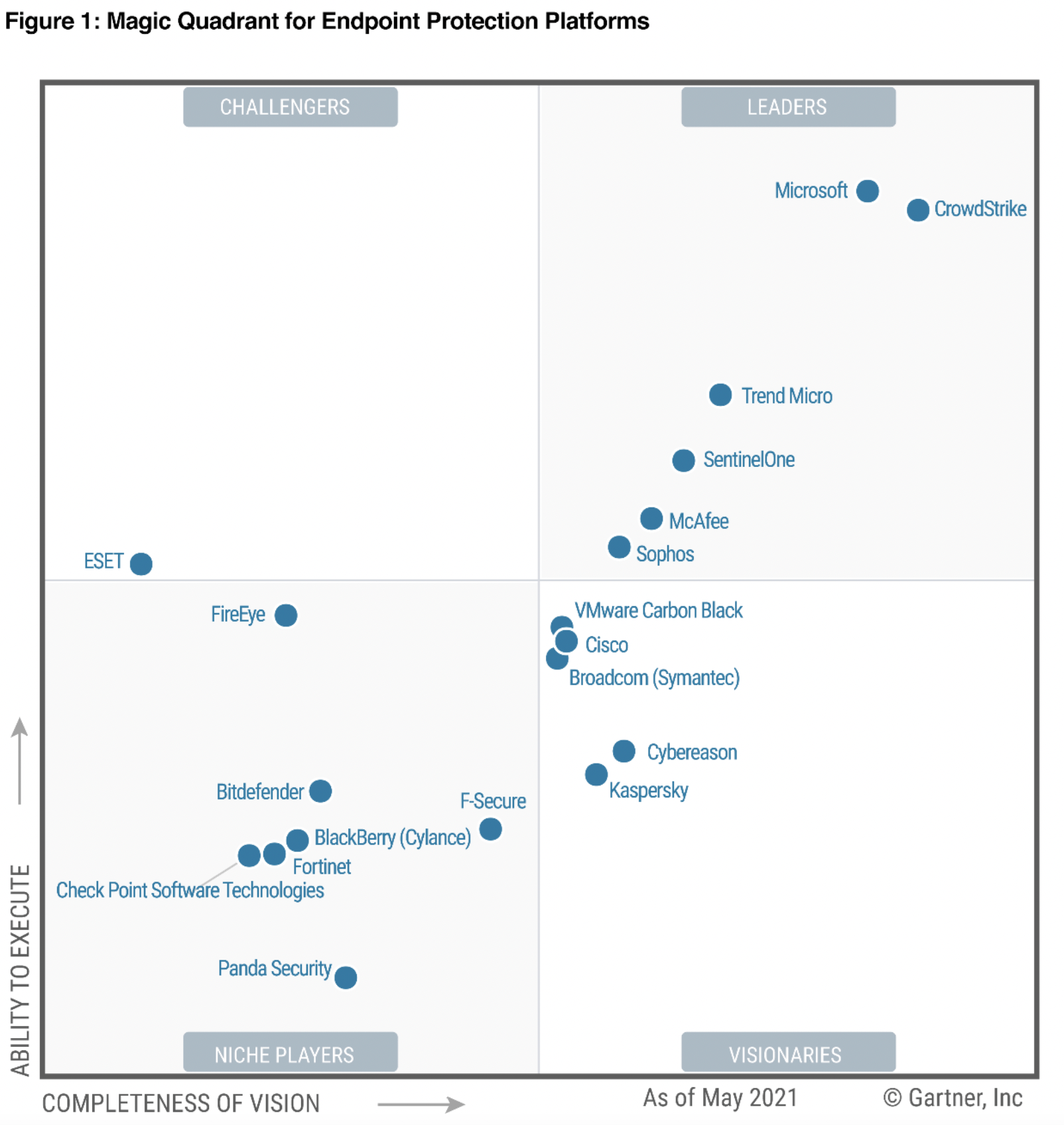
Protection before Detection – Endpoint detection response
Read More: Protection before Detection – Endpoint detection responseProtection before Detection – Endpoint detection response Endpoint Detection and response gets a lot of attention from the entire cyber security industry, EDR as it is commonly known is a valuable tool in a corporate kitbag, but is Endpoint and response something that should be acquired first, second or where? If we review the Australian…
The No.1 way to protect Data, Defender for Business and Premium
Read More: The No.1 way to protect Data, Defender for Business and PremiumThe No.1 way to protect Data, Defender for Business and Premium, MSP’s and businesses looking for better coverage of the ASD Essential 8 with the fewest possible products should look at Microsoft Defender for Business or Business Premium preferably. This morning a colleague (thanks Ross) sent me this article and it reminded me that we…
Microsoft Autopatch – Patch Tuesday is gone for good!
Read More: Microsoft Autopatch – Patch Tuesday is gone for good!Microsoft Autopatch – Patch Tuesday is gone for good! As an ex-systems administrator my life back in the good ol’ days was busy. Waiting for the next patches Testing the new patches Deploying the new patches …….. rolling back the new patches where it causes a legacy printer or other device to no longer function!…
An Empirical Assessment of Endpoint Detection and Response Systems against Advanced Persistent Threats Attack Vectors
Read More: An Empirical Assessment of Endpoint Detection and Response Systems against Advanced Persistent Threats Attack VectorsAn Empirical Assessment of Endpoint Detection and Response Systems against Advanced Persistent Threats Attack Vectors. Recently I wrote about EDR failure to detect and respond to cases of Advanced Persistent Threats here after discovering a research paper on the topic when researching the use of Machine Learning in cyber security Detection and response solutions such…
Mic
Microsoft Defender for endpoint server licensingRead More:Microsoft Defender for endpoint server licensing, Microsoft licensing is hard to follow at the best of times, not to mention product name changes/updates, licensing terms etc etc. Recently I have been involved in licensing questions for reseller and Managed Service Providers (MSP) across my region and Microsoft Defender for endpoint server licensing has come up…
Mic
Microsoft Defender for endpoint server licensingEndpoint Detection Response Assessment = Fail
Read More: Endpoint Detection Response Assessment = FailEndpoint Detection Response Assessment = Failure of virtually all current leading Endpoint detection and response solutions to detect a range of ‘known’ attack methods. Throughout this work, we went through a series of attack vectors used by advanced threat actors to infiltrate organizations. Using them, we evaluated state-of-the-art EDR solutions to assess their reactions, as…
AV NGAV EDR XDR MDR AMDR
Read More: AV NGAV EDR XDR MDR AMDRThe cyber security landscape has seen huge expansion and growth in the past 5 years and End Point Detection and Response (EDR) has been one of the biggest areas of expansion. https://www.morphisec.com/hubfs/2020%20State%20of%20Endpoint%20Security%20Final.pdf According to Ponemon Institute, 68% of organisations suffered one or more endpoint attacks that successfully compromised data or IT Infrastructure. In 2018 Gartner…
End Point Protection (epp)
CSF framework: 1. Identify; 2. Protect. Cyber Maturity Level:⭐️
Read More: End Point Protection (epp)Organisation type: All organisations need End Point Protection
CSF framework: 1. Identify; 2. Protect. Cyber Maturity Level:⭐️